The latest menace actor to utilize this system is TA453, an Iranian menace group also referred to as “Charming Kitten.” Proofpoint’s analysis signifies that this group works to help the pursuits of the Islamic Revolutionary Guard Corps (IRGC). TA453 largely targets teachers, policymakers, diplomats, journalists, and human rights advocates. The menace actor conducts phishing assaults by corresponding with its targets below the guise of a journalist, educational, or different particular person within the work of the targets.
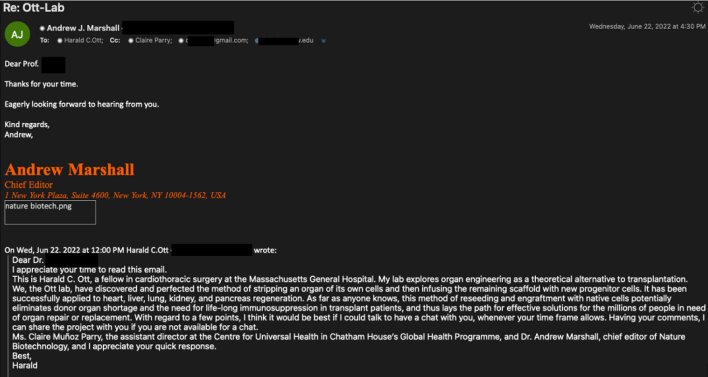
The assault started with an e mail despatched by “Harald Ott” asking for suggestions on a challenge associated to the goal’s subject of analysis. This primary e mail recognized and cc’d two different personas by the names of “Clair Parry” and “Andrew Marshall.” “Andrew” then adopted up the primary e mail by preemptively thanking the goal for his time and expressing eagerness to listen to again from the goal. “Harald,” “Andrew,” and “Claire” are all personas managed by the menace actor, however their manufactured correspondence lends the looks of legitimacy to the e-mail chain.
The goal ultimately replied to the e-mail chain, prompting “Harald” to ship an extra e mail linking to a Phrase doc titled “Ott-Lab 371.docx. This phrase doc downloads a macro enabled template containing three completely different macros. These macros gather and exfiltrate person and machine info, together with the person’s IP handle and an inventory of working processes. These macros don’t seem to carry out any extra malicious actions, so they could be supposed for reconnaissance, with the menace actor planning to conduct additional assaults later primarily based on the software program recognized on victims’ machines. The malicious payload apart, this assault demonstrates that phishing assaults can come within the type of an energetic e mail chain containing a number of correspondents, making it tougher for customers to establish assaults as such earlier than it’s too late.
Prime picture courtesy of Alex Brown


