Deep fakes are anticipated to develop into a extra distinguished assault vector. Here is determine them.
What are Deep Fakes?
A deep faux is the act of maliciously changing actual photographs and movies with fabricated ones to carry out info manipulation. To create photographs, video and audio which can be top quality sufficient for use in deep fakes, AI and ML are required. Such use of AI, ML and picture alternative are in contrast to different varieties of info manipulation, which use much less excessive manipulation strategies, like misrepresentation of knowledge, isolating elements of the data or enhancing it in a misleading method. Etay Maor, Senior Director of Safety Technique at Cato Networks provides “So as to add problems, the latest developments and accessibility to AI generated textual content, similar to GPT3, have already been utilized in mixture with deepfakes (as a proof of idea) to create interactive, human wanting dialog bots”
What Do Deep Fakes Look Like?
Deep fakes are available all sizes and styles. Some are easier and a few are extra superior. A few of the hottest examples of deep fakes are:
Face Swap
Face swapping is the act of changing the face in a video or picture from one individual to a different. Face swapping requires devoted software program, but it surely doesn’t need to be primarily based on superior know-how – at the moment one may even discover cellular apps that assist face swapping. Face swapping that’s out there in cellular apps is often restricted to easy use circumstances, like swapping between the consumer’s photographs and actors’ faces in film scenes.
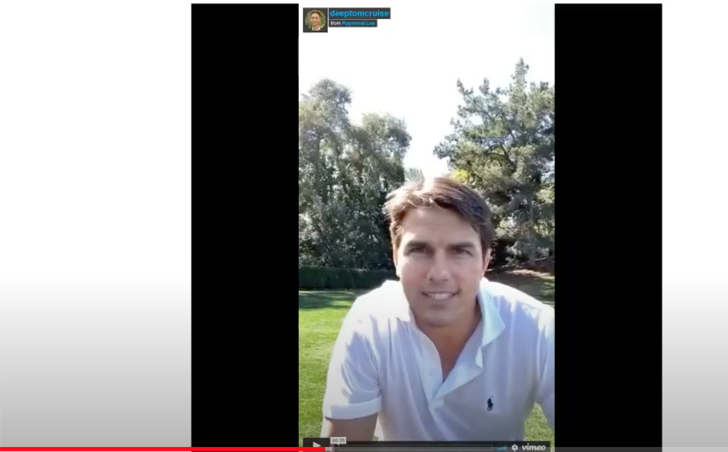
Extra superior face swapping does exist, but it surely requires extra mannequin coaching and code, and – consequently – GPUs, which is pricey and resource-intensive. An instance of a extra superior face swapping deep faux will be see on this video, by which Tom Cruise is swapped with the presenter’s face:
This Tom Cruise face swap required two hours of coaching on a GPU in addition to days {of professional} video enhancing post-processing. This would possibly sound like so much, but it surely was additionally thought-about a less complicated swap than others, as a result of the presenter had an analogous haircut to Cruise and might impersonate his voice, which implies much less coaching and post-processing had been required.
Puppet Grasp (Lip Sync)
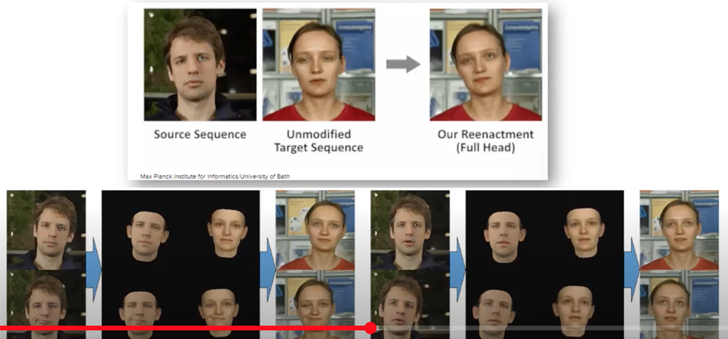
The ‘Puppet Grasp’ deep faux is a method by which the picture of an individual’s mouth actions are manipulated, making it seem to be the individual is saying one thing they have not really mentioned. In comparison with face swapping, which trains a mannequin on the brand new, swapped face, ‘Puppet Grasp’ trains a mannequin on the face of the unique picture, and particularly on the mouth actions.
