E-commerce industries in South Korea and the U.S. are on the receiving finish of an ongoing GuLoader malware marketing campaign, cybersecurity agency Trellix disclosed late final month.
The malspam exercise is notable for transitioning away from malware-laced Microsoft Phrase paperwork to NSIS executable information for loading the malware. Different nations focused as a part of the marketing campaign embrace Germany, Saudi Arabia, Taiwan and Japan.
NSIS, brief for Nullsoft Scriptable Set up System, is a script-driven open supply system used to develop installers for the Home windows working system.
Whereas assault chains in 2021 leveraged a ZIP archive containing a macro-laced Phrase doc to drop an executable file tasked with loading GuLoader, the brand new phishing wave employs NSIS information embedded inside ZIP or ISO photographs to activate the an infection.
“Embedding malicious executable information in archives and pictures will help menace actors evade detection,” Trellix researcher Nico Paulo Yturriaga mentioned.
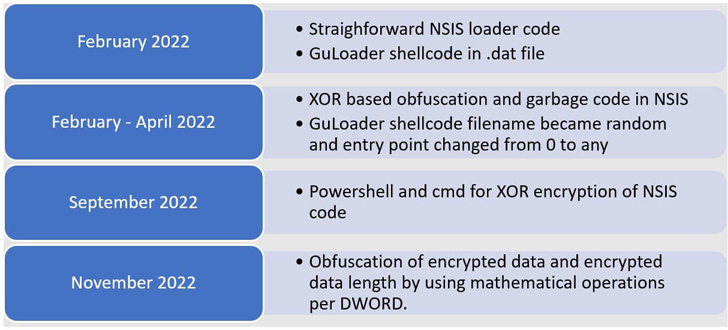
Over the course of 2022, the NSIS scripts used to ship GuLoader are mentioned to have grown in sophistication, packing in extra obfuscation and encryption layers to hide the shellcode.
The event can also be emblematic of a broader shift inside the menace panorama, which has witnessed spikes in different malware distribution strategies in response to Microsoft’s blocking of macros in Workplace information downloaded from the web.
“The migration of GuLoader shellcode to NSIS executable information is a notable instance to indicate the creativity and persistence of menace actors to evade detection, forestall sandbox evaluation and impede reverse engineering,” Yturriaga famous.