Cybersecurity researchers are calling consideration to a free-to-use browser automation framework that is being more and more utilized by risk actors as a part of their assault campaigns.
“The framework incorporates quite a few options which we assess could also be utilized within the enablement of malicious actions,” researchers from Group Cymru stated in a brand new report printed Wednesday.
“The technical entry bar for the framework is purposefully stored low, which has served to create an lively neighborhood of content material builders and contributors, with actors within the underground economic system promoting their time for the creation of bespoke tooling.”
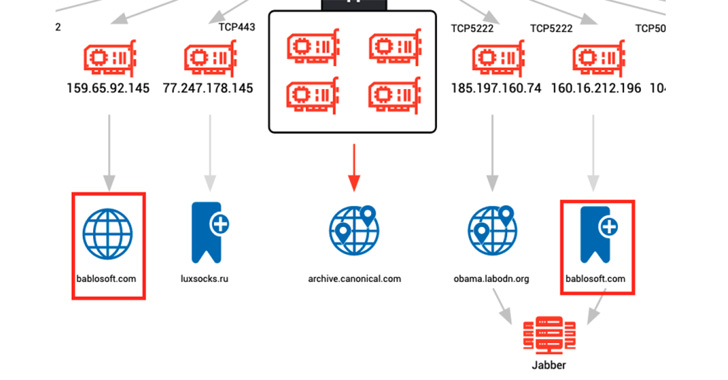
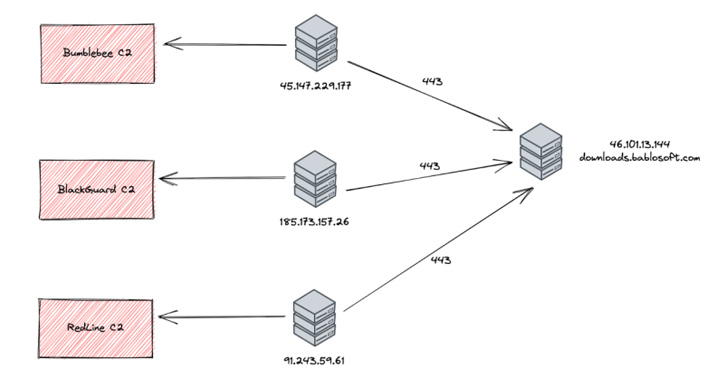
The U.S. cybersecurity firm stated it noticed command-and-control (C2) IP addresses related to malware similar to Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft (“downloads.bablosoft[.]com”), the maker of the Browser Automation Studio (BAS).
Bablosoft was beforehand documented by cloud safety and utility supply agency F5 in February 2021, pointing to the framework’s potential to automate duties in Google’s Chrome browser in a way just like official developer instruments like Puppeteer and Selenium.
Risk telemetry for the subdomain’s IP deal with — 46.101.13[.]144 — reveals {that a} overwhelming majority of exercise is originating from areas in Russia and Ukraine, with open supply intelligence indicating that Bablosoft’s proprietor is allegedly primarily based within the Ukrainian capital metropolis of Kyiv.
It is being suspected that the operators of the malware campaigns related to the Bablosoft subdomain for functions of downloading further instruments to be used as a part of post-exploitation actions.
Additionally recognized are a number of hosts related to cryptojacking malware like XMRig and Tofsee speaking with a second subdomain named “fingerprints.bablosoft[.]com” to make use of a service that helps the mining malware conceal its habits.
“Primarily based on the variety of actors already using instruments supplied on the Bablosoft web site, we will solely anticipate to see BAS changing into a extra widespread component of the risk actor’s toolkit,” the researchers stated.