For the previous 5 years, the Nationwide Vulnerability Database (NVD) has damaged its personal document of reported vulnerabilities and is on tempo to do the identical in 2022. With a risk panorama rising that rapidly, it is no shock to see safety groups cannot preserve tempo.
In keeping with a report from Cobalt, 79% of safety groups battle to persistently monitor for vulnerabilities amid at the moment’s labor shortages, and 54% of safety respondents are contemplating quitting their jobs.
Making an attempt to remediate every part was by no means a profitable technique. Danger-based vulnerability administration (RBVM) is an method that will get organizations higher outcomes with much less effort than attempting to maintain up with the each day common of greater than 60 new vulnerabilities up to now in 2022.
5 years of information backs this up. The highest 4 metrics used to measure success with RBVM have persistently gotten higher, at the same time as a document variety of widespread vulnerabilities and exposures (CVEs) has added extra noise to the fray annually.
Let’s take a deeper have a look at these metrics, how they’ve improved, and why they’ve improved.
RBVM 101
In its early days, RBVM was taboo as a result of everybody noticed vulnerability administration as an all-or-nothing proposition. Treasured few reached “all” standing, and getting there meant a whole lot of time wasted on remediating vulnerabilities that posed no risk.
“Maturity fashions” try to gather one of the best cybersecurity practices decided by specialists and tweak them over time, however there’s an excellent higher means: information. A collection of analysis studies from the Cyentia Institute
has supplied some solutions on what organizations ought to be prioritizing and knowledgeable a greater method to RBVM.
Analysis produced together with the Cyentia Institute has proven that 23% of printed vulnerabilities have related exploit code and a pair of% have noticed exploits within the wild. That dramatically reduces the quantity of effort required … should you’re remediating the correct means.
We are able to decide how organizations are doing by taking a look at remediation capability, velocity, protection, and effectivity. The Cyentia Institute analyzed information from Kenna’s platform throughout the previous 5 years and visualized it within the charts under.
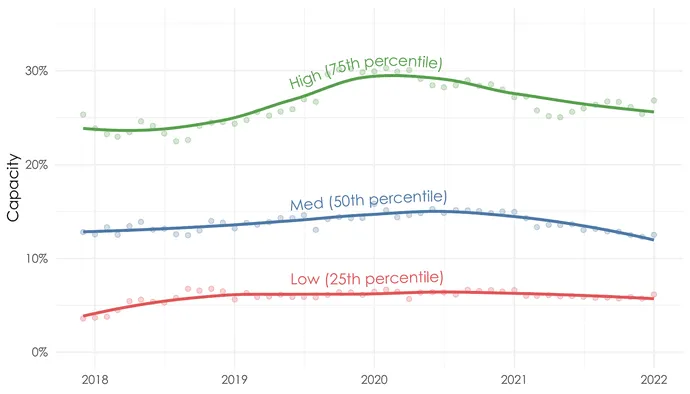
Capability, the proportion of open vulnerabilities being closed on common each month, has usually elevated over the previous 5 years for main and common organizations. Whereas most organizations are remediating extra of their open vulnerabilities, the underside quarter of organizations has remained regular with no significant shifts.
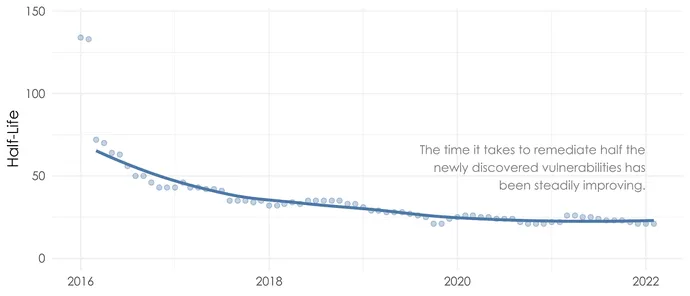
Remediation velocity noticed fast, significant progress and has since been bettering slowly. The place we are actually is a huge development over early 2016, when the half-life was greater than 125 days. During the last 4 years, the half-life — or time it takes to remediate half the newly found vulnerabilities — has dropped by greater than a 3rd from 32 days to 21 days.
Effectivity and protection are associated, which is why they’re proven collectively, and and not using a important change in prioritization technique, bettering a kind of metrics will usually result in a lower within the different. For instance, one option to improve protection is to easily remediate extra, however that makes you much less environment friendly.
Round 2018, each protection and effectivity have been round 35%, however a rise in protection (extra exploited vulns are remediated accurately) causes a lower in effectivity (fewer of the remediated vulnerabilities are being exploited). That is seemingly brought on by organizations rising their capability to remediate extra vulnerabilities.
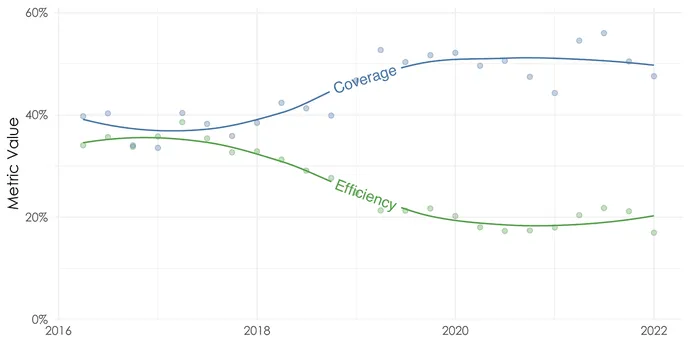
Remember the fact that that is all occurring as we have seen the variety of reported vulnerabilities improve annually since 2017. Organizations which have adopted RBVM are filtering out the noise by specializing in danger. They’re additionally remediating extra vulnerabilities sooner, which is why protection and effectivity proceed to enhance.
Explaining the Success
Whereas a extra clever method to vulnerability administration makes the largest distinction, distributors have gotten smarter, too. Analysis tells us that Microsoft has extra weak property noticed and extra exploitation exercise than its friends. When the software program large points patches rapidly, it has a heavy affect on remediation velocity (organizations deal with half their vulnerabilities affecting Microsoft merchandise in roughly 22 days, greater than 40 instances faster than SAP or Linux at 900 days).
Between a wiser method and fast patches from software program distributors, vulnerability administration is in a much better place than it was 5 years in the past. The proof is within the numbers that organizations have higher success once they method safety by a danger lens.
The labor market has additional difficult the already advanced challenge of safety, however now organizations know they do not have to repair every part. In truth, it might be foolish to and you will find yourself driving your worthwhile safety practitioners away. By adopting RBVM, organizations can begin to quell the unrelenting pandemonium at the moment’s safety panorama has turn out to be.


