The operators of RomCom RAT are persevering with to evolve their campaigns with rogue variations of software program akin to SolarWinds Community Efficiency Monitor, KeePass password supervisor, and PDF Reader Professional.
Targets of the operation encompass victims in Ukraine and choose English-speaking international locations just like the U.Okay.
“Given the geography of the targets and the present geopolitical state of affairs, it is unlikely that the RomCom RAT risk actor is cybercrime-motivated,” the BlackBerry Menace Analysis and Intelligence Group mentioned in a brand new evaluation.
The most recent findings come per week after the Canadian cybersecurity firm disclosed a spear-phishing marketing campaign aimed toward Ukrainian entities to deploy a distant entry trojan known as RomCom RAT.
The unknown risk actor has additionally been noticed leveraging trojanized variants of Superior IP Scanner and pdfFiller as droppers to distribute the implant.
The most recent iteration of the marketing campaign entails establishing decoy lookalike web sites with an analogous area title, adopted by importing a malware-laced installer bundle of the malicious software program, after which sending phishing emails to focused victims.
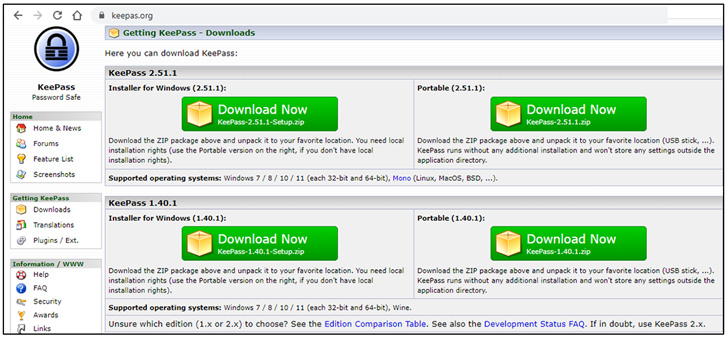 |
| Pretend Keypass web site |
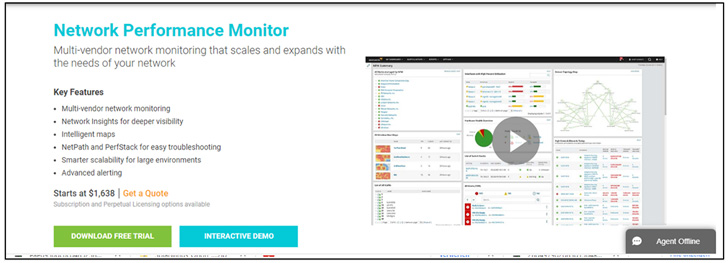 |
| Pretend SolarWinds web site |
“Whereas downloading a free trial from the spoofed SolarWinds website, a reputable registration type seems,” the researchers defined.
“If crammed out, actual SolarWinds gross sales personnel would possibly contact the sufferer to comply with up on the product trial. That approach misleads the sufferer into believing that the not too long ago downloaded and put in utility is totally reputable.”
It isn’t simply SolarWinds software program. Different impersonated variations contain the favored password supervisor KeePass and PDF Reader Professional, together with within the Ukrainian language.
The usage of RomCom RAT has additionally been linked to risk actors related to the Cuba ransomware and Industrial Spy, in keeping with Palo Alto Networks Unit 42, which is monitoring the ransomware group below the constellation-themed moniker Tropical Scorpius.
Given the interconnected nature of the cybercriminal ecosystem, it isn’t instantly evident if the 2 units of actions share any connections or if the malware is obtainable on the market as a service to different risk actors.



