Malicious actors are resorting to voice phishing (vishing) techniques to dupe victims into putting in Android malware on their units, new analysis from ThreatFabric reveals.
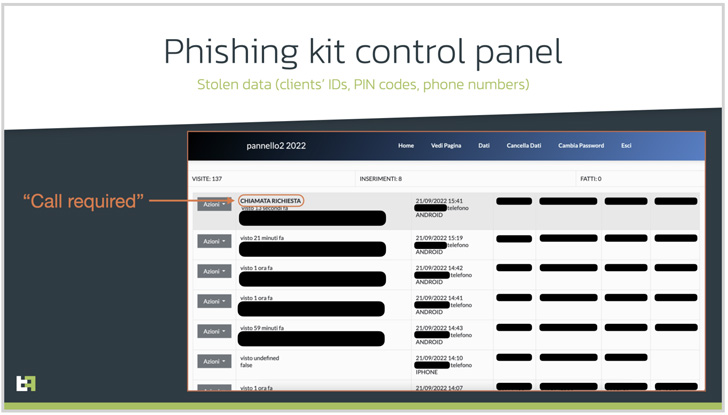
The Dutch cell safety firm mentioned it recognized a community of phishing web sites focusing on Italian online-banking customers which can be designed to pay money for their contact particulars.
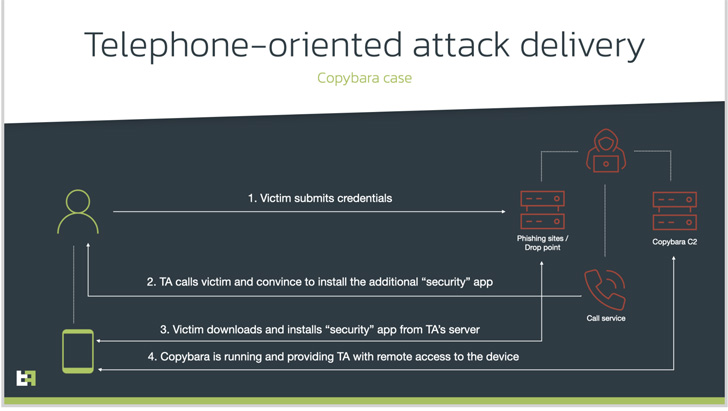
Phone-oriented assault supply (TOAD), because the social engineering approach known as, entails calling the victims utilizing beforehand collected info from fraudulent web sites.
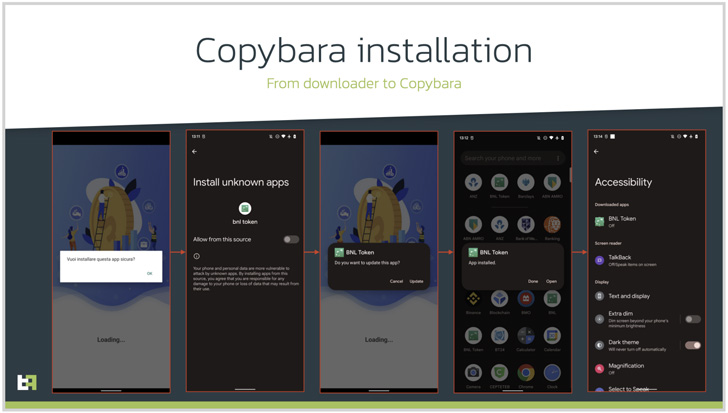
The caller, who purports to be a assist agent for the financial institution, instructs the person, then again, to put in a safety app and grant it intensive permissions, when, in actuality, it is malicious software program supposed to realize distant entry or conduct monetary fraud.
On this case, it results in the deployment of an Android malware dubbed Copybara, a cell trojan first detected in November 2021 and is primarily used to carry out on-device fraud by way of overlay assaults focusing on Italian customers. Copybara has additionally been confused with one other malware household often called BRATA.
ThreatFabric assessed the TOAD-based campaigns to have commenced across the similar time, indicating that the exercise has been ongoing for practically a 12 months.
Like some other Android-based malware, Copybara’s RAT capabilities are powered by abusing the working system’s accessibility providers API to collect delicate info and even uninstall the downloader app to scale back its forensic footprint.
What’s extra, the infrastructure utilized by the risk actor has been discovered to ship a second malware named SMS Spy that permits the adversary to realize entry to all incoming SMS messages and intercept one-time passwords (OTPs) despatched by banks.
The brand new wave of hybrid fraud assaults presents a brand new dimension for scammers to mount convincing Android malware campaigns which have in any other case relied on conventional strategies similar to Google Play Retailer droppers, rogue adverts, and smishing.
“Such assaults require extra sources on [threat actors’] aspect and are extra refined to carry out and preserve,” ThreatFabric’s Cellular Risk Intelligence (MTI) staff informed The Hacker Information.
“We additionally wish to level out that focused assaults from a fraud success perspective are sadly extra profitable, at the least on this particular marketing campaign.”
This isn’t the primary time TOAD techniques are being employed to orchestrate banking malware campaigns. Final month, the MalwareHunterTeam detailed the same assault geared toward customers of the Indian financial institution Axis Financial institution in a bid to put in an info-stealer that impersonates a bank card rewards app.
“Any suspicious name needs to be double checked by calling your monetary group,” the MTI staff mentioned, including “monetary organizations ought to present their clients with information about ongoing campaigns and improve the shopper apps with mechanisms to detect suspicious exercise.”