Social engineering is a strong technique for hackers to use laptop techniques with out using malware or laptop hacking instruments. To hold out a profitable social engineering hack, moral hackers want to know the way to successfully use social media and human interplay to acquire delicate info. Social engineering is an important talent for safety consultants, particularly these within the IT area, because it’s utilized in just about each section of a cybersecurity venture.
The abilities required by moral hackers make it attainable for somebody with none data of computer systems or coding strategies to hold out critical cybersecurity duties equivalent to breaking into a corporation’s system undetected utilizing social engineering techniques alone. That stated, it can be crucial to not count on an excessive amount of from unqualified moral hackers who possess little data of correct laptop safety procedures and practices since their abilities are not any match for malicious hackers who will all the time defeat them ultimately through malware assaults or different types of cybercrime exercise.
Social engineering is primarily used to entry private accounts like emails and social media accounts like Fb or to collect private knowledge. The hackers produce phishing pages that appear very very like official ones and try and persuade the sufferer that they’re official and reliable. For extra info:
Instance of a Social Engineering Assault:
The constructing of false phishing pages is the most common illustration of a social engineering assault.
As a way to get the sufferer to imagine they’re official and reliable, the hacker first produces a phony phishing web page that appears remarkably like the actual one. The hacker then sends the sufferer the hyperlink through e-mail or SMS and poses a risk, equivalent to “Click on on the hyperlink and login or your account shall be banned/deleted,” and when the sufferer clicks on the hyperlink, he’s taken to a faux phishing web page that tips them into pondering they clicked on the official login web page after which requests their login credentials, which the hacker then retrieves with the intention to entry the sufferer’s account. In consequence, the hacker gained entry to the account shortly and efficiently.
Setoolkit:
It’s an open-source, free toolkit that’s employed in social engineering assaults like phishing and bulk emailing. Programmer Dave Kennedy created and created the Social Engineering Toolkit. Safety consultants and penetration testers use this software to search for cybersecurity vulnerabilities in techniques all around the world. Toolkit for social engineering targets to make use of offensive strategies on their computer systems. It accommodates a wide range of instruments that can be utilized to study extra about phishing victims, amongst different issues.
For extra info: Social Engineering Toolkit
Sensible Demonstration:
1. Open Kali Linux
2. Open the terminal and kind the next command to open setoolkit.
setoolkit

3. Choose Social Engineering Assaults
1
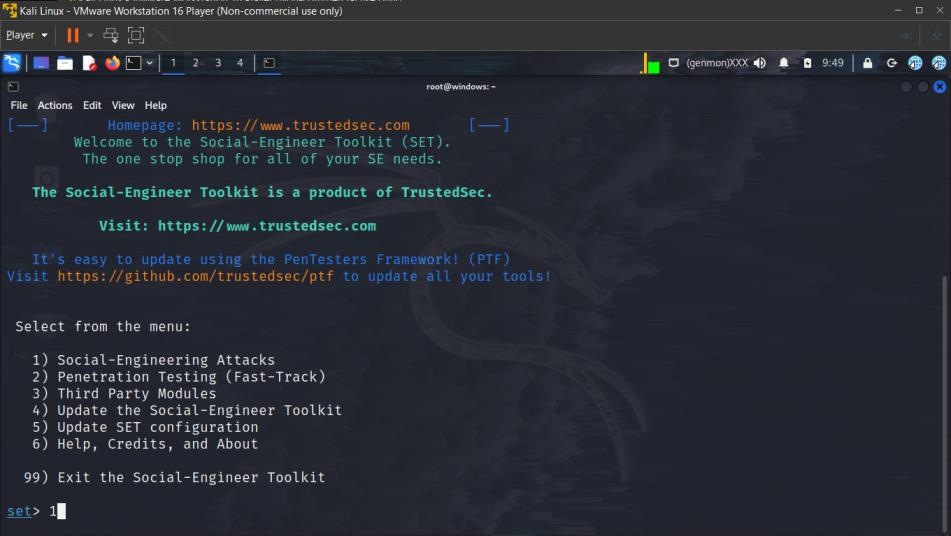
4. Choose Internet Assault Vectors
2
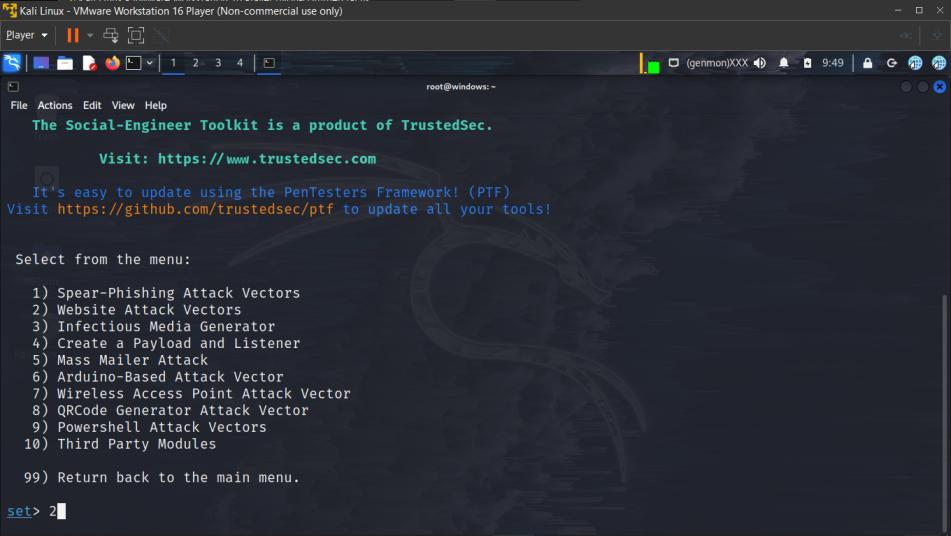
5. Choose Credential Harvester Assault
3

