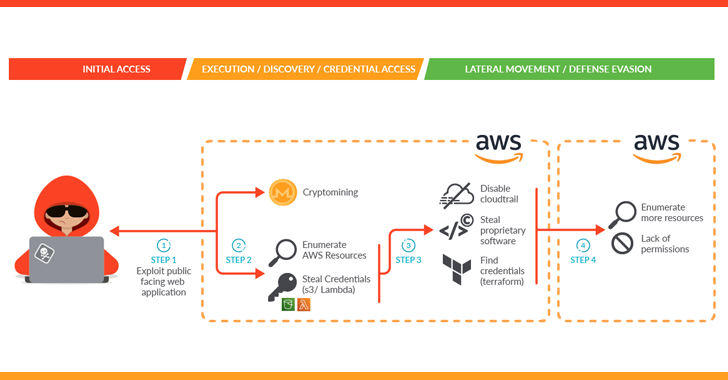
A classy assault marketing campaign dubbed SCARLETEEL is focusing on containerized environments to perpetrate theft of proprietary knowledge and software program.
“The attacker exploited a containerized workload after which leveraged it to carry out privilege escalation into an AWS account to be able to steal proprietary software program and credentials,” Sysdig stated in a brand new report.
The superior cloud assault additionally entailed the deployment of crypto miner software program, which the cybersecurity firm stated is both an try and generate illicit income or a ploy to distract defenders and throw them off the path.
The preliminary an infection vector banked on exploiting a weak public-facing service in a self-managed Kubernetes cluster hosted on Amazon Internet Companies (AWS).
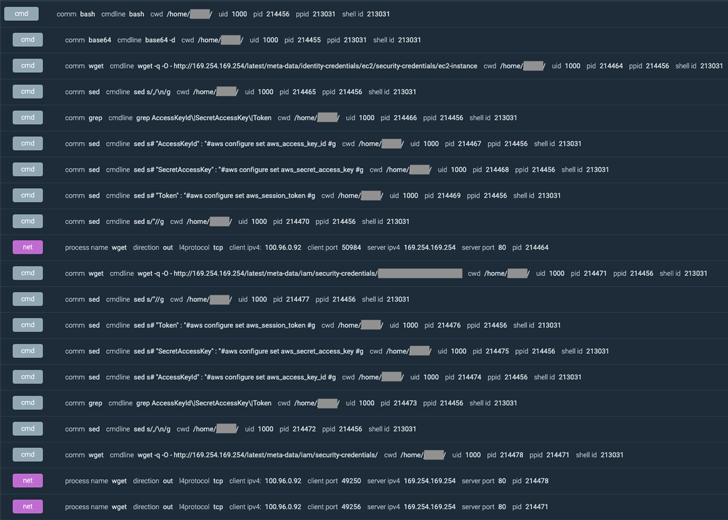
Upon gaining a profitable foothold, an XMRig crypto miner was launched and a bash script was used to acquire credentials that might be used to additional burrow into the AWS cloud infrastructure and exfiltrate delicate knowledge.
“Both crypto mining was the attacker’s preliminary objective and the objective modified as soon as they accessed the sufferer’s surroundings, or crypto mining was used as a decoy to evade the detection of knowledge exfiltration,” the corporate stated.
The intrusion notably additionally disabled CloudTrail logs to attenuate the digital footprint, stopping Sysdig from accessing further proof. In all, it allowed the risk actor to entry greater than 1TB of knowledge, together with buyer scripts, troubleshooting instruments, and logging recordsdata.
“Additionally they tried to pivot utilizing a Terraform state file to different linked AWS accounts to unfold their attain all through the group,” the corporate stated. This, nevertheless, proved to be unsuccessful resulting from lack of permissions.
The findings come weeks after Sysdig additionally detailed one other cryptojacking marketing campaign mounted by the 8220 Gang between November 2022 and January 2023 focusing on exploitable Apache internet server and Oracle Weblogic functions.