ACM.17 Making a reusable KSM Key Template for Batch Jobs
This can be a continuation of my sequence of posts on Automating Cybersecurity Metrics.
The objective of this put up is to create a template that we are able to use to generically create new KMS keys with completely different principals who’re allowed to make use of the important thing to encrypt and decrypt information.
How is a generic template useful?
- You’ll be able to forestall human error when deploying assets by creating issues with normal, accepted templates.
- Organizations might have a separate staff and account the place they handle encryption keys, comparable to I’ve written about in a previous put up.
- You might write a self-service perform or job that permits individuals to deploy their very own encryption keys, which doesn’t allow them to change the important thing administrator, however does permit the to specify who can encrypt and decrypt the information from an outlined set of individuals which are allowed to entry information within the deployment surroundings.
- You need to use the identical template all through your software program growth lifecycle (SDLC) with out having to vary the code. The identical template might be deployed in dev, QA, and manufacturing, however you swap out the parameters.
In some instances the encrypt and decrypt principal will probably be one and the identical. Our generic template will permit us to go in a job ARN for the encrypt and the decrypt principal.
Keys can have a single key administrator function. On this case we’re presuming that there’s a consumer or group that may assume a job to create or administer KMS keys however these principals to not have permission to encrypt or decrypt information.
This earlier put up describes the potential KMS structure the place the KMS keys are created in a stand-alone account, managed by particular key directors.
Key Administrator Position
We are going to want a create a KMS key administrator function that we are able to use go into our KMS key template. While you create a KMS key manually within the AWS console you’ve the choice to pick out KMS key directors.

Subsequent you choose the individuals who can use the important thing (encrypt and decrypt):

Then you find yourself with a key coverage. A part of that key coverage will assign permissions to the important thing directors. We’ll use these permissions of the idea of the important thing administrator function we create. In case you don’t need your key directors to have any of the permissions beneath, comparable to the flexibility to delete keys, you’ll be able to take away them.
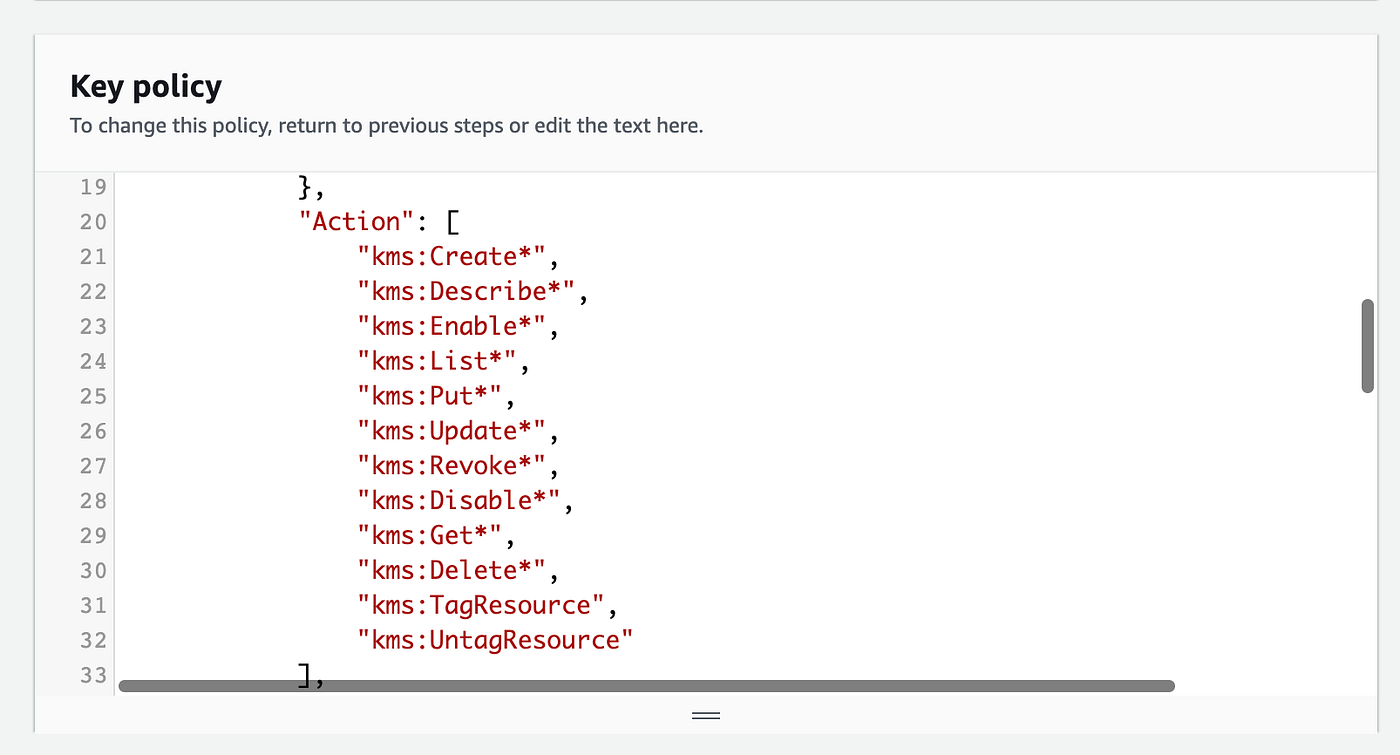
For testing functions, I’ll assume this function from an EC2 instanced deployed in one other account utilizing an AWS CLI Profile.
The consumer within the different account will must be allowed to imagine the function with MFA to deploy the KMS key. Meaning the distant consumer will want the identical STS AssumeRole permissions we gave our batch job consumer on this put up:
Add a parameter for the consumer ARN that’s allowed to imagine the function:

Since we’re utilizing MFA right here, the consumer will, sadly, have so as to add credentials to the EC2 occasion in an effort to assume the function and use MFA. Hopefully we’ll resolve that concern with the way in which we’re designing our batch jobs and we are able to transfer this KMS key creation course of to a batch job sooner or later. TBD.
KMS Key Customers — Encryption and Decryption
Right here is our KMS Key template thus far. Parameters embrace a singular id and outline, a rotation parameter (true or false) which signifies whether or not we wish key rotation. If you’re defending delicate information it’s a good suggestion to rotate your encryption keys no less than as soon as per yr. You’ll pay for every model of key materials KMS shops.
As well as we’ll go in two ARNs — one for the consumer allowed to decrypt with the important thing and one of many consumer allowed to encrypt with the important thing. Word that the important thing administrator is retrieved from the outputs of the kms key administrator function.
Word that the important thing administrator function is retrieved from the outputs of our KMS administrator function template.

Now we should always be capable to deploy KMS keys in a typical method, however we’ll want to check this out with an precise use case. After I wrote this I figured I might most likely have to repair some bugs and typos once I examined this code out. Because it seems I made some further adjustments to this code as I believed by the structure together with how I would want to deploy this template and the way the important thing could be used. Observe me for updates.
Teri Radichel
In case you favored this story please clap and observe:
Medium: Teri Radichel or Electronic mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts


