With Microsoft taking steps to dam Excel 4.0 (XLM or XL4) and Visible Fundamental for Functions (VBA) macros by default throughout Workplace apps, malicious actors are responding by refining their new techniques, strategies, and procedures (TTPs).
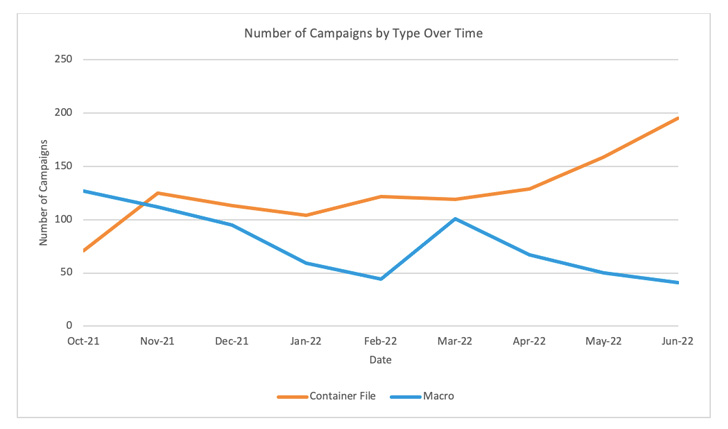
“Using VBA and XL4 Macros decreased roughly 66% from October 2021 via June 2022,” Proofpoint stated in a report shared with The Hacker Information.
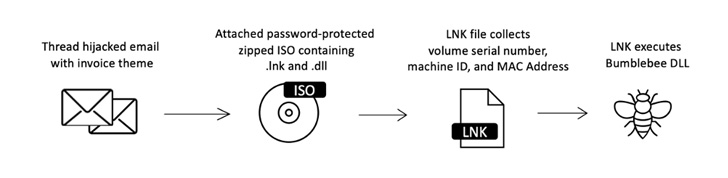
Instead, adversaries are more and more pivoting away from macro-enabled paperwork to different alternate options, together with container recordsdata resembling ISO and RAR in addition to Home windows Shortcut (LNK) recordsdata in campaigns to distribute malware.
VBA macros embedded in Workplace paperwork despatched by way of phishing emails have confirmed to be an efficient method in that it permits risk actors to routinely run malicious content material after tricking a recipient into enabling macros by way of social engineering techniques.
Nonetheless, Microsoft’s plans to block macros in recordsdata downloaded from the web have led to email-based malware campaigns experimenting with different methods to bypass Mark of the Net (MOTW) protections and infect victims.
This entails the usage of ISO, RAR and LNK file attachments, which have surged almost 175% throughout the identical interval. At the very least 10 risk actors are stated to have begun utilizing LNK recordsdata since February 2022.
“The variety of campaigns containing LNK recordsdata elevated 1,675% since October 2021,” the enterprise safety firm famous, including the variety of assaults utilizing HTML attachments greater than doubled from October 2021 to June 2022.
A few of the notable malware households distributed via these new strategies encompass Emotet, IcedID, Qakbot, and Bumblebee.
“Risk actors pivoting away from immediately distributing macro-based attachments in electronic mail represents a major shift within the risk panorama,” Sherrod DeGrippo, vp of risk analysis and detection at Proofpoint, stated in an announcement.
“Risk actors at the moment are adopting new techniques to ship malware, and the elevated use of recordsdata resembling ISO, LNK, and RAR is anticipated to proceed.”