Most firms have methods in place to coach workers about community safety. However there was so much much less consciousness and schooling on easy methods to scale back “phygital” dangers — that’s, bodily units that launch digital assaults towards an organization’s laptop networks.
One other identify for these phygital assaults is “warshipping.” Primarily, a malicious hacker creates an Web-enabled system — for instance, a miniature laptop — and sends it by means of bodily mail in an try and compromise an organization’s laptop community. What’s extra, as a result of so many workers have but to return to their bodily workplaces post-lockdown, these units can simply sit for months unattended in unopened mail on desks and in mailrooms, gathering information and exploiting vulnerabilities in an organization’s community.
It is frighteningly straightforward and cheap to make your individual DIY model of a warshipping system. With simply three hours, a few hundred {dollars}, and some YouTube movies, almost anybody can do it. To point out you precisely how straightforward it’s, I’ll discuss how I constructed a warshipping system after which talk about what you are able to do to guard your organization towards these assaults.
Constructing a Warshipping Gadget
Put together yourselves for a little bit of a technical leap into {hardware} and software program. We do not have the area right here to enter each facet of constructing a warshipping system, however the next ought to provide you with a harrowing sense of precisely how straightforward and cheap the method might be.
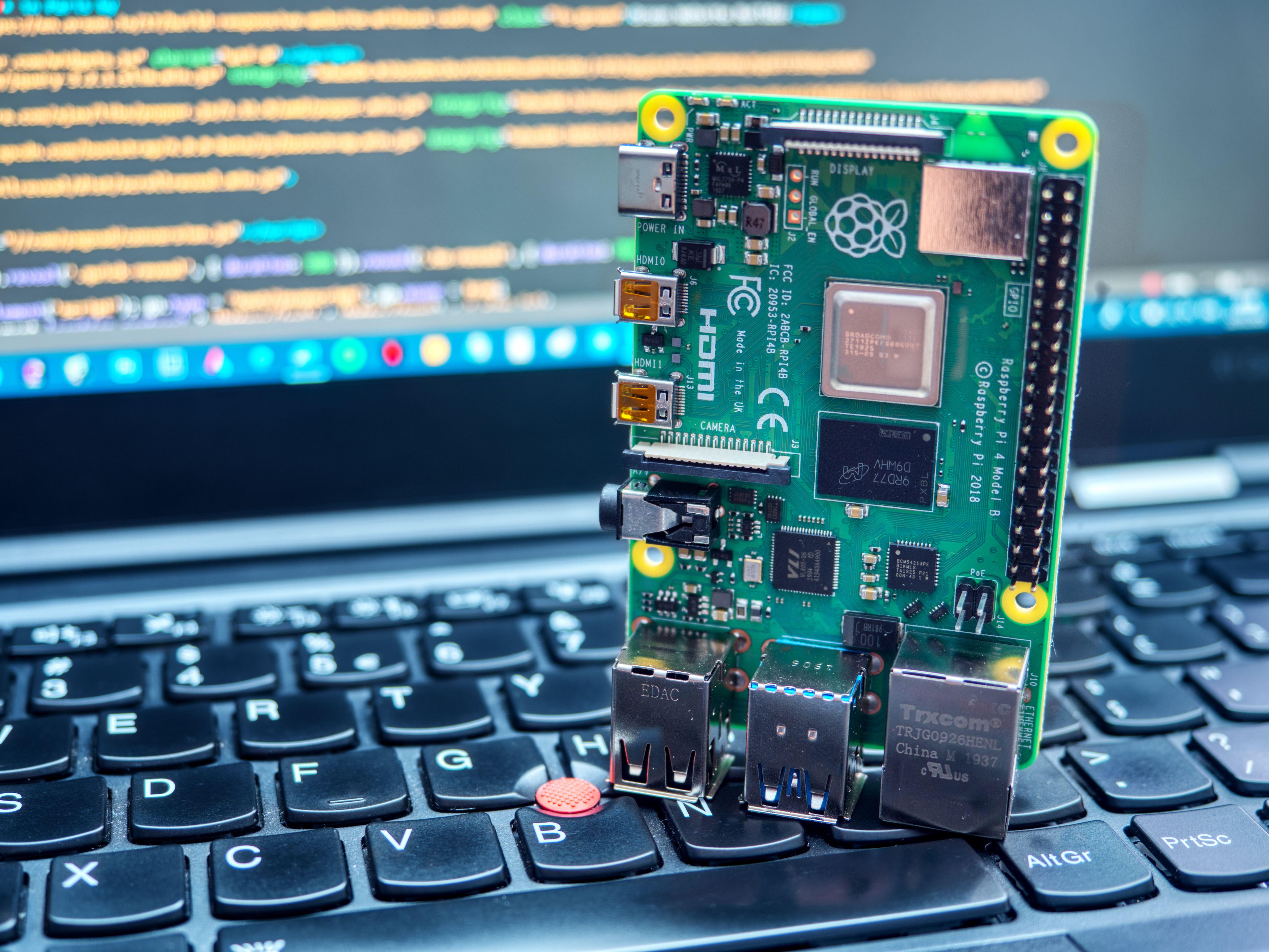
Constructing {hardware}. The muse of any warshipping system is so simple as a hobbyist circuit board not a lot greater than a bank card, which might function like a miniature laptop. One instance is a Raspberry Pi, which is definitely discovered on-line and arrives with the required software program, or no less than software program that will also be simply discovered on-line.
Subsequent you want a Wi-Fi dongle of some variety so your warshipping system can hook up with the Web wirelessly. A USB Wi-Fi adapter and a reminiscence card with no less than 32 GBs of storage, together with a SIM card to allow a mobile connection and optionally available GPS system, will full the {hardware} necessities.
Software program conditions. Raspberry Pis have their very own Ubuntu-based working system (OS) known as Raspberry Pi OS.
Subsequent you will want to determine distant entry. It is advisable discover your system’s IP deal with so you’ll be able to hook up with it by means of your laptop or one other system. To try this, you’ll be able to run a scan in your native community or use a smartphone app. Subsequent enter the default password for a Raspberry Pi, which is “raspberry.” You now have a useful warshipping system.
Prepared for warshipping. Ultimately you’ll be able to set up your software program for warshipping. Your precise warshipping software program is available in two elements: your optionally available GPS software program if you wish to hold observe of your system location and Kismet or a related network-detecting software program.
Kismet acts as a packet sniffer, which finds and captures packets of information from a community to retailer or ahead that info. So Kismet can probably be used to seize information out of your community.
Your system is now able to trigger a world of ache for some poor IT group. All you must do is ship it within the mail, and when it arrives you’ll be able to entry delicate information or discover a weak entry level for an assault through the mobile connection. Then you can be part of the realm of malicious hackers who’re costing firms worldwide $2.9 million each minute as a consequence of cybercrime.
Key Takeaways
So what are some helpful takeaways from all of this?
First, it is advisable notice that this risk is not going away. These assaults are just too straightforward to launch and too onerous to deal with. In any case, who has the time to type by means of all of that incoming mail as quickly because it arrives?
Second, it is advisable develop phygital safety measures as a part of your total cybersecurity efforts. Packages can sit in mailrooms for weeks — or nowadays, months — earlier than somebody processes them. Any of these packages may comprise a warshipping system that may use their idle time gathering information out of your community. As a result of warshipping units might be sufficiently small to suit between two items of cardboard, even an opened empty field you are saving within the mailroom to be reused at a later date might be a risk.
To handle the problem, you can begin by instantly processing packages which might be incorrectly addressed, since these will get returned to the sender. However you need to transcend that to course of all unopened mail as shortly as doable and by no means retain used packaging supplies within the mailroom. You may also look into the most recent mail-scanning know-how, which might detect these units whereas avoiding the dangerous results of X-rays.
Third, community discovery software program may also help you decide up on uncommon visitors and detect any new units the minute they hook up with your community. Meaning you’ll be able to probably detect a warshipping system earlier than any injury is completed. As well as, the wave of layoffs within the current Nice Resignation, insider threats from people who’re or previously had been approved customers in your community are simply as frequent and could also be more durable to detect, since these folks could have entry to accepted credentials and units.
Fourth, educate your workers. They doubtless don’t know that packages they left on their desks for just a few days whereas they had been working remotely may have a warshipping system inside, so do them and yourselves a favor by alerting them to the doable risk.
If there’s one factor you’ve got discovered from this text, it needs to be that the phygital world is a harmful place. However simply understanding in regards to the hazard is half the battle. So now you understand.