Final Thursday, one among Australia’s largest telecommunications and broadband suppliers, Optus, disclosed a cyberattack that compromised buyer knowledge. Whereas the knowledge breach befell every week in the past, the story continues to develop. Because it at present stands, a menace actor accessed the private data of as many as 11.2 million previous and current Optus clients, together with clients of its subsidiaries Virgin Cellular and Gomo. The sheer variety of affected people makes this Australia’s largest ever knowledge breach. Nevertheless, in a considerably stunning twist, the actor who claims to be behind this incident retracted his knowledge extortion scheme, allegedly deleted his copy of the info, and apologized for ever having stolen it.
Hacker Claims Knowledge From 11.2 Million Optus Prospects Stolen
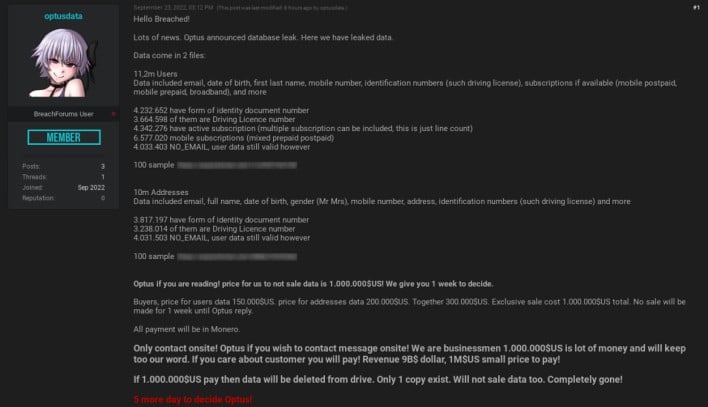
A day after Optus disclosed the info breach, an unknown actor posted to the hacking web site Breach Boards underneath the identify “optusdata.” The discussion board person began a thread wherein he claimed to own buyer knowledge stolen from Optus within the knowledge breach. The proprietor and administrator of Breach Boards, pompompurin, replied to the thread saying he verified the authenticity of the person’s claims by talking with him and viewing a pattern of the info.
In accordance with the unique discussion board publish, the menace actor stole knowledge pertaining to 11.2 million Optus clients. The publish hyperlinks to 2 samples of the info, which embody names, dates of start, electronic mail addresses, telephone numbers, residence addresses, driver’s license numbers, passport numbers, Medicare ID numbers, and subscription data.
Optus has since issued a assertion indicating that 9.8 million buyer information had been uncovered. Nevertheless, the corporate additionally not too long ago knowledgeable clients of Virgin Cellular and Gomo that their private data was included on this knowledge breach, and it’s unclear whether or not these clients are included in that 9.8 million. Whereas Virgin Cellular and Gomo are each subsidiaries of Optus, not the entire firm’s subsidiaries had been affected. In accordance with reporter Josh Taylor, Amaysim clients weren’t affected by this breach.
Optus Denies The Breach Was Due To “Human Error”
An unnamed “senior determine” inside Optus instructed ABC Information that the breach seems to have been the results of human error. Extra particularly, the interior Optus buyer database was related to an Software Programming Interface (API) that was uncovered to the open net by means of “a take a look at community which occurred to have web entry.” This rationalization of the breach was corroborated by optusdata, who spoke with reporter Jeremy Kirk on Breach Boards. Kirk shared screenshots from his dialog with the menace actor, who stated that he accessed the database by means of an API discovered at an easily-guessable net handle. This handle appears to be legit, because it seems in GitHub repositories courting way back to 2018.
What’s extra, optusdata instructed Kirk that the API endpoint was unauthenticated, which means it was unprotected by any type of login credentials. It’s doable that this API was protected by authentication up to now and solely not too long ago grew to become unprotected previous to the breach. Optus seems to have responded to the info breach by taking the API offline. Nevertheless, in correspondence with ABC Information, Optus instantly denied the declare that human error was at fault for the breach, with the CEO insisting that the corporate has “very robust cyber defenses.” Optus as a substitute attributed the breach to a “subtle” cyberattack, however didn’t present any extra particulars.
