On April 18, 2022, a handful of US residents scrambled to get their taxes filed. Whereas tax season is often a stressor, think about that these filers bought some unsolicited assist. Think about that one way or the other, strangers which may resemble angels simply appeared of their lives, providing steering and assist to work with them via this course of … all via the pc display.
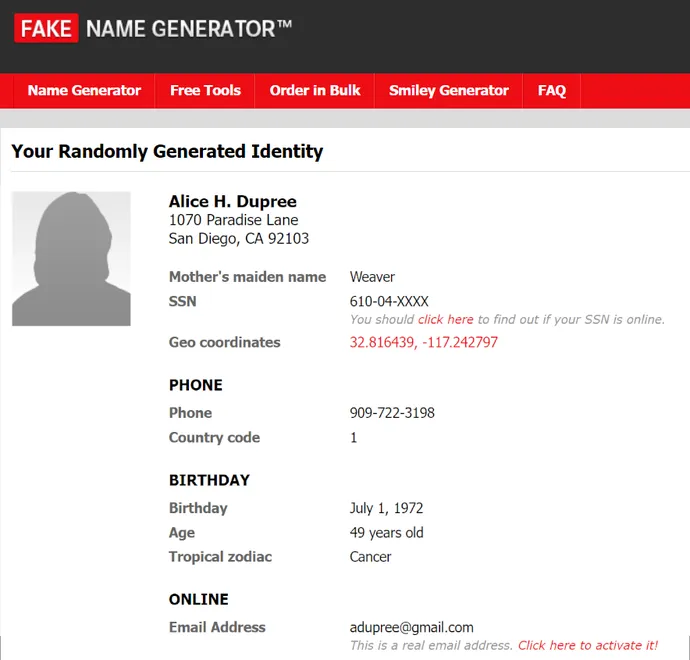
For our story, let’s think about we obtain a benign LinkedIn message from “Alice Dupree,” stating that she is a liaison with H&R Block and is reaching out to supply any help in submitting taxes. If we study Alice’s profile, the whole lot talked about strains up along with her public presence. The truth is, she seems like a really respected individual! She attended a prestigious college, has had a prolific profession, and has an attractive skilled abstract.
Whereas we might evaluate her schooling and previous work expertise along with her LinkedIn profile, there’s definitely different demographic, geographic, or private data that we wouldn’t see on-line. So let’s speak about Alice on a extra private stage.
She is 49 years previous, she lives in San Diego, California, and her favourite coloration is black (to match the enterprise fits she wears). On high of that, she was born on July 1, 1972, and her zodiac signal is Most cancers. She drives a 2005 Lexus LS to go to her mom (maiden title “Weaver”), and in case you ever want to succeed in her, her cellphone quantity is 909-722-3198.
She has an O+ blood kind and has a Mastercard that expires in February 2025. Alice owns an iPhone, however when she is on her laptop, she makes use of the Firefox Net browser.
We by no means would have the necessity for that data, or ask any questions pertaining to it — but when we did, Alice would have all of the solutions. It’s her life story, in any case!
You could be questioning how I do know a lot about Alice. Properly, that is as a result of I made her up.
Alice would not exist, and all her background data has been randomly laptop generated to make her character all of the extra convincing. Her total persona was artificially created with free, publicly accessible on-line instruments that anybody can use.
Faking Individuals (For Actual)
It’s surprisingly simple to provide you with an entire identification for a pretend individual at the moment. In all actuality, there are on-line instruments that do all of the arduous give you the results you want. Social engineering is simply too simple for scammers and cybercriminals.
Perpetrators can use Faux Identify Generator to quickly create a complete persona for pretend however plausible characters — identical to I did with Alice Dupree.
As soon as all this background data has been generated and provided for a budding scammer, they merely want a plausible profile image to exchange the default grey silhouette.
If it wasn’t already simple sufficient, cybercriminals and scammers can’t solely generate a complete individual’s historical past, but in addition their look with one other on-line device like This Particular person Does Not Exist.
How Can You Inform What Is Actual?
Possibly an observant eye would possibly discover a number of telltales that this Alice character is a randomly generated persona. The profile image gained from This Particular person Does Not Exist may need the strongest indicators:
- The individual’s gaze is immediately into the digital camera.
- They may have odd or uncommon traits.
- Equipment like hats or glasses and even hair strands would possibly fade out and in.
- The facet edges background could have very unusual figures.
You’ll have seen our so-called Alice is carrying earrings, however the left seems a bit extra distorted than the correct.

However how can somebody defend towards falling for Web scams like this? Each time attainable, if a person can do their due diligence by reaching out to the alleged firm or college this persona is/was part of, they’ll decide if that is official.
Analyzing their profile may additionally reveal that the account has little to no exercise. Social media websites could prune or take away accounts with little to no exercise, wherein case scammers really want to spend time to maintain up the charade and look as lifelike as attainable.
If there’s any suspicion you acquired a message from a pretend persona, it’s price performing some on-line analysis to find out if this individual is who they are saying they’re – or in the event that they exist in any respect.
For some semblance of “coaching your eyes” to detect pretend computer-generated profile photos, try Which Face Is Actual. Keep in mind a number of the indicators mentioned: centered eyes, blurry backgrounds, fading glasses or hair strands, and mismatched earrings. When lies and cons are at your door, inbox, or direct messages, you are the entrance line of protection.


