The superior persistent menace (APT) actor tracked as Evilnum is as soon as once more exhibiting indicators of renewed exercise geared toward European monetary and funding entities.
“Evilnum is a backdoor that can be utilized for information theft or to load further payloads,” enterprise safety agency Proofpoint mentioned in a report shared with The Hacker Information. “The malware consists of a number of fascinating parts to evade detection and modify an infection paths based mostly on recognized antivirus software program.”
Targets embrace organizations with operations supporting overseas exchanges, cryptocurrency, and decentralized finance (DeFi). The newest spate of assaults are mentioned to have commenced in late 2021.
The findings additionally dovetail with a report from Zscaler final month that detailed low-volume focused assault campaigns launched in opposition to corporations in Europe and the U.Ok.
Energetic since 2018, Evilnum is tracked by the broader cybersecurity neighborhood utilizing the names TA4563 and DeathStalker, with an infection chains culminating within the deployment of the eponymous backdoor that is able to reconnaissance, information theft, or fetching further payloads.
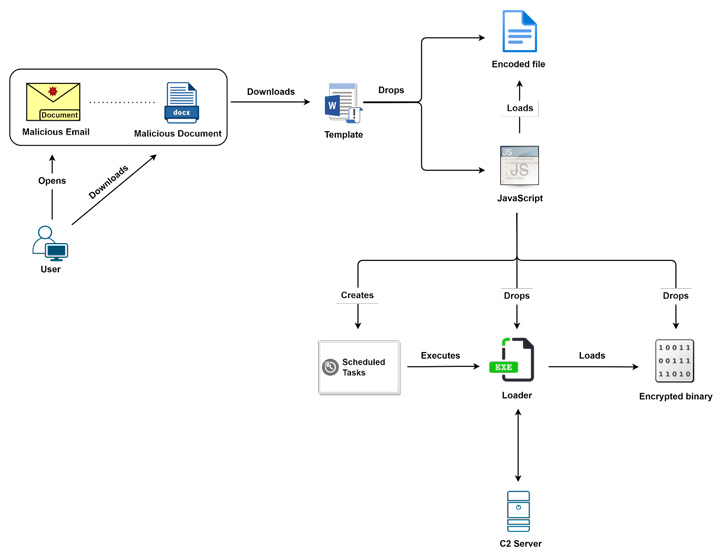
The newest set of actions flagged by Proofpoint incorporate up to date ways, methods, and procedures (TTPs), counting on a mixture of Microsoft Phrase, ISO, and Home windows Shortcut (LNK) information despatched as electronic mail attachments in spear-phishing emails to the victims.
Different variants of the marketing campaign noticed in early 2022 have made use of monetary lures to entice recipients into opening .LNK information inside malicious ZIP archive attachments or clicking on OneDrive URLs containing both an ISO or LNK file.
In yet one more occasion, the actor switched up the modus operandi to ship macro-laden Microsoft Phrase paperwork that drop obfuscated JavaScript code designed to launch the backdoor binary.
This system was as soon as once more modified in mid-2022 to distribute Phrase paperwork, which try to retrieve a distant template and connect with an attacker-controlled area. Whatever the distribution vector employed, the assaults result in the execution of the Evilnum backdoor.
Though no next-stage malware executables had been recognized, the backdoor is thought to behave as a conduit to ship payloads from the malware-as-a-service (MaaS) supplier Golden Chickens.
“Monetary organizations, particularly these working in Europe and with cryptocurrency pursuits, ought to pay attention to TA4563 exercise,” Sherrod DeGrippo, vice President of menace analysis and detection at Proofpoint, mentioned in an announcement. “The group’s malware generally known as Evilnum is below energetic improvement.”