Both approach, the info breach grew to become instrumental to an extortion scheme. At first, the menace actor tried to extort Optus by threatening to promote the stolen knowledge to 3rd occasion actors if the corporate didn’t pay a $1 million ransom charge. Nevertheless, a number of days after optusdata issued this ultimatum, Optus clients caught up within the knowledge breach started receiving sudden SMS messages. The messages directed their recipients to switch $2000AUD to a Commonwealth Financial institution of Australia account underneath the identify “OptusData” to have their data wiped from the stolen database earlier than it’s offered. The financial institution responded by issuing a rip-off alert and blocking this account.
It isn’t clear that the menace actor trying to extort Optus clients instantly is similar actor because the one answerable for the info breach. An unrelated actor may have used the data launched within the knowledge samples to contact Optus clients in an try and rip-off them out of their cash with none capacity to observe by means of with the promise to erase their private data from the stolen database.
Chilly Ft?
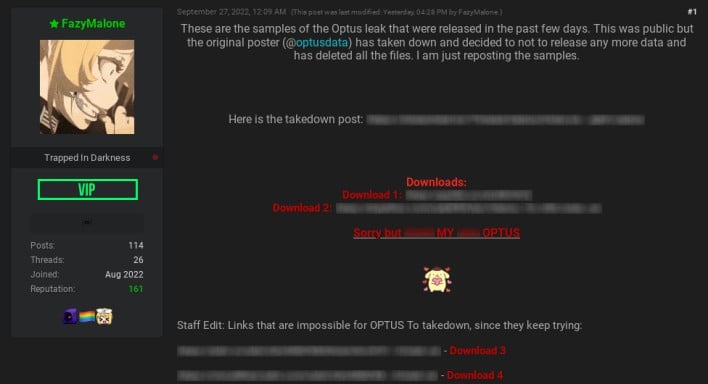
Regardless, nearly the entire stolen knowledge might have been deleted with out both Optus or its clients paying a single cent. On Tuesday, optusdata deleted the unique discussion board thread saying the info breach and changed it with a brand new thread saying that the stolen Optus knowledge gained’t be offered or leaked to anybody. The publish affords repeated apologies and states that the one copy of the stolen knowledge has been deleted. Some Breach Boards customers speculated that Optus ended up paying the ransom charge in spite of everything, however reporter Jeremy Kirk obtained affirmation from Optus that the corporate didn’t pay a ransom.
A probable rationalization for the sudden change of coronary heart is that the menace actor started to really feel the strain of regulation enforcement. In accordance with the discussion board publish, the info breach drew an excessive amount of consideration, making it not possible to promote the info. This retraction got here lower than a day after the Australian Federal Police introduced “Operation Hurricane” with the acknowledged aim of figuring out the cybercriminals behind the Optus breach and stopping id fraud. The Australian authorities additionally reportedly referred to as within the US Federal Bureau of Investigation (FBI) for assist.
Some Irreversible Harm Is Performed
Sadly for a small subset of Optus clients, the info samples revealed within the unique discussion board publish dwell on. The samples proceed to be out there for obtain from one other Breach Boards person who has reposted them in a brand new discussion board thread. These samples listing the private data of 10,200 Optus clients, placing them susceptible to id fraud.
We additionally haven’t any affirmation at this level that the bigger stolen database was truly deleted, so Optus clients shouldn’t merely shrug off the info breach. The stolen database may present up at one other time, so Optus clients ought to take precautionary measures. Fortuitously, state governments are working to help Australians affected by the breach, with many providing methods for folks to extra simply purchase new driver’s licenses. Optus has even pledged to pay driver’s license alternative charges for residents of New South Wales.
Past driver’s licenses, the Australian Minister for Overseas Affairs, Penny Wong, has despatched Optus a letter requesting that the corporate cowl the price of new passports for purchasers affected by the breach. The Australian Federal Police additionally simply introduced a joint operation with all State and Territory police, the Australian Cyber Safety Centre, the Australian Banking Affiliation, IDCARE and the Buyer Owned Banking Affiliation. Named Operation Guardian, the coordinated effort is meant to establish the ten,200 Optus clients whose data was leaked within the knowledge samples and supply them with extra protections.