The operators of the Gootkit access-as-a-service (AaaS) malware have resurfaced with up to date methods to compromise unsuspecting victims.
“Prior to now, Gootkit used freeware installers to masks malicious information; now it makes use of authorized paperwork to trick customers into downloading these information,” Development Micro researchers Buddy Tancio and Jed Valderama mentioned in a write-up final week.
The findings construct on a earlier report from eSentire, which disclosed in January of widespread assaults geared toward staff of accounting and legislation companies to deploy malware on contaminated programs.
Gootkit is a part of the proliferating underground ecosystem of entry brokers, who’re recognized to offer different malicious actors a pathway into company networks for a value, paving the best way for precise damaging assaults similar to ransomware.
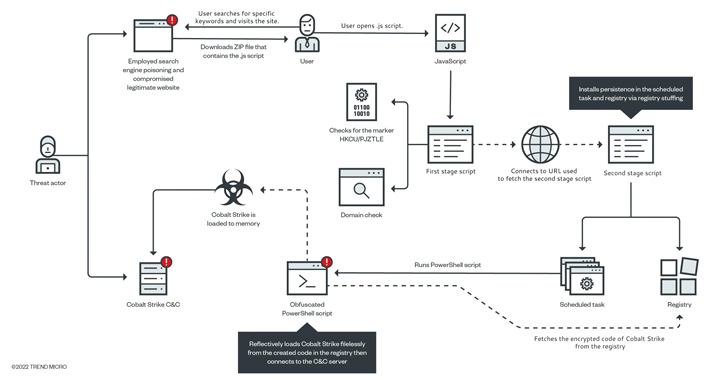
The loader makes use of malicious search engine outcomes, a method known as search engine marketing poisoning, to lure unsuspecting customers into visiting compromised web sites internet hosting malware-laced ZIP package deal information purportedly associated to disclosure agreements for actual property transactions.
“The mix of search engine marketing poisoning and compromised respectable web sites can masks indicators of malicious exercise that may often hold customers on their guard,” the researchers identified.
The ZIP file, for its half, features a JavaScript file that masses a Cobalt Strike binary, a instrument used for post-exploitation actions that run straight within the reminiscence filelessly.
“Gootkit continues to be lively and enhancing its methods,” the researchers mentioned. “This suggests that this operation has confirmed efficient, as different risk actors appear to proceed utilizing it.”