Risk actors related to the Cuba ransomware have been linked to beforehand undocumented ways, methods and procedures (TTPs), together with a brand new distant entry trojan referred to as ROMCOM RAT on compromised methods.
The new findings come from Palo Alto Networks’ Unit 42 risk intelligence workforce, which is monitoring the double extortion ransomware group below the constellation-themed moniker Tropical Scorpius.
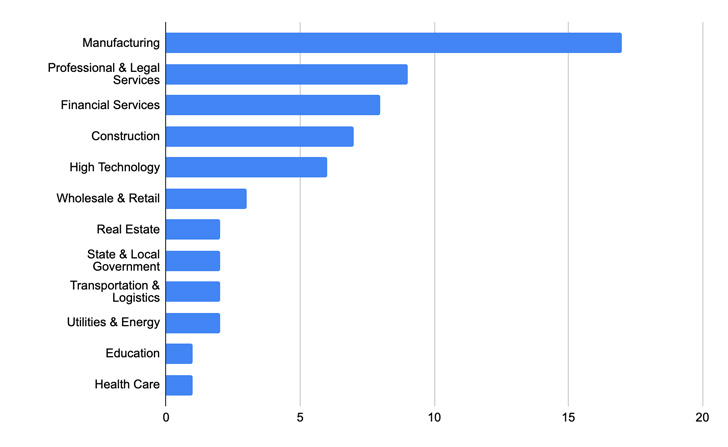
Cuba ransomware (aka COLDDRAW), which was first detected in December 2019, reemerged on the risk panorama in November 2021 and has been attributed to assaults in opposition to 60 entities in 5 essential infrastructure sectors, amassing at the least $43.9 million in ransom funds.
Of the 60 victims listed on its information leak website, 40 are positioned within the U.S., indicating a not as international distribution of focused organizations as different ransomware gangs.
“Cuba ransomware is distributed by Hancitor malware, a loader recognized for dropping or executing stealers, corresponding to Distant Entry Trojans (RATs) and different kinds of ransomware, onto victims’ networks,” in response to a December 2021 alert from the U.S. Federal Bureau of Investigation (FBI).
“Hancitor malware actors use phishing emails, Microsoft Change vulnerabilities, compromised credentials, or respectable Distant Desktop Protocol (RDP) instruments to achieve preliminary entry to a sufferer’s community.”
Within the intervening months, the ransomware operation has obtained an improve with an intention to “optimize its execution, reduce unintended system habits, and supply technical assist to the ransomware victims in the event that they select to barter,” per Development Micro.
Chief among the many adjustments encompassed terminating extra processes earlier than encryption (viz Microsoft Outlook, Change, and MySQL), increasing the file sorts to be excluded, and revision to its ransom word to supply sufferer assist by way of quTox.
Tropical Scorpius can also be believed to share connections with a knowledge extortion market referred to as Industrial Spy, as reported by Bleeping Laptop in Might 2022, with the exfiltrated information following a Cuba ransomware assault posted on the market on the illicit portal as a substitute of its personal information leak website.
The newest updates noticed by Unit 42 in Might 2022 has to do with the protection evasion ways employed previous to the deployment of the ransomware to fly below the radar and transfer laterally throughout the compromised IT atmosphere.
“Tropical Scorpius leveraged a dropper that writes a kernel driver to the file system referred to as ApcHelper.sys,” the corporate famous. “This targets and terminates safety merchandise. The dropper was not signed, nevertheless, the kernel driver was signed utilizing the certificates discovered within the LAPSUS$ NVIDIA leak.”
The primary job of the kernel driver is to terminate processes related to safety merchandise in order to bypass detection. Additionally included within the assault chain is an area privilege escalation device downloaded from a distant server to achieve SYSTEM permissions.
This, in flip, is achieved by triggering an exploit for CVE-2022-24521 (CVSS rating: 7.8), a flaw within the Home windows Frequent Log File System (CLFS) that was patched by Microsoft as a zero-day flaw in April 2022.
The privilege escalation step is adopted by finishing up system reconnaissance and lateral motion actions by instruments like ADFind and Internet Scan, whereas additionally utilizing a ZeroLogon utility that exploits CVE-2020-1472 to achieve area administrator rights.
Moreover, the intrusion paves the way in which for the deployment of a novel backdoor referred to as ROMCOM RAT, which is supplied to begin a reverse shell, delete arbitrary information, add information to a distant server, and harvest a listing of operating processes.
The distant entry trojan, per Unit 42, is alleged to be below energetic growth, because the cybersecurity agency found a second pattern uploaded to the VirusTotal database on June 20, 2022.
The improved variant comes with assist for a broadened set of twenty-two instructions, counting the flexibility to obtain bespoke payloads to seize screenshots in addition to extract a listing of all put in functions to ship again to the distant server.
“Tropical Scorpius stays an energetic risk,” the researchers stated. “The group’s exercise makes it clear that an method to tradecraft utilizing a hybrid of extra nuanced instruments specializing in low-level Home windows internals for protection evasion and native privilege escalation may be extremely efficient throughout an intrusion.
The findings come as rising ransomware teams corresponding to Stormous, Vice Society, Luna, SolidBit, and BlueSky are persevering with to proliferate and evolve within the cybercrime ecosystem, on the identical utilizing superior encryption methods and supply mechanisms.
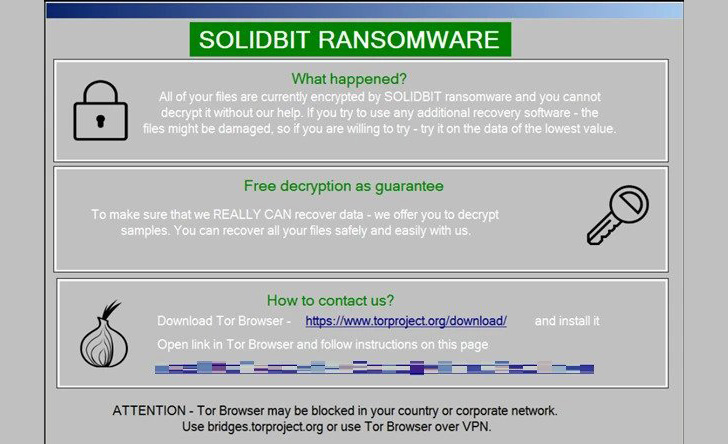
SolidBit stands out for its concentrating on of customers of in style video video games and social media platforms by masquerading as totally different functions like a League of Legends account checker device and instruments like Social Hacker and Instagram Follower Bot, permitting the actors to solid a large internet of potential victims.
“SolidBit ransomware is compiled utilizing .NET and is definitely a variant of Yashma ransomware, also referred to as Chaos,” Development Micro famous in a write-up final week.
“It is potential that SolidBit’s ransomware actors are presently working with the unique developer of Yashma ransomware and certain modified some options from the Chaos builder, later rebranding it as SolidBit.”
BlueSky, for its half, is understood to make the most of multithreading to encrypt information on the host for sooner encryption, to not point out undertake anti-analysis methods to obfuscate its look.
The ransomware payload, which kicks off with the execution of a PowerShell script retrieved from an attacker-controlled server, additionally disguises itself as a respectable Home windows utility (“javaw.exe”).
“Ransomware authors are adopting trendy superior methods corresponding to encoding and encrypting malicious samples, or utilizing multi-staged ransomware supply and loading, to evade safety defenses,” Unit 42 famous.
“BlueSky ransomware is able to encrypting information on sufferer hosts at speedy speeds with multithreaded computation. As well as, the ransomware adopts obfuscation methods, corresponding to API hashing, to decelerate the reverse engineering course of for the analyst.”