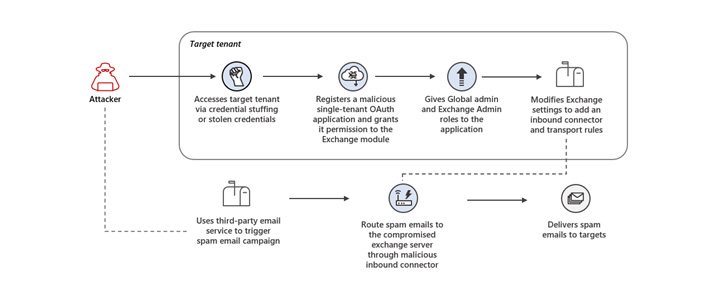
Microsoft on Thursday warned of a consumer-facing assault that made use of rogue OAuth purposes deployed on compromised cloud tenants to in the end seize management of Trade servers and unfold spam.
“The risk actor launched credential stuffing assaults in opposition to high-risk accounts that did not have multi-factor authentication (MFA) enabled and leveraged the unsecured administrator accounts to realize preliminary entry,” the Microsoft 365 Defender Analysis Crew stated.
The unauthorized entry to the cloud tenant permitted the adversary to register a malicious OAuth utility and grant it elevated permissions, and finally modify Trade Server settings to permit inbound emails from particular IP addresses to be routed by the compromised e mail server.
“These modifications to the Trade server settings allowed the risk actor to carry out their major aim within the assault: sending out spam emails,” Microsoft stated. “The spam emails had been despatched as a part of a misleading sweepstakes scheme meant to trick recipients into signing up for recurring paid subscriptions.”
The e-mail messages urged the recipients to click on on a hyperlink to obtain a prize, doing so which redirected the victims to a touchdown web page that requested the victims to enter their bank card particulars for a small delivery price to gather the reward.
The risk actor additional carried out plenty of steps to evade detection and proceed its operations for prolonged intervals of time, together with taking weeks and even months to make use of the malicious OAuth utility after it was arrange and deleting the modifications made to the Trade Server after every spam marketing campaign.
Microsoft’s risk intelligence division stated that the adversary has been actively operating spam e mail campaigns for a number of years, sometimes sending excessive volumes of spam emails briefly bursts by a wide range of strategies.
Though the first aim of the assault seems to be to trick unwitting customers into signing up for undesirable subscription companies, it may have posed a much more severe risk had the identical approach been used to steal credentials or distribute malware.
“Whereas the follow-on spam marketing campaign targets shopper e mail accounts, this assault targets enterprise tenants to make use of as infrastructure for this marketing campaign,” Microsoft stated. “This assault thus exposes safety weaknesses that may very well be utilized by different risk actors in assaults that might straight impression affected enterprises.”