A brand new assault vector focusing on the Visible Studio Code extensions market might be leveraged to add rogue extensions masquerading as their reliable counterparts with the purpose of mounting provide chain assaults.
The method “might act as an entry level for an assault on many organizations,” Aqua safety researcher Ilay Goldman stated in a report printed final week.
VS Code extensions, curated by way of a market made obtainable by Microsoft, enable builders so as to add programming languages, debuggers, and instruments to the VS Code source-code editor to enhance their workflows.
“All extensions run with the privileges of the consumer that has opened the VS Code with none sandbox,” Goldman stated, explaining the potential dangers of utilizing VS Code extensions. “Which means the extension can set up any program in your laptop together with ransomwares, wipers, and extra.”
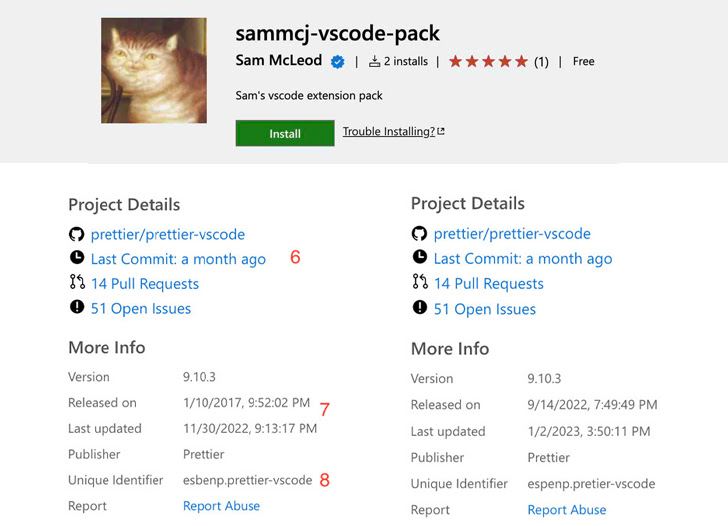
To that finish, Aqua discovered that not solely is it potential for a risk actor to impersonate a well-liked extension with small variations to the URL, {the marketplace} additionally permits the adversary to make use of the identical title and extension writer particulars, together with the mission repository data.
Whereas the tactic would not enable the variety of installs and the variety of stars to be replicated, the truth that there are not any restrictions on the opposite figuring out traits means it might be used to deceive builders.
The analysis additionally found that the verification badge assigned to authors might be trivially bypassed because the test mark solely proves that the extension writer is the precise proprietor of a site.
In different phrases, a malicious actor might purchase any area, register it to get a verified test mark, and finally add a trojanized extension with the identical title as that of a reliable one to {the marketplace}.
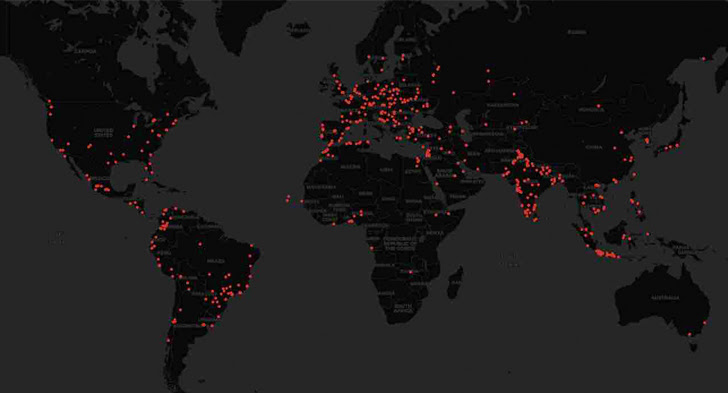
A proof-of-concept (PoC) extension masquerading because the Prettier code formatting utility racked up over 1,000 installations inside 48 hours by builders internationally, Aqua stated. It has since been taken down.
This isn’t the primary time issues have been raised about software program provide chain threats within the VS Code extensions market.
In Might 2021, enterprise safety agency Snyk uncovered plenty of safety flaws in fashionable VS Code extensions with hundreds of thousands of downloads that would have been abused by risk actors to compromise developer environments.
“Attackers are always working to broaden their arsenal of strategies permitting them to run malicious code contained in the community of organizations,” Goldman stated.