Macros could be extremely helpful instruments in Microsoft Workplace. Most Microsoft Workplace macros use Visible Primary for Functions (VBA) or Excel 4.0 macros (XLM). These programming and macro languages have a shocking quantity of entry to system assets on Home windows machines, particularly contemplating they solely run from inside Microsoft Workplace. The profit to those macros is to simplify advanced performance, akin to automation in Microsoft Excel or area validation in kinds which will have been built-in right into a Microsoft Phrase doc, to call just a few.
Regardless of their usefulness, nevertheless, macros are sometimes used to deploy malware as properly, as a result of they’re able to downloading and executing exterior software program. As a result of most Workplace purposes can combine with one another, a macro can seize your Handle ebook from Outlook, for instance, and permit no matter malware you will have been contaminated to ship malicious payloads to your contacts. Microsoft’s dominance within the productiveness and working programs areas has made their software program wealthy targets for a really very long time, with the angle of assault usually deliver macros.
Microsoft not too long ago issued a patch to most newer variations of Microsoft Workplace disabling macros if the Workplace file being opened was flagged as ” downloaded from the web.” Initially the flag was automated and turned on in all places for all customers. Nevertheless, many small enterprise customers who depend on macros requested Microsoft to carry off on such broad sweeping adjustments, and so the patch was rolled again, sadly with out a lot discover. Right now system directors have the power to have the safety flag for on-line macro detection turned on as a Group Coverage, nevertheless it’s not on for everybody by default. As such, macros can nonetheless be an assault vector, nevertheless, in keeping with a latest report by cybersecurity agency Proofpoint, malware and risk actors are looking for new assault vectors which will circumvent Microsoft’s stricter safety insurance policies as they relate to macros.
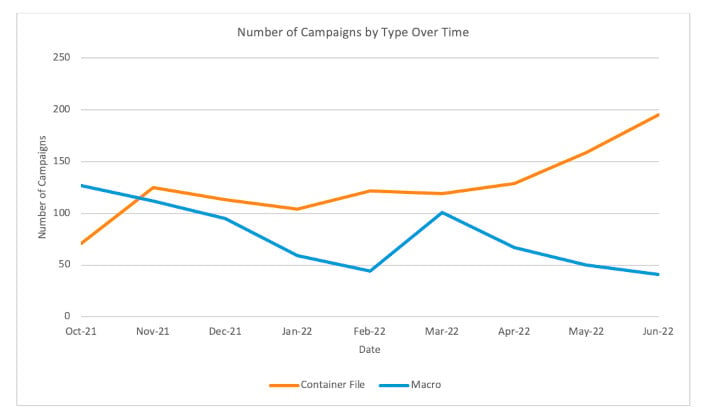
Graph Exhibiting Container Campaigns vs Macro Campaigns (Supply: Proofpoint)
How might they do it? By basically forcing customers to take an additional step when downloading attachments. If an Excel file is downloaded from an online browser, or as a direct attachment from an e-mail, it is going to be flagged as coming from the web. Nevertheless, if the file originated from inside a container-style file, akin to a zipper, rar, iso, img, or different container, the originating location would be the native drive in keeping with Home windows. As a result of the file was extracted from a compressed container, the “from the web” flag is not utilized.
LNK recordsdata can be used to avoid Microsoft newest measures. On Home windows machines, LNK recordsdata are used for issues like desktop shortcuts. Much less savvy customers might click on LNK recordsdata and be linked to a malware payload which may already reside regionally, and even pushed into downloading malware. Proofpoint’s statistics point out that LNK based-threats have considerably elevated since Microsoft’s announcement to limit the default habits and use of macros.
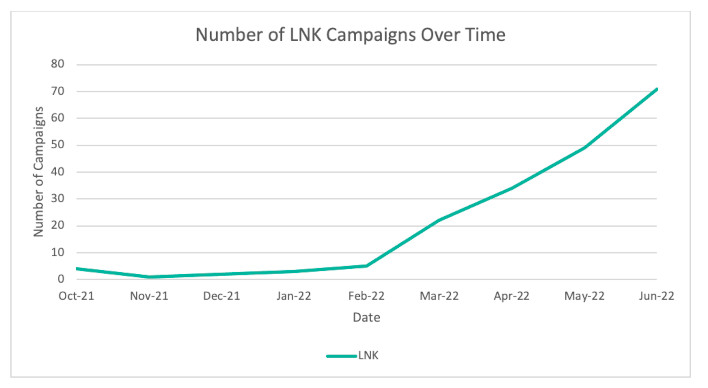
Graph Indicating an Improve in LNK malware campaigns (Supply: Proofpoint)
Whatever the measures and potential restrictions put in place by Microsoft, safety schooling and coaching stay a customers finest safety towards malware. By no means clicking hyperlinks or opening recordsdata from untrusted sources is essential. System directors, in fact, are suggested to repeatedly remind and replace customers on finest security practices as properly.