Fortinet on Monday issued emergency patches for a extreme safety flaw affecting its FortiOS SSL-VPN product that it mentioned is being actively exploited within the wild.
Tracked as CVE-2022-42475 (CVSS rating: 9.3), the crucial bug pertains to a heap-based buffer overflow vulnerability that might enable an unauthenticated attacker to execute arbitrary code through specifically crafted requests.
The corporate mentioned it is “conscious of an occasion the place this vulnerability was exploited within the wild,” urging prospects to maneuver rapidly to use the updates.
The next merchandise are impacted by the problem –
- FortiOS model 7.2.0 by 7.2.2
- FortiOS model 7.0.0 by 7.0.8
- FortiOS model 6.4.0 by 6.4.10
- FortiOS model 6.2.0 by 6.2.11
- FortiOS-6K7K model 7.0.0 by 7.0.7
- FortiOS-6K7K model 6.4.0 by 6.4.9
- FortiOS-6K7K model 6.2.0 by 6.2.11
- FortiOS-6K7K model 6.0.0 by 6.0.14
Patches can be found in FortiOS variations 7.2.3, 7.0.9, 6.4.11, and 6.2.12 in addition to FortiOS-6K7K variations 7.0.8, 6.4.10, 6.2.12, and 6.0.15.
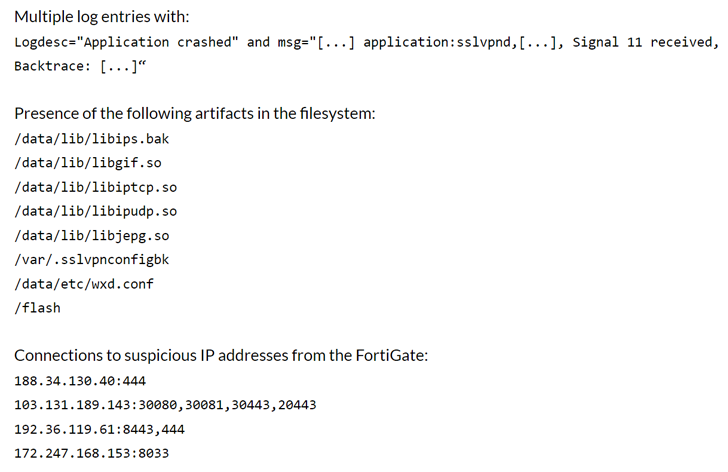
The American community safety firm has additionally printed indicators of compromise (IoCs) related to the exploitation makes an attempt, together with the IP addresses and the artifacts which are current within the file system publish a profitable assault.
The advisory comes two months after Fortinet warned of energetic weaponization of one other crucial authentication bypass bug in FortiOS, FortiProxy, and FortiSwitchManager (CVE-2022-40684, CVSS rating: 9.6).