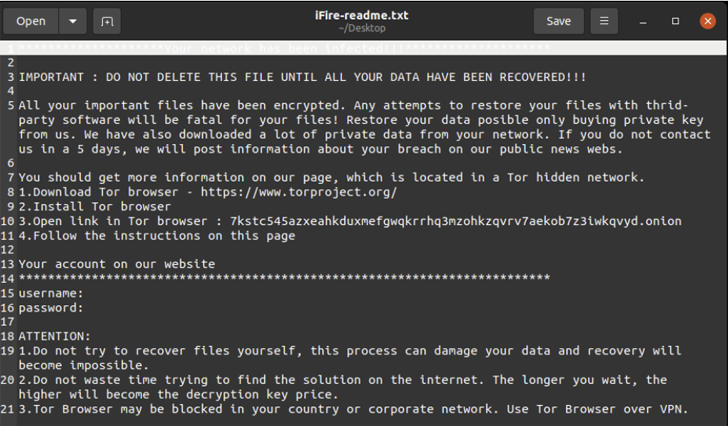
A beforehand identified Home windows-based ransomware pressure often known as IceFire has expanded its focus to focus on Linux enterprise networks belonging to a number of media and leisure sector organizations internationally.
The intrusions entail the exploitation of a not too long ago disclosed deserialization vulnerability in IBM Aspera Faspex file-sharing software program (CVE-2022-47986, CVSS rating: 9.8), in accordance with cybersecurity firm SentinelOne.
“This strategic shift is a major transfer that aligns them with different ransomware teams that additionally goal Linux programs,” Alex Delamotte, senior menace researcher at SentinelOne, mentioned in a report shared with The Hacker Information.
A majority of the assaults noticed by SentinelOne have been directed in opposition to corporations situated in Turkey, Iran, Pakistan, and the U.A.E., nations that aren’t sometimes focused by organized ransomware crews.
IceFire was first detected in March 2022 by the MalwareHunterTeam, but it surely wasn’t till August 2022 that victims had been publicized by way of its darkish net leak web site, in accordance with GuidePoint Safety, Malwarebytes, and NCC Group.
The ransomware binary focusing on Linux is a 2.18 MB 64-bit ELF file that is put in on CentOS hosts working a susceptible model of IBM Aspera Faspex file server software program.
It is also able to avoiding encrypting sure paths in order that the contaminated machine continues to be operational.
Uncover the Hidden Risks of Third-Occasion SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to study concerning the forms of permissions being granted and reduce danger.
“Compared to Home windows, Linux is harder to deploy ransomware in opposition to–significantly at scale,” Delamotte mentioned. “Many Linux programs are servers: typical an infection vectors like phishing or drive-by obtain are much less efficient. To beat this, actors flip to exploiting software vulnerabilities.”
The event comes as Fortinet FortiGuard Labs disclosed a brand new LockBit ransomware marketing campaign using “evasive tradecraft” to keep away from detection via .IMG containers that bypass Mark of The Net (MotW) protections.