Main monetary and insurance coverage corporations positioned in French-speaking nations in Africa have been focused over the previous two years as a part of a persistent malicious marketing campaign codenamed DangerousSavanna.
International locations focused embrace Ivory Coast, Morocco, Cameroon, Senegal, and Togo, with the spear-phishing assaults closely specializing in Ivory Coast in latest months, Israeli cybersecurity agency Verify Level stated in a Tuesday report.
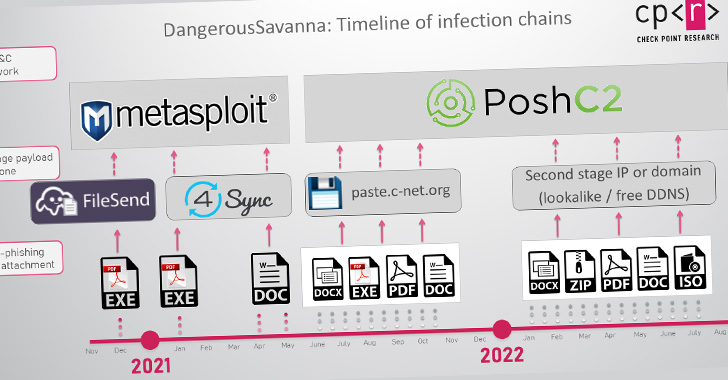
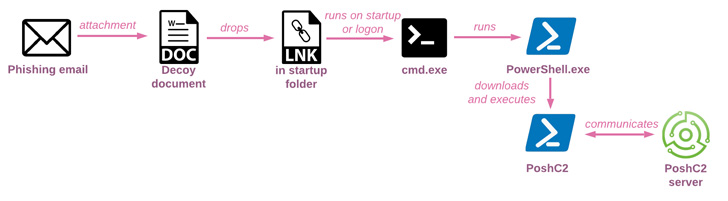
An infection chains entail concentrating on workers of economic establishments with social engineering messages containing malicious attachments as a method of preliminary entry, finally resulting in the deployment of off-the-shelf malware similar to Metasploit, PoshC2, DWservice, and AsyncRAT.
“The menace actors’ creativity is on show within the preliminary an infection stage, as they persistently pursue the workers of the focused corporations, continuously altering an infection chains that make the most of a variety of malicious file sorts, from self-written executable loaders and malicious paperwork, to ISO, LNK, JAR and VBE recordsdata in numerous combos,” the corporate stated.
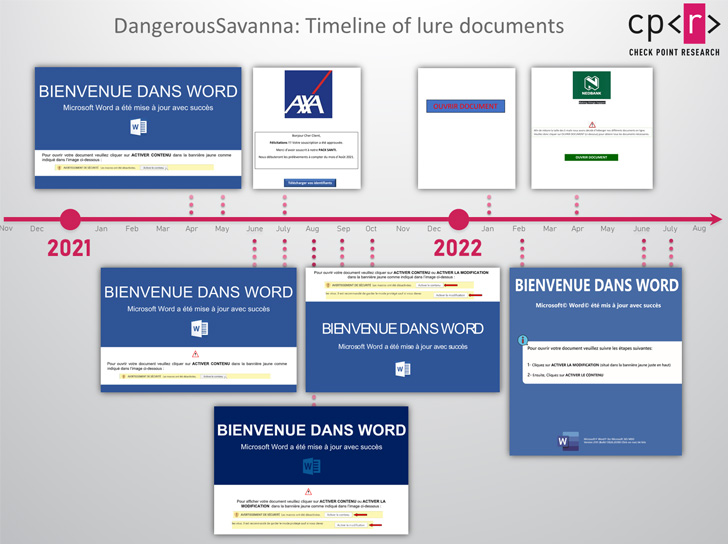
The phishing emails are written in French and despatched utilizing Gmail and Hotmail companies, with the messages additionally impersonating different monetary establishments in Africa to spice up their credibility.
Whereas assaults in 2021 leveraged macro-laced Microsoft Phrase paperwork as lures, the corporate’s choice to block macros in recordsdata downloaded from the web by default earlier this 12 months has led the DangerousSavanna actors to pivot to PDF and ISO recordsdata.
Moreover, the primary wave of assaults from the tip of 2020 to the start of 2021 concerned the usage of bespoke .NET-based instruments, which got here disguised as PDF recordsdata hooked up to phishing emails, to retrieve next-stage droppers and loaders from distant servers.
Whatever the methodology used, post-exploitation actions carried out after acquiring an preliminary foothold embrace establishing persistence, performing reconnaissance, and delivering further payloads to remotely management the host, kill anti-malware processes, and log keystrokes.
The precise provenance of the menace actor stays unclear, however the frequent shift in its instruments and strategies demonstrates their information of open-source software program and their capacity to fine-tune their techniques for maximizing monetary achieve.
“If one an infection chain did not work out, they modified the attachment and the lure and tried concentrating on the identical firm repeatedly looking for an entry level,” Verify Level stated. “With social engineering through spear-phishing, all it takes is one incautious click on by an unsuspecting consumer.”