VirusTotal, an internet service that analyzes over two million information and web sites a day by checking them in opposition to over seventy anti-virus scanners and area block lists, has launched a report offering perception into the varied strategies of deception employed in malware campaigns. In line with the report, risk actors are more and more packaging malware with respectable app installers, in addition to designing malware to visually mimic respectable purposes.
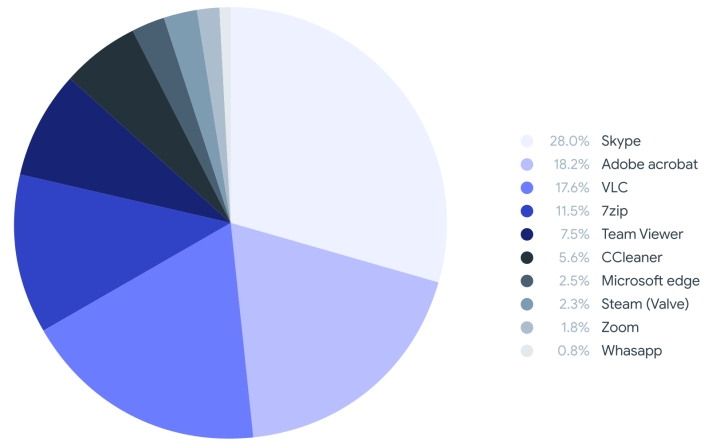
VirusTotal was stunned to search out how regularly malicious information are signed with stolen signing keys. Earlier this 12 months, a bunch of hackers generally known as LAPSUS$ claimed to steal 1TB of information from NVIDIA. The group publicly leaked solely 20GB of this knowledge earlier than the seven members of the group had been arrested. Nonetheless, this leak nonetheless induced important injury because it revealed two of NVIDIA’s code signing certificates, which malware builders promptly started utilizing to signal malicious packages. NVIDIA just isn’t distinctive in having its signing keys stolen. Different corporations have had their certificates stolen as nicely. A few of these stolen keys change into invalidated, whether or not by expiring or being revoked. Nevertheless, VirusTotal nonetheless detected virtually a million malicious information signed with legitimate certificates between January 2021 and June 2022.
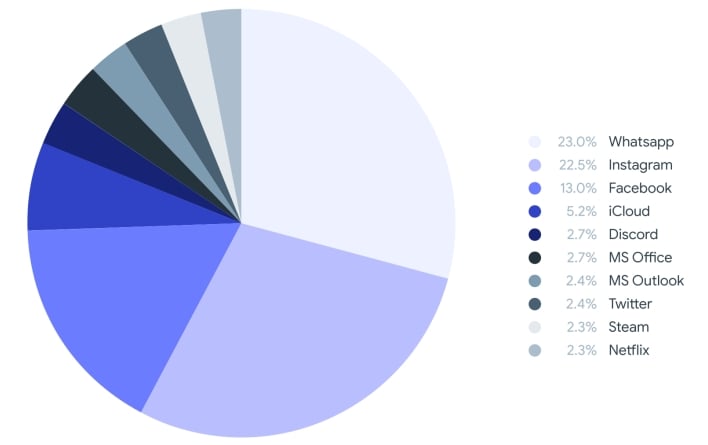
Lastly, VirusTotal seemed not simply at malware packages themselves, but additionally web sites that distribute malware. As talked about above, phishing assaults usually make use of web sites designed to seem like respectable web sites. Fraudulent web sites usually use the identical favicon as that of the web sites they mimic. A favicon is the little icon that seems on the prime of an online browser once you go to a web site. In line with the report, the Whatsapp, Instagram, and Fb favicons are these most regularly utilized by malicious web sites.


