An Web Explorer zero-day vulnerability was actively exploited by a North Korean risk actor to focus on South Korean customers by capitalizing on the current Itaewon Halloween crowd crush to trick customers into downloading malware.
The invention, reported by Google Menace Evaluation Group researchers Benoît Sevens and Clément Lecigne, is the most recent set of assaults perpetrated by ScarCruft, which can also be referred to as APT37, InkySquid, Reaper, and Ricochet Chollima.
“The group has traditionally targeted their concentrating on on South Korean customers, North Korean defectors, coverage makers, journalists, and human rights activists,” TAG mentioned in a Thursday evaluation.
The brand new findings illustrate the risk actor’s continued abuse of Web Explorer flaws similar to CVE-2020-1380 and CVE-2021-26411 to drop backdoors like BLUELIGHT and Dolphin, the latter of which was disclosed by Slovak cybersecurity agency ESET late final month.
One other key instrument in its arsenal is RokRat, a Home windows-based distant entry trojan that comes with a variety of features that permit it to seize screenshots, log keystrokes, and even harvest Bluetooth system data.
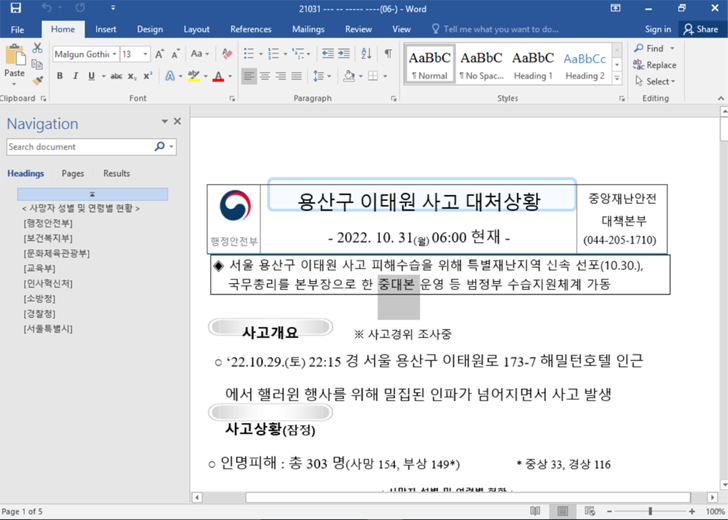
The assault chain noticed by Google TAG entails using a malicious Microsoft Phrase doc that was uploaded to VirusTotal on October 31, 2022. It abuses one more Web Explorer zero-day flaw within the JScript9 JavaScript engine, CVE-2022-41128, that was patched by Microsoft final month.
The file references the October 29 incident that befell within the Itaewon neighborhood of Seoul and exploits public curiosity within the tragedy to retrieve an exploit for the vulnerability upon opening it. The assault is enabled by the truth that Workplace renders HTML content material utilizing Web Explorer.
Profitable exploitation is adopted by the supply of a shellcode that wipes all traces by clearing the Web Explorer cache and historical past in addition to downloading the subsequent stage payload.
Google TAG mentioned it couldn’t get well the follow-on malware used within the marketing campaign, though it is suspected to have concerned the deployment of RokRat, BLUELIGHT, or Dolphin.