Vital infrastructure is necessary for societal existence, development, and improvement. Societies are reliant on the companies supplied by crucial infrastructure sectors like telecommunication, vitality, healthcare, transportation, and data expertise. Security and safety are vital for the optimum operation of those crucial infrastructures. Vital infrastructure is made up of digital and non-digital property. Organizations should keep forward of cybersecurity threats to stop failures brought on by cyber assaults on crucial infrastructure. Discovering methods to guard digital property in an ever-changing panorama full of threats is a steady exercise. Organizations should additionally make use of environment friendly safety options and finest practices to remain protected and scale back the possibilities of compromise.
Safety options assist safe and enhance the visibility of a corporation’s risk panorama. Totally different options use totally different ideas and approaches. An necessary idea that has risen not too long ago is Prolonged Detection and Response (XDR).
XDR options present detection and response capabilities throughout a number of layers. XDR instruments correlate knowledge utilizing risk detection and response strategies by gathering logs and occasions from varied sources, similar to community units, servers, and purposes. These capabilities make it attainable for safety groups to rapidly detect, examine and reply to incidents.
Assaults on crucial infrastructure
In February 2022, a provide chain assault occurred in one in all Germany’s vitality giants. This assault led to the closure of greater than 200 fuel stations throughout Germany, affecting lives and companies. This occasion occurred practically a yr after the Colonial Pipeline assault in the US of America, the place knowledge exfiltration occurred and a ransomware an infection shut down digital companies inside their infrastructure for days. An article from the NYTimes reported that an estimated 5 million {dollars} had been paid to the hackers concerned within the Colonial Pipeline ransomware assault. The hackers within the Colonial Pipeline case had been in a position to achieve entry utilizing a compromised VPN password, and so they proceeded to carry out intrusion actions for a complete day earlier than they had been detected.
There are a number of entry factors for assaults on crucial infrastructure, and a few vectors are extra prevalent than others. These vectors embody compromised credentials, unpatched working methods, susceptible purposes, and malware delivered by varied strategies.
Emphasis must be positioned on securing crucial infrastructure earlier than an assault occurs, no matter the way it originates. Safety options assist organizations defend themselves from totally different assault vectors. These options embody XDR, SIEM, code scanners, infrastructure analyzers, vulnerability scanners, and malware detection options. Along with these options are compliance requirements. A number of really useful requirements are NIST, PCI DSS, HIPAA, and GDPR. The proper utility of those options and compliance requirements may help enhance a corporation’s safety posture.
How XDR can mitigate assaults
An XDR performs a major function in conditions the place risk actors goal totally different digital property of a corporation. With an XDR built-in into a corporation’s infrastructure, safety occasions from varied sources and property are analyzed and correlated to find out what actions are occurring within the infrastructure. An XDR has the flexibility to detect and supply automated responses to malicious actions in an surroundings. Such a response can kill a malicious course of, delete a malicious file, or isolate a compromised endpoint. Because the responses are executed in close to real-time, velocity performs a crucial function within the execution of those duties.
Wazuh SIEM/XDR
Wazuh is a free and open supply SIEM and XDR platform. It consists of a number of elements that defend each cloud and on-premises workloads. The Wazuh platform operates with an agent-server mannequin. The Wazuh central elements (server, indexer, and dashboard) analyze safety knowledge from endpoints in your infrastructure. On the similar time, the Wazuh agent is deployed on endpoints to gather safety knowledge and supply risk detection and response. The Wazuh agent is light-weight and helps a number of platforms. Wazuh additionally helps agentless monitoring on routers, firewalls, and switches.
Wazuh XDR capabilities
Wazuh has a number of capabilities that assist a corporation keep forward of safety threats. A few of these capabilities are malware detection, vulnerability detection, file integrity monitoring, and automatic response to threats, amongst others. The next sections include extra particulars on Wazuh capabilities that assist in defending crucial infrastructure.
Log knowledge evaluation
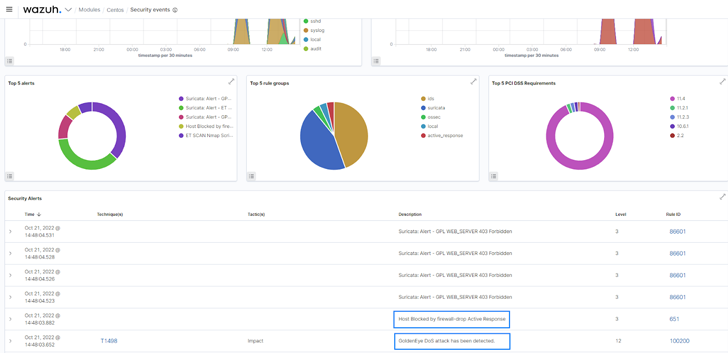
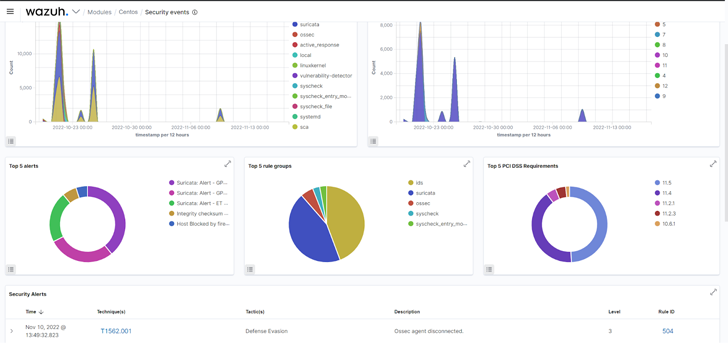
The Wazuh log knowledge evaluation module collects and analyzes safety knowledge from varied sources. Such knowledge embody system occasion logs, utility logs, and irregular system habits logs. Consequently, the analyzed knowledge is used for risk detection and automatic response. This functionality offers you visibility into occasions occurring at totally different endpoints in your infrastructure.
 |
| Fig 1: Safety occasions of a monitored endpoint on the Wazuh dashboard. |
Malware detection
Wazuh has a number of options that assist in malware detection. As well as, Wazuh might be built-in with different safety instruments like YARA and VirusTotal to detect malware. By correctly configuring Wazuh Fixed Database (CDB) lists, values from decoded alerts similar to customers, file hashes, IP addresses, or domains might be in contrast with malicious data. Here’s a weblog put up that exhibits how Wazuh might be built-in with CDB lists for detecting and responding to malicious recordsdata. This Wazuh functionality helps you detect malware on varied monitored endpoints.
File integrity monitoring
The Wazuh File Integrity Monitoring (FIM) module displays an endpoint filesystem to detect adjustments in predefined recordsdata and directories. Alerts are triggered when a file is created, modified, or deleted in monitored directories. You possibly can see how this module is utilized to detect adjustments to an SSH key file within the weblog put up Detecting illegitimate crypto miners on Linux endpoints. Utilizing the Wazuh FIM module, you possibly can detect adjustments to configuration recordsdata on crucial methods and decide if the exercise is permitted or malicious.
Vulnerability detection
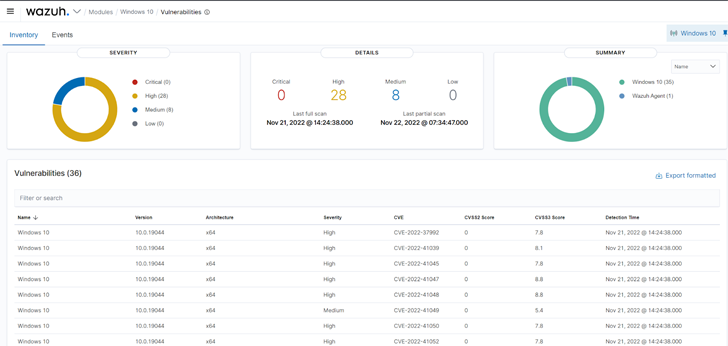
Wazuh makes use of the Vulnerability detector module to search out vulnerabilities on a monitored endpoint. Vulnerability detection works by performing software program audits. These audits are made attainable by leveraging vulnerability feeds listed from sources like Canonical, Debian, Pink Hat, Arch Linux, ALAS (Amazon Linux Advisories Safety), Microsoft, and the Nationwide Vulnerability Database. These feeds are cross-correlated by Wazuh with data from the endpoint’s utility stock. Directors ought to start remediation instantly after vulnerabilities are detected earlier than malicious actors can exploit them.
Automated response to threats
The Wazuh energetic response module might be configured to routinely execute countermeasures when occasions match particular standards. It will probably execute user-defined actions, similar to a firewall block or drop, visitors shaping or throttling, account lockout, system shutdown, and so forth. The energetic response module was configured to disclaim community connection from an recognized malicious supply within the weblog put up Responding to community assaults with Suricata and Wazuh XDR.
Conclusion
Implementing safety throughout a number of layers of crucial infrastructure reduces a corporation’s assault floor. We have now emphasised a number of components to remember to keep up a correct safety posture. In defending your digital property, we recommend an answer that works properly with varied endpoints, methods, and applied sciences.
Wazuh is a free and open supply XDR resolution. It consists of the capabilities vital to find vulnerabilities, decide the system configuration state, and reply to threats in your digital property. Wazuh additionally gives help for compliance requirements like PCI DSS, HIPAA, NIST, and GDPR. Wazuh has an ever-growing group the place help is supplied to customers. Take a look at the Wazuh documentation for extra data.