6. Choose Web site Cloner
2

7. Sort your IP deal with.
Notice: To carry out this assault over WAN you’ll must enter your public/exterior IP deal with. To carry out over LAN kind your inside IP deal with offered by your router. To seek out your IP deal with kind ifconfig in new terminal home windows and replica your IP deal with.
ifconfig

8. Now enter the URL you need to clone and carry out a phishing assault over (on this case Fb)
https://fb.com/

The method will full in a few seconds after which the phishing web site shall be hosted on the desired IP deal with on port 80 (principally).
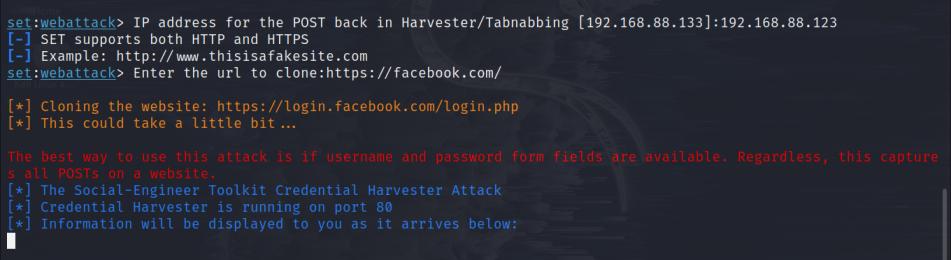
Now open the web site on different gadget with the IP.
Notice: Be sure to are related to similar community in case of LAN

A Fb Login web page is displayed which appears to be legit.

Because the person enters the e-mail ID and password it’s fetched by setoolkit

The password and e-mail id entered by the sufferer is efficiently fetched by the Hacker (highlighted in pink).

The credentials are saved in an XML file to examine over them later, to entry it open this file location
/root/.set/studies
Now open the one XML file and findthe e-mail and password parameter.

To make the hyperlink extra convincing, hackers masks the URL with interesting phrases and phrases with instruments like Maskphish (take a look at: Maskphish)
Countermeasures:
- Test the web accounts incessantly for any unusual exercise.
- Incessantly altering passwords
- Maintaining a watch on the Login exercise carefully.
- Keep away from clicking any suspicious or surprising hyperlinks, together with these from pals or family, because it’s attainable that they’ve additionally had their accounts hacked.
- Putting in phishing safety software program.
- Not accepting requests from strangers.
- Keep away from sharing any delicate info on social media as doing so might get you in hassle.
- Discover ways to spot a phishing try by studying and understanding the e-mail message you obtain earlier than you click on any hyperlinks or obtain an attachment.
Notice: This text is barely written for academic functions.


