Net infrastructure firm Cloudflare on Tuesday disclosed not less than 76 workers and their relations obtained textual content messages on their private and work telephones bearing comparable traits as that of the delicate phishing assault in opposition to Twilio.
The assault, which transpired across the identical time Twilio was focused, got here from 4 telephone numbers related to T-Cell-issued SIM playing cards amd was finally unsuccessful.
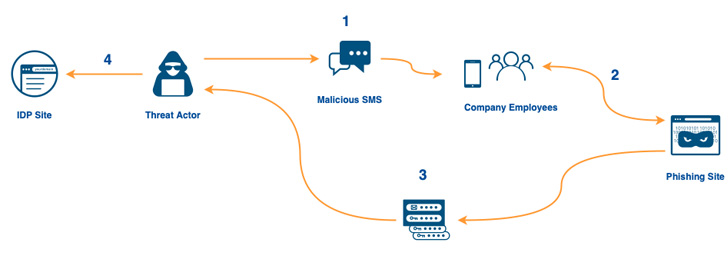
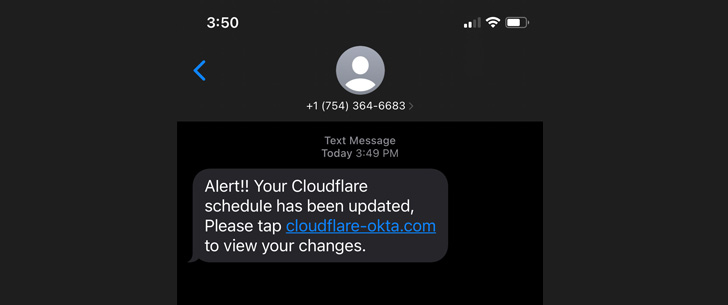
The textual content messages pointed to a seemingly official area containing the key phrases “Cloudflare” and “Okta” in an try and deceive the workers into handing over their credentials.
The wave of over 100 smishing messages commenced lower than 40 minutes after the rogue area was registered through Porkbun, the corporate famous, including the phishing web page was designed to relay the credentials entered by unsuspecting customers to the attacker through Telegram in real-time.
This additionally meant that the assault might defeat 2FA roadblocks, because the Time-based One Time Password (TOTP) codes inputted on the faux touchdown web page have been transmitted in a similar method, enabling the adversary to sign-in with the stolen passwords and TOTPs.
Cloudflare mentioned three of its workers fell for the phishing scheme, however famous that it was in a position to forestall its inner programs from being breached by way of using FIDO2-compliant bodily safety keys required to entry its purposes.
“Because the laborious keys are tied to customers and implement origin binding, even a complicated, real-time phishing operation like this can’t collect the data essential to log in to any of our programs,” Cloudflare mentioned.
“Whereas the attacker tried to log in to our programs with the compromised username and password credentials, they might not get previous the laborious key requirement.”
What’s extra, the assaults did not simply cease at stealing the credentials and TOTP codes. Ought to an worker get previous the login step, the phishing web page was engineered to robotically obtain AnyDesk’s distant entry software program, which, if put in, may very well be used to commandeer the sufferer’s system.
In addition to working with DigitalOcean to close down the attacker’s server, the corporate additionally mentioned it reset the credentials of the impacted workers and that it is tightening up its entry implementation to stop any logins from unknown VPNs, residential proxies, and infrastructure suppliers.
The event comes days after Twilio mentioned unknown hackers succeeded in phishing the credentials of an undisclosed variety of workers and gained unauthorized entry to the corporate’s inner programs, utilizing it to pay money for buyer accounts.