Malicious actors have been noticed abusing respectable adversary simulation software program of their assaults in an try to remain underneath the radar and evade detection.
Palo Alto Networks Unit 42 stated a malware pattern uploaded to the VirusTotal database on Might 19, 2022, contained a payload related to Brute Ratel C4, a comparatively new refined toolkit “designed to keep away from detection by endpoint detection and response (EDR) and antivirus (AV) capabilities.”
Authored by an Indian safety researcher named Chetan Nayak, Brute Ratel (BRc4) is analogous to Cobalt Strike and is described as a “custom-made command-and-control middle for pink group and adversary simulation.”
The industrial software program was first launched in late 2020 and has since gained over 480 licenses throughout 350 prospects. Every license is obtainable at $2,500 per person for a yr, after which it may be renewed for a similar period at the price of $2,250.
BRc4 is supplied with all kinds of options, akin to course of injection, automating adversary TTPs, capturing screenshots, importing and downloading information, assist for a number of command-and-control channels, and the flexibility to maintain reminiscence artifacts hid from anti-malware engines, amongst others.
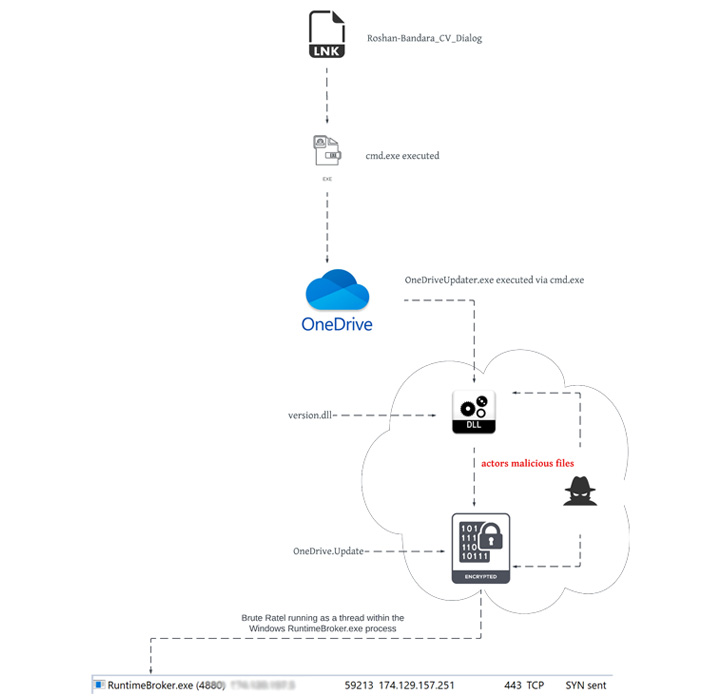
The artifact, which was uploaded from Sri Lanka, masquerades as a curriculum vitae of a person named Roshan Bandara (“Roshan_CV.iso”) however in actuality is an optical disc picture file that, when double-clicked, mounts it as a Home windows drive containing a seemingly innocent Phrase doc that, upon launching, installs BRc4 on the person’s machine and establishes communications with a distant server.
The supply of packaged ISO information is often despatched by way of spear-phishing e mail campaigns, though it isn’t clear if the identical technique was used to ship the payload to the goal atmosphere.
“The composition of the ISO file, Roshan_CV.ISO, carefully resembles that of different nation-state APT tradecraft,” Unit 42 researchers Mike Harbison and Peter Renals stated, calling out similarities to that of a packaged ISO file beforehand attributed to Russian nation-state actor APT29 (aka Cozy Bear, The Dukes, or Iron Hemlock).
APT29 rose to notoriety final yr after the state-sponsored group was blamed for orchestrating the large-scale SolarWinds provide chain assault.
The cybersecurity agency famous it additionally noticed a second pattern that was uploaded to VirusTotal from Ukraine a day later and which exhibited code overlaps to that of a module chargeable for loading BRc4 in reminiscence. The investigation has since unearthed seven extra BRc4 samples courting again to February 2021.
That is not all. By analyzing the C2 server that was used as a covert channel, quite a lot of potential victims have been recognized. This contains an Argentinian group, an IP tv supplier offering North and South American content material, and a significant textile producer in Mexico.
“The emergence of a brand new penetration testing and adversary emulation functionality is important,” the researchers stated. “But extra alarming is the effectiveness of BRc4 at defeating fashionable defensive EDR and AV detection capabilities.”
Shortly after the findings turned public, Nayak tweeted that “correct actions have been taken towards the discovered licenses which had been offered within the black market,” including BRc4 v1.1 “will change each side of IoC discovered within the earlier releases.”