 A brand new phishing technique makes use of a decades-old particular URL format to benefit from how safety options and e-mail shoppers interpret URLs, tricking victims into clicking.
A brand new phishing technique makes use of a decades-old particular URL format to benefit from how safety options and e-mail shoppers interpret URLs, tricking victims into clicking.
It’s known as the HTTP Authorization header and it’s been round since 1999 as a part of RFC 2616 which outlined HTTP model 1.1. It specifies that an HTTP net request can include a username and password in a URL simply earlier than the fully-qualified area identify. For instance:
https://username:password@notarealdomainname.ext
Every part after the double ahead slash and earlier than the “@” is interpreted as authentication credentials. A brand new phishing technique noticed by safety researchers at Notion Level discovered that scammers had been making the most of the “@”, putting it in what can be perceived because the “center” of a sound URL, solely to trick e-mail shoppers and scanning options into decoding the URL as being benign, when it was something however.
Take the thought of tricking a person into pondering they had been going to be taken to the next URL:
http://www[.]workplace[.]com[/]login
However the URL really reads:
http://www[.]workplace[.]com[/]login@maliciousdomain[.]com
With many net browsers, every little thing earlier than the “@” is taken into account authentication particulars and the vacation spot area is every little thing after the “@”. In distinction, the e-mail scanners could not interpret the URL correctly in any respect and deem it to not be a menace.
Within the case of the assault discovered by Notion Level, the URL in query is discovered within the following picture:
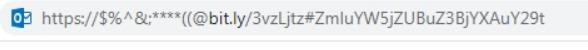
The actual URL is the Bitly hyperlink which takes victims to a spoofed Microsoft 365 logon web page.
The one saving grace can be present in these customers that know to scrutinize the ultimate URL they’re taken to (which was not Microsoft 365) earlier than they supply credentials. Customers that endure continuous Safety Consciousness Coaching are taught to at all times be on guard trying to something out of the strange – whether or not it’s a hyperlink with an “@” in the course of it, or an incorrect URL on a logon web page.