Here is what it appears like:
[warning – explicit language]
The know-how behind the ‘Puppet Grasp’ relies on synthesizing the masks, i.e. the unique picture, and putting it on prime of the mannequin of the one who is impersonating and lip syncing them.
Audio
The third distinguished sort of deep faux is audio-based. Audio deep fakes are audio recordsdata that take an actual individual’s voice and make it appears like they’re saying one thing they’d by no means mentioned. Audio deep fakes are created by taking audio recordsdata, allocating annotations to the sounds, coaching an ML mannequin primarily based on the annotations to affiliate sounds with textual content after which producing a brand new audio file.
Here is what’s appears like:
Deep Fakes vs. Low-cost Fixes
Not all modified photographs or audio are deep fakes. Whereas deep fakes are media synthesized or modified utilizing AI, low cost fixes are media synthesized or modified utilizing low-tech strategies, that are simple to identify. They usually have distortions and have been clearly manipulated. Here is what an affordable repair appears like:
The Cyber Danger of Deep Fakes
Deep fakes have develop into extra practical and accessible and they’re additionally sooner to create than ever earlier than. This makes them a robust instrument for weaponization. Consequently, they pose a danger for companies and for nations. They can be utilized for cyber crime, social engineering, fraud, by risk actor nations to affect international operations, and extra.
For instance, deep faux was used to imitate a CEO’s voice and persuade an govt to wire $243,000 to a rip-off account. Etay Maor of Cato Networks “Enterprise e mail comprise and phishing assaults have gotten more durable and more durable to detect primarily based on easy evaluation of the language used. There’s a want for a holistic method, such because the one provided by a single vendor SASE resolution, that may detect the assault at completely different a number of choke factors and never depend on remoted level merchandise which can be doomed to fail”. In one other case, a deep faux was introduced as proof in a baby custody case.
Deep fakes may also be used for spreading disinformation, i.e false distribution of knowledge to affect public opinion or obscure the reality. For instance, deep fakes might be used to impersonate world leaders and ignite an assault, or to impersonate a CEO and manipulate an organization’s inventory worth. In different circumstances, deep fakes allow believable deniability, by which folks may deny all sources of media by claiming they’re deep fakes, which creates a social breach of belief.
Lastly, deep faux can be utilized for defamation, i.e damaging somebody’s good status. For instance, by creating revenge porn.
Find out how to Detect Deep Fakes
There are two foremost varieties of strategies for precisely detecting deep fakes:
- Low-level detection strategies
- Excessive-level detection strategies
Low-level Detection Strategies
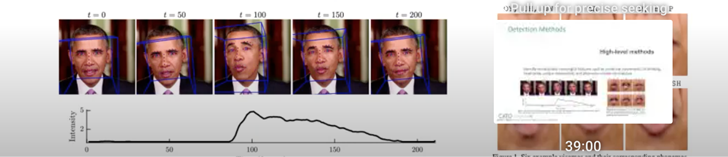
Low-level detection strategies depend on ML fashions which can be skilled to determine artifacts or pixellations that had been launched by way of the deep faux era course of. These artifacts could also be imperceptible to the human eye, however the fashions, which had been skilled on actual photographs and deep faux photographs, are in a position to detect them.
Excessive-level Detection Strategies
Excessive-level detection strategies use fashions that may determine semantically significant options. These embody unnatural actions, like blinking, head-pose or distinctive mannerisms, and phoneme-viseme mismatches.
In the present day, these detection strategies are thought-about correct. Nevertheless, as deep faux know-how improves and turns into extra refined, they’re anticipated to develop into much less efficient and can should be up to date and improved. Along with these strategies, every one in all us may also help detect deep fakes by verifying the media supply of movies and pictures we obtain.
To be taught extra about several types of cybersecurity assaults and forestall them, Cato Networks’ Cyber Safety Masterclass collection is obtainable on your viewing.