A hacktivist collective known as GhostSec has claimed credit score for compromising as many as 55 Berghof programmable logic controllers (PLCs) utilized by Israeli organizations as a part of a “Free Palestine” marketing campaign.
Industrial cybersecurity agency OTORIO, which dug deeper into the incident, stated the breach was made doable owing to the truth that the PLCs had been accessible by the Web and had been secured by trivially guessable credentials.
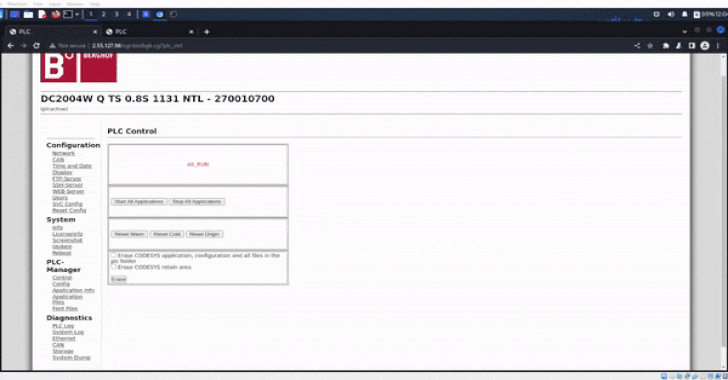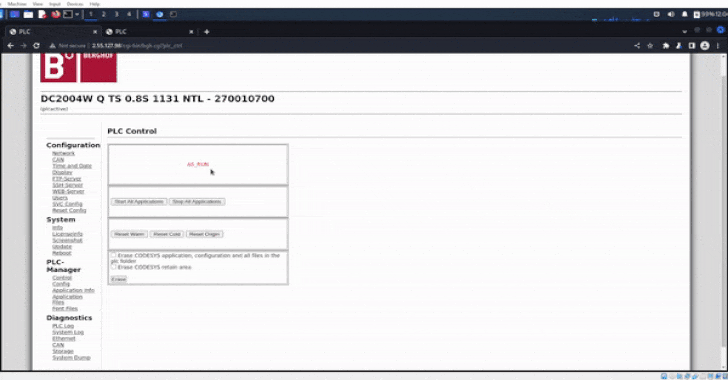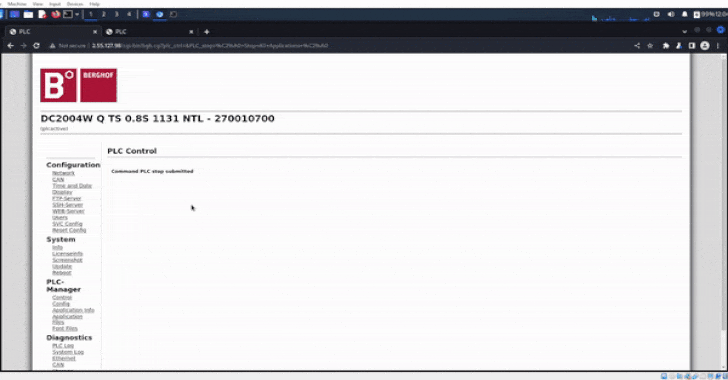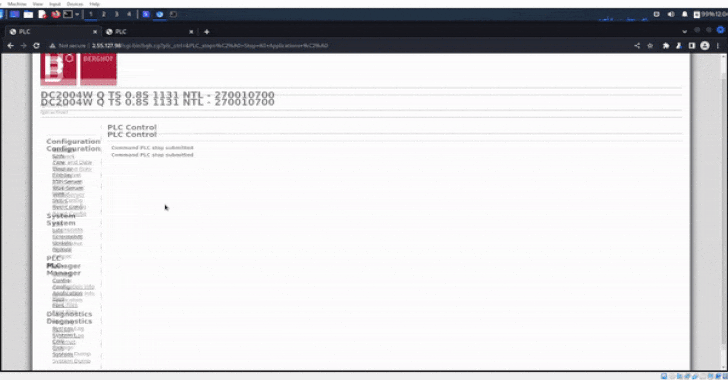
Particulars of the compromise first got here to gentle on September 4 after GhostSec shared a video on its Telegram channel demonstrating a profitable login to the PLC’s admin panel, along with dumping information from the hacked controllers.
The Israeli firm stated the system dumps and screenshots had been exported instantly from the admin panel following unauthorized entry to the controllers by their public IP addresses.
GhostSec (aka Ghost Safety), first recognized in 2015, is a self-proclaimed vigilante group that was initially fashioned to goal ISIS web sites that preach Islamic extremism.
Earlier this February, the group rallied its assist for Ukraine within the instant aftermath of Russia’s navy invasion of the nation. Since late June, it has additionally participated in a marketing campaign focusing on Israeli organizations and enterprises.
“The group pivoted from their common operations and began to focus on a number of Israeli firms, presumably getting access to numerous IoT interfaces and ICS/SCADA methods, which led to doable disruptions,” Cyberint famous on July 14.
The assaults in opposition to Israeli targets, dubbed “#OpIsrael,” is alleged to have commenced on June 28, 2022, citing “steady assaults from Israel in the direction of Palestinians.”
Within the intervening interval, GhostSec has carried out plenty of assaults, together with these aimed toward internet-exposed interfaces belonging to Bezeq Worldwide and an ELNet energy meter situated on the Scientific Industries Heart (Matam).
The breach of Berghof PLCs, considered in that gentle, is a part of the actor’s broader shift to strike the SCADA/ICS area, though it seems to be a case whereby the group took benefit of “simply ignored misconfigurations of commercial methods” to hold out the assaults.
“Regardless of the low affect of this incident, this can be a nice instance the place a cyber assault may have simply been averted by easy, correct configuration,” the researchers stated.
“Disabling the general public publicity of belongings to the Web, and sustaining a superb password coverage, particularly altering the default login credentials, would trigger the hacktivists’ breach try to fail.”
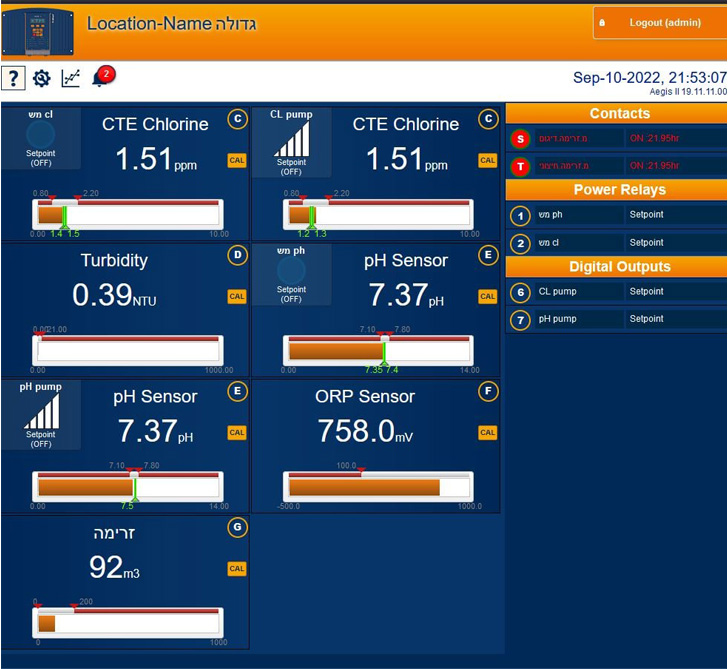
GhostSec, in the intervening time, has continued to submit extra screenshots, claiming to have gained entry to a different management panel that can be utilized to change chlorine and pH ranges within the water.
“Hope you all can perceive our resolution on not attacking their pH ranges and risking an opportunity to hurt the innocents of #Israel,” the group stated in a tweet posted over the weekend. “Our ‘battle’ has all the time been FOR the folks not in opposition to them. #FreePalestine”