Google’s Menace Evaluation Group (TAG) on Thursday disclosed it had acted to dam as many as 36 malicious domains operated by hack-for-hire teams from India, Russia, and the U.A.E.
In a way analogous to the surveillanceware ecosystem, hack-for-hire corporations equip their purchasers with capabilities to allow focused assaults geared toward corporates in addition to activists, journalists, politicians, and different high-risk customers.
The place the 2 stand aside is that whereas prospects buy the spyware and adware from business distributors after which deploy it themselves, the operators behind hack-for-hire assaults are recognized to conduct the intrusions on their purchasers’ behalf with a view to obscure their function.
“The hack-for-hire panorama is fluid, each in how the attackers arrange themselves and within the wide selection of targets they pursue in a single marketing campaign on the behest of disparate purchasers,” Shane Huntley, director of Google TAG, stated in a report.
“Some hack-for-hire attackers brazenly promote their services and products to anybody prepared to pay, whereas others function extra discreetly promoting to a restricted viewers.”
A latest marketing campaign mounted by an Indian hack-for-hire operator is alleged to have focused an IT firm in Cyprus, an schooling establishment in Nigeria, a fintech firm within the Balkans, and a buying firm in Israel, indicating the breadth of victims.
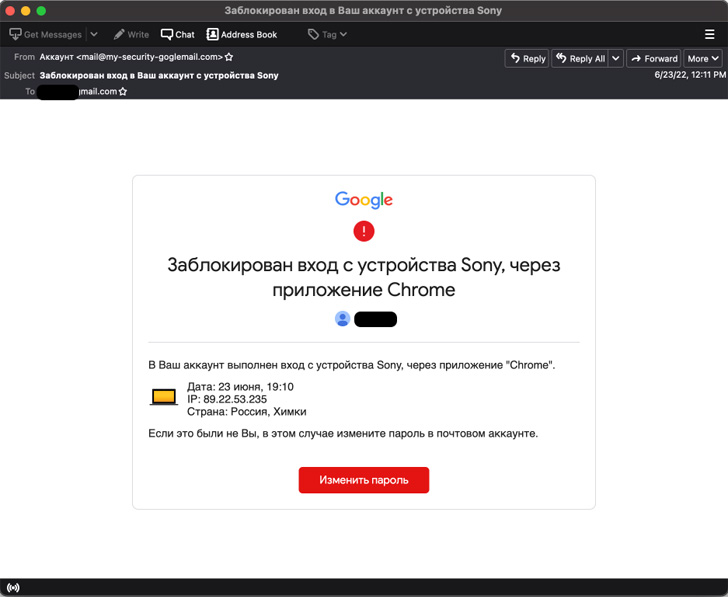
The Indian outfit, which Google TAG stated it has been monitoring since 2012, has been linked to a string of credential phishing assaults with the aim of harvesting login data related to authorities businesses, Amazon Internet Providers (AWS), and Gmail accounts.
The marketing campaign includes sending spear-phishing emails containing a rogue hyperlink that, when clicked, launches an attacker-controlled phishing web page designed to siphon credentials entered by unsuspecting customers. Targets included authorities, healthcare, and telecom sectors in Saudi Arabia, the United Arab Emirates, and Bahrain.
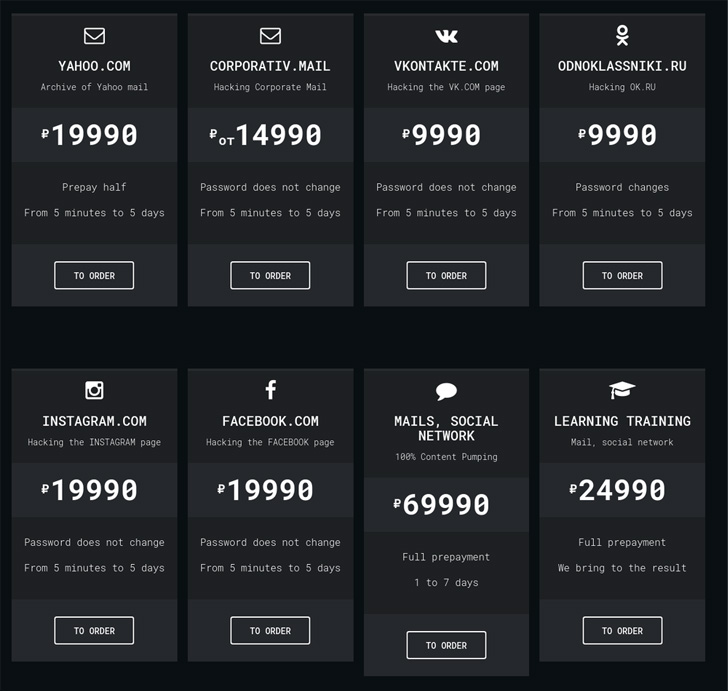
Google TAG attributed the Indian hack-for-hire actors to a agency referred to as Rebsec, which, in line with its dormant Twitter account, is brief for “Rebel Securities” and is predicated within the metropolis of Amritsar. The corporate’s web site, down for “upkeep” as of writing, additionally claims to supply company espionage companies.
An analogous set of credential theft assaults concentrating on journalists, European politicians, and non-profits has been linked to a Russian actor dubbed Void Balaur, a cyber mercenary group first documented by Pattern Micro in November 2021.
Over the previous 5 years, the collective is believed to have singled out accounts at main webmail suppliers like Gmail, Hotmail, and Yahoo! and regional webmail suppliers like abv.bg, mail.ru, inbox.lv, and UKR.internet.
Lastly, TAG additionally detailed the actions of a bunch primarily based within the U.A.E. and has connections to the unique builders of a distant entry trojan referred to as njRAT (aka H-Worm or Houdini).
The phishing assaults, as beforehand uncovered by Amnesty Worldwide in 2018, entail utilizing password reset lures to steal credentials from targets in authorities, schooling, and political organizations within the Center East and North Africa.
Following the account compromise, the menace actor maintains persistence by granting an OAuth token to a professional e mail utility like Thunderbird, producing an App Password to entry the account by way of IMAP, or linking the sufferer’s Gmail account to an adversary-owned account on a third-party mail supplier.
The findings come every week after Google TAG revealed particulars of an Italian spyware and adware firm named RCS Lab, whose “Hermit” hacking instrument was used to focus on Android and iOS customers in Italy and Kazakhstan.