The operators of the Hive ransomware-as-a-service (RaaS) scheme have overhauled their file-encrypting software program to totally migrate to Rust and undertake a extra subtle encryption technique.
“With its newest variant carrying a number of main upgrades, Hive additionally proves it is one of many quickest evolving ransomware households, exemplifying the repeatedly altering ransomware ecosystem,” Microsoft Risk Intelligence Middle (MSTIC) mentioned in a report on Tuesday.
Hive, which was first noticed in June 2021, has emerged as some of the prolific RaaS teams, accounting for 17 assaults within the month of Might 2022 alone, alongside Black Basta and Conti.
The shift from GoLang to Rust makes Hive the second ransomware pressure after BlackCat to be written within the programming language, enabling the malware to realize extra advantages similar to reminiscence security and deeper management over low-level assets in addition to make use of a variety of cryptographic libraries.
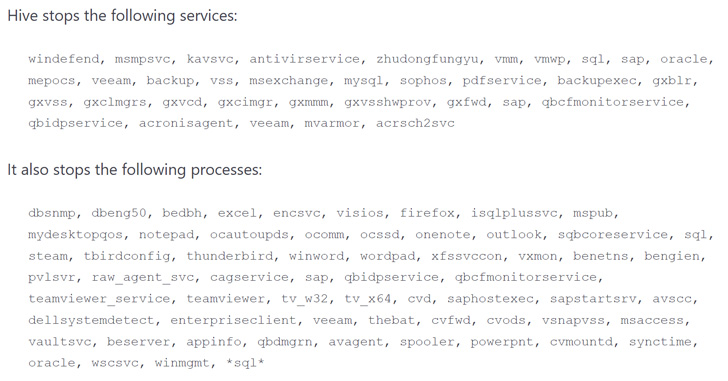
What it additionally affords is the power to render the malware proof against reverse engineering, making it extra evasive. Moreover, it comes with options to cease companies and processes related to safety options which will cease it in its tracks.
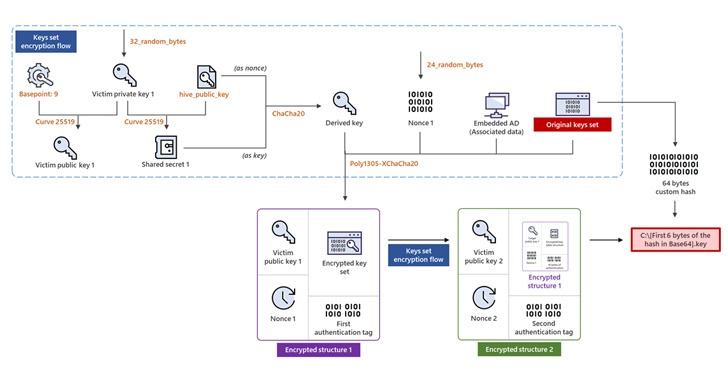
Hive is not any completely different from different ransomware households in that it deletes backups to stop restoration, however what’s modified considerably within the new Rust-based variant is its method to file encryption.
“As an alternative of embedding an encrypted key in every file that it encrypts, it generates two units of keys in reminiscence, makes use of them to encrypt recordsdata, after which encrypts and writes the units to the basis of the drive it encrypts, each with .key extension,” MSTIC defined.
To find out which of the 2 keys is used for locking a particular file, an encrypted file is renamed to incorporate the file identify containing the important thing that is then adopted by an underscore and a Base64-encoded string (e.g., “C:myphoto.jpg.l0Zn68cb _ -B82BhIaGhI8”) that factors to 2 completely different places within the corresponding .key file.
The findings come because the menace actor behind the lesser-known AstraLocker ransomware ceased operations and launched a decryption software as a part of a shift to crytojacking, Bleeping Laptop reported this week.
However in a sign that the cybercriminal panorama is in fixed flux, cybersecurity researchers have found a brand new ransomware household known as RedAlert (aka N13V) that is able to concentrating on each Home windows and Linux VMWare ESXi servers.