Sadly, there’s not an entire lot of details about the zero-day exploit at concern. All we all know is that it is tracked as CVE-2022-3075. It has a “Excessive” severity ranking and is described as an “inadequate knowledge validation in Mojo” exploit. Critically, nonetheless, Google plainly states it’s “conscious of experiences that an exploit for CVE-2022-3075 exists within the wild.”
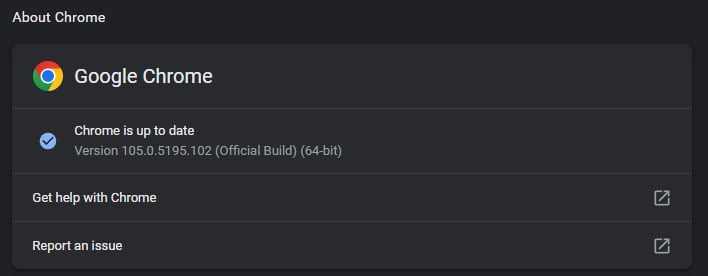
There are billions (plural) of Chrome customers. Anybody who has not but up to date to the most recent secure construct on the time of this writing (model 105.0.5195.102 on Home windows, Mac, and Linux) is probably weak to no matter this zero-day entails.
For anybody questioning, Mojo is a set of runtime libraries that present a small suite of low-level IPC primitives (message pipes, knowledge pipes, and shared buffers). The patch for the actively exploited zero day leveraging a flaw in Mojo arrives simply days after Google pushed out Chrome model 105, which itself contained a pair dozen unrelated bug fixes.
To facilitate a guide replace, click on on the three vertical dots within the upper-right nook of Chrome and navigate to Assist > About Google Chrome. The browser will then test for and fetch the most recent replace. It immediate you to relaunch the browser to finish its set up if an replace is accessible.
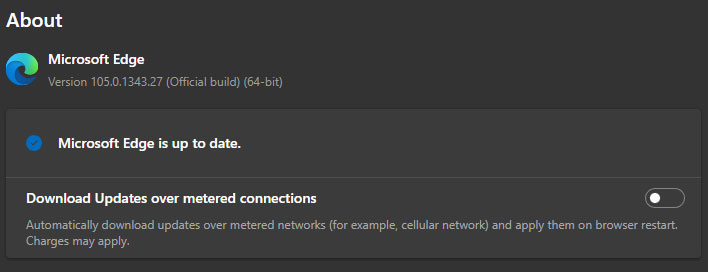
To use the replace in Edge, click on on the three horizontal dots within the upper-right nook, then go to Assist and suggestions > About Microsoft Edge.


