Expertise corporations akin to NSO Group develop spyware and adware and promote it to state actors all inside the bounds of the regulation. These teams keep that the spyware and adware is to be used by approved authorities authorities solely, however latest historical past appears to point out that unintended actors have managed to deploy this sort of spyware and adware. Final 12 months, an investigation discovered that NSO Group’s Pegasus spyware and adware had contaminated the telephones of at the least 9 US State Division workers, main NSO Group to launch its personal investigation into this use of its spyware and adware.
Now Google’s Menace Evaluation Group (TAG) has found a special spyware and adware marketing campaign focusing on Android and iOS customers in Italy and Kazakhstan. Researchers at Lookout Menace Lab dubbed this spyware and adware “Hermit” and attribute it to RCS Labs, which is an Italian spyware and adware vendor. RCS prides itself on being “the main European supplier of full lawful interception companies.” The Hermit spyware and adware has been deployed earlier than, however this new marketing campaign includes a significantly alarming tactic.
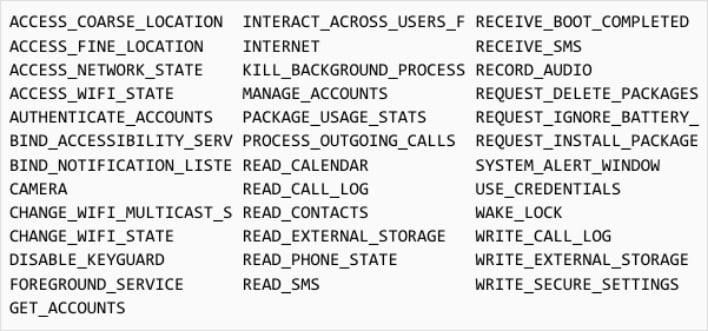
These malicious apps weren’t ever obtainable on the Google Play Retailer or Apple App Retailer, however had been as an alternative side-loaded from web sites managed by the attackers. As soon as put in, the malicious iOS apps exploited at the least six completely different safety vulnerabilities, together with two zero-day exploits. The malicious Android apps, alternatively, didn’t immediately exploit any vulnerabilities themselves, however requested entry to numerous permissions, as proven above, and communicated with the menace actors’ command-and-control (C2) servers. The Android apps might retrieve extra malicious payloads from the C2 servers and set up them on contaminated units.
Google has responded to this spyware and adware marketing campaign by warning all Android victims, implementing Google Play Shield modifications, and disabling the Firebase Cloud Messaging initiatives that had been getting used as C2 servers. Whereas we nonetheless don’t know who was behind this spyware and adware marketing campaign, all the web sites that distributed the malicious apps have since been taken down, so the marketing campaign is hopefully over for now.


