Cryptography is the research of knowledge safety by means of Encryption method, which describe the encryption course of and strategies used.
A cipher is an algorithm which is used to encrypt or decrypt the information. Plain textual content is transformed in cipher textual content with assist of this. The remodeling course of is carried out utilizing a key.
This key is sort of a sample to encrypt the information. If we needed to decrypt the information then we have to reverse the method.
Instance:
Think about A is represented as D, and B is represented as E, it means all alphabets are changed with the third subsequent alphabet. Then Apple shall be written as:
A = D
P = S
P = S
L = 0
E = H
So, apple in plain textual content earlier than encryption is APPLE.
This concept or algorithm to exchange the alphabet with third subsequent alphabet is named Cipher.
The third subsequent letter is used to encrypt the information, this secret is taken into account as a key.
If we need to use this above-mentioned cipher then we should know the principles and the important thing.
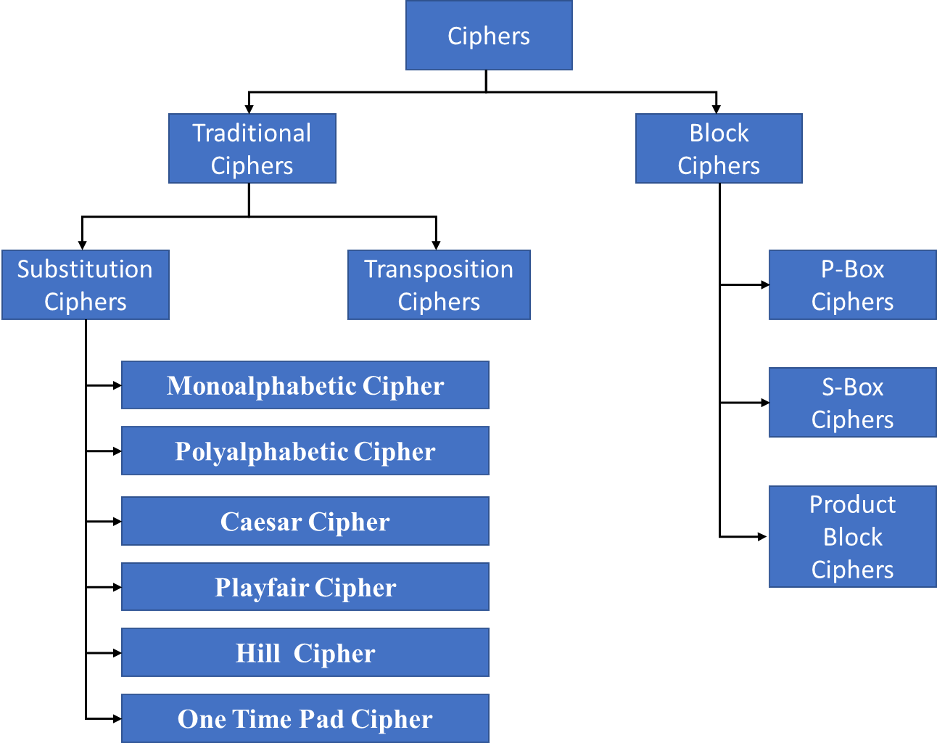
Forms of Ciphers in Cryptography
Primarily there are two varieties of Cipher as given beneath:
- Block Ciphers
- Conventional Ciphers
Block Ciphers
These are new applied sciences. On this a textual content block is remodeled or changed with a cipher textual content block as an alternative of single character transformation.
These are once more divided in three classes:
P-Field or Permutation Field
Transformation or transposition is carried out on bit degree.
Plaintext is remodeled with digital Bits similar to 1 and 0.
The scale needs to be related in each plain textual content or cipher textual content.
S-Field or Substitution Field
Substitution is carried out at bit degree. It comprises three issues:
- Decoder: Decoder remodel n-bit into 2n bit construction.
- P-Field: P-box carry out permutation on this decoded knowledge.
- Encoder: The encoder is used to rework the permuted knowledge into cipher textual content.
Product Block
If we would like extra dependable and safe cipher then we will mix P-Field and S-Field to create new cipher, generally known as Product Block.
It applies each the processing on the plain textual content for transformation into cipher textual content.
Additionally Learn: Forms of Cryptography
Conventional Ciphers
These are the sooner ciphers. These have easy mechanism. Most of conventional ciphers use single alphabet or character as a unit for transformation. Means one plain textual content alphabet is changed with one cipher textual content alphabet.
These are once more divided in two classes:
- Substitution Cipher
- Transposition Cipher
Substitution Ciphers
As title implies the present letter, character, alphabet, quantity, bit is changed by another letter, character, alphabet, quantity, bit as nicely. The alternative possibly utilized on a single character or a block of characters. let’s have a look at their sub components:
1. Monoalphabetic Cipher
Single character is changed with single alternate character all through the entire knowledge set. For instance, if for a specific knowledge set A is taken into account as H, then at everyplace letter A is used, that shall be changed with H.
That is a simple technique however to search out the secret is very tough so this can be a good cipher.
Even we will prepare the entire alphabet set to new alternate values as given beneath:
Instance:
Plain textual content: Cipher is an algorithm.
Cipher textual content: PVCUREVFNANYTBEVGUZ.
2. Polyalphabetic Cipher
On this Vigenere sq. or Vigenere desk is used.
On this desk a number of alternates are present for single character.
The ultimate alternate is relying on the character and the key phrase to encrypt the textual content.
for transformation a key can also be used and this secret is totally different for every dataset.
For instance, take a plain textual content APPLE and the key phrase is RIGHT, so now A is used with R, P is used with I, second P is used with G, L is used with H, and E is used with T.
A = R
P = I
P = G
L = H
E = T
Now for convert A go for row A and column R. the cross worth is R.
Now repeat the method for all of the alphabets so the values are:
A = R
P = X
P = V
L = S
E = X
So, Apple is encrypted as RXVSX.
3. Caesar Cipher
That is quite simple. On this every alphabet is changed with its upcoming third subsequent alphabet.
Instance: A is changed by D, B is changed by E and so forth.
let’s remodel phrase Cipher:
C = F
I = L
P = S
H = Okay
E = H
R = U
So, Cipher is remodeled in FLSKHU.
4. Playfair Cipher
On this a Playfair sq. is used, which is 5 X 5 in dimension.
Steps are as follows:
- First select a key phrase of your personal selection. For instance, select “cipherincryptography” (cipher in cryptography)
- Now enter the characters within the 5 X 5 matrix.
- Keep away from the repeated phrase.
- Fill I and J in a single cell.
A B C D E F G H I J Okay L M N O P Q R S T U V W X Y Z

- Enter the key phrase “cipherincryptography”

- Now enter the remaining alphabets from A B C D E F G H I J Okay L M N O P Q R S T U V W X Y Z

- Now the matrix is prepared.
- For transformation comply with the principles:
- Break the given phrases in alphabet units. Every set ought to have 2 alphabets.
- If in any set each alphabets are related then write the alphabet one time and add X.
- If a single letter is existed then add Z.
- If each alphabets can be found in similar row, then substitute them with their simply subsequent proper alphabet.
- If each alphabets can be found in similar column, then substitute them with their simply subsequent beneath alphabet.
- If each alphabets aren’t in similar row or similar column then swap them with their excellent or left alphabets however with different nook of the dice.
For instance, select phrase Apple:
Apple = AP PL EZ

AP = BI (We will select any both I or J)
PL = IM
EZ = OE
So, Apple is encrypted as BIIMOE.
5. Hill Cipher
It is a complicated mathematical algorithm to encrypt the information.
- First apply numbers to alphabets similar to:

- Then select a key matrix (m*n) dimension.
- Then select the phrase to encrypt.
- Break the phrase in dimension equal to key matrix.
- Now convert the phrase matrix in quantity matrix.
- Now discover the cipher matrix through the use of this formulation:
- C = KP mod 26
Right here C = cipher matrix
Okay = key matrix.
P = phrase matrix
- now remodel the cipher matrix into phrase matrix.
- Comply with the method for the entire knowledge set.
Instance: We select phrase Apple to rework. Convert the alphabets into numbers from the above-mentioned desk.

The scale of phrase matrix is the same as the dimensions of key matrix. Therefore 1 X 2.
Now select a key phrase:
We select CELL as key phrase.
Plot it in matrix. Cell has 4 characters so the matrix shall be 2 X 2 in dimension as given:

Now convert it into quantity matrix:


Repeat the method for different two phrase matrix.
The ultimate transformation shall be appear to be this:

So, that is the tactic of Hill cipher. It’s fairly prolonged and sophisticated.
6. One-time Pad
It’s related like substitution cipher however right here authentic alphabets are changed with the identical dimension key phrase. Means dimension of plain textual content and key phrase is analogous. The key phrases are generated on random foundation. Every key phrase used as soon as solely.
It’s unattainable to crack the code attributable to a number of mixtures.
Transposition Cