A beforehand unknown menace actor has been focusing on corporations within the U.S. and Germany with bespoke malware designed to steal confidential info.
Enterprise safety firm Proofpoint, which is monitoring the exercise cluster below the identify Screentime, mentioned the group, dubbed TA866, is probably going financially motivated.
“TA866 is an organized actor capable of carry out properly thought-out assaults at scale primarily based on their availability of customized instruments; capability and connections to buy instruments and companies from different distributors; and growing exercise volumes,” the corporate assessed.
Campaigns mounted by the adversary are mentioned to have commenced round October 3, 2022, with the assaults launched through emails containing a booby-trapped attachment or URL that results in malware. The attachments vary from macro-laced Microsoft Writer information to PDFs with URLs pointing to JavaScript information.
The intrusions have additionally leveraged dialog hijacking to entice recipients into clicking on seemingly innocuous URLs that provoke a multi-step assault chain.
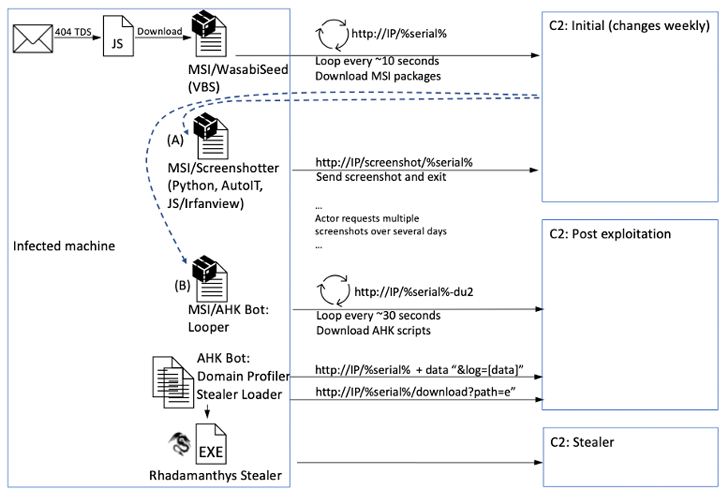
Regardless of the tactic used, executing the downloaded JavaScript file results in an MSI installer that unpacks a VBScript dubbed WasabiSeed, which capabilities as a instrument to fetch next-stage malware from a distant server.
One of many payloads downloaded by WasabiSeed is Screenshotter, a utility that is tasked with taking screenshots of the sufferer’s desktop periodically and transmitting that info again to a command-and-control (C2) server.
“That is useful to the menace actor in the course of the reconnaissance and sufferer profiling stage,” Proofpoint researcher Axel F mentioned.
A profitable reconnaissance section is adopted by the distribution of extra malware for post-exploitation, with choose assaults deploying an AutoHotKey (AHK)-based bot to drop an info stealer named Rhadamanthys.
Proofpoint mentioned the URLs used within the marketing campaign concerned a visitors route system (TDS) referred to as 404 TDS, enabling the adversary to serve malware solely in situations the place the victims meet a particular set of standards, corresponding to geography, browser utility, and working system.
The origins of TA866 stay unclear as but, though Russian language variable names and feedback have been recognized within the supply code of AHK Bot, a 2020 variant of which was employed in assaults aimed toward Canadian and U.S. banks. The malware can be suspected to have been put to make use of way back to April 2019.
“Using Screenshotter to assemble info on a compromised host earlier than deploying extra payloads signifies the menace actor is manually reviewing infections to determine high-value targets,” Proofpoint mentioned.
“You will need to notice that to ensure that a compromise to achieve success, a consumer has to click on on a malicious hyperlink and, if efficiently filtered, work together with a JavaScript file to obtain and run extra payloads.”
The findings come amid a spike in menace actors making an attempt out new methods to execute code on targets’ units after Microsoft blocked macros by default in Workplace information downloaded from the web.
This contains using search engine marketing (search engine optimisation) poisoning, malvertising, and model spoofing to distribute malware by packaging the payloads as well-liked software program corresponding to distant desktop apps and on-line assembly platforms.
Moreover, rogue adverts on Google search outcomes are getting used to redirect unsuspecting customers to fraudulent credential phishing web sites which can be designed to steal Amazon Net Companies (AWS) logins, in response to a brand new marketing campaign documented by SentinelOne.
“The proliferation of malicious Google Advertisements resulting in AWS phishing web sites represents a severe menace to not simply common customers, however community and cloud directors,” the cybersecurity firm mentioned.
“The convenience with which these assaults could be launched, mixed with the big and numerous viewers that Google Advertisements can attain, makes them a very potent menace.”
One other approach that has witnessed a surge in current months is the abuse of novel file codecs like Microsoft OneNote and Writer paperwork for malware supply.
The assaults aren’t any totally different from these utilizing different forms of malicious Workplace information, whereby the e-mail recipient is duped into opening the doc and clicking on a faux button, which ends up in the execution of embedded HTA code to retrieve Qakbot malware.
“E-mail directors have, over time, arrange guidelines that both outright forestall, or throw severe-sounding warnings, on any inbound messages originating from exterior the group with quite a lot of abusable file codecs connected,” Sophos researcher Andrew Brandt mentioned.
“It seems to be seemingly that OneNote .one notebooks would be the subsequent file format to finish up on the email-attachment chopping block, however for now, it stays a persistent threat.”