Google on Tuesday introduced the open supply availability of OSV-Scanner, a scanner that goals to supply quick access to vulnerability details about varied initiatives.
The Go-based device, powered by the Open Supply Vulnerabilities (OSV) database, is designed to attach “a mission’s record of dependencies with the vulnerabilities that have an effect on them,” Google software program engineer Rex Pan in a publish shared with The Hacker Information.
“The OSV-Scanner generates dependable, high-quality vulnerability data that closes the hole between a developer’s record of packages and the knowledge in vulnerability databases,” Pan added.
The concept is to determine all of the transitive dependencies of a mission and spotlight related vulnerabilities utilizing information pulled from OSV.dev database.
Google additional acknowledged that the open supply platform helps 16 ecosystems, counting all main languages, Linux distributions (Debian and Alpine), in addition to Android, Linux Kernel, and OSS-Fuzz.
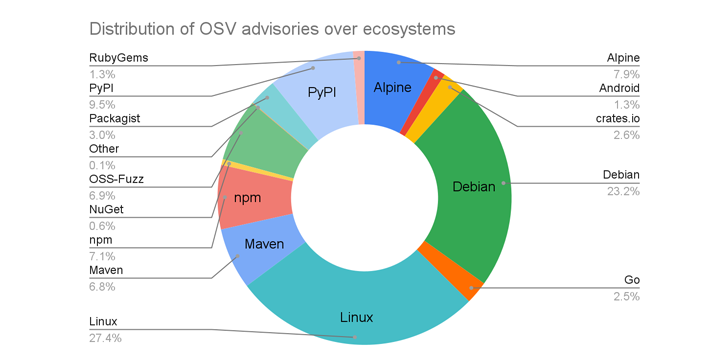
The results of this growth is that OSV.dev is a repository to greater than 38,000 advisories, up from 15,000 safety alerts a 12 months in the past, with Linux (27.4%), Debian (23.2%), PyPI (9.5%), Alpine (7.9%), and npm (7.1%) taking over the highest 5 slots.
As for the following steps, the web big famous it is working to include help for C/C++ flaws by constructing a “prime quality database” that entails including “exact commit degree metadata to CVEs.”
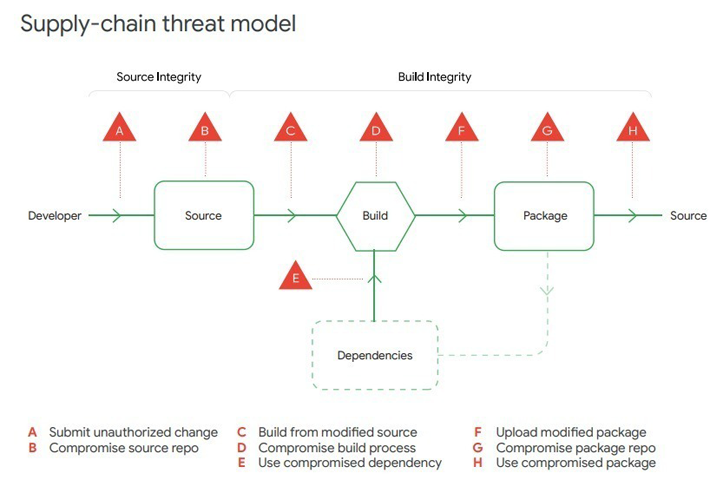
OSV-Scanner arrives practically two months after Google launched GUAC – quick for Graph for Understanding Artifact Composition – to enrich Provide chain Ranges for Software program Artifacts (SLSA or “salsa”) as a part of its efforts to harden software program provide chain safety.
Final week, Google additionally revealed a brand new “Views on Safety” report calling on organizations to develop and deploy a standard SLSA framework to forestall tampering, enhance integrity, and safe packages in opposition to potential threats.
Different suggestions laid out by the corporate embrace taking up further open supply safety obligations and adopting a extra holistic method to addressing dangers comparable to these introduced by the Log4j vulnerability and the SolarWinds incident in recent times.
“Software program provide chain assaults usually require sturdy technical aptitude and long-term dedication to tug off,” the corporate mentioned. “Refined actors usually tend to have each the intent and functionality to conduct these kind of assaults.”
“Most organizations are susceptible to software program provide chain assaults as a result of attackers take the time to focus on third-party suppliers with trusted connections to their clients’ networks. They then use that belief to burrow deeper into the networks of their final targets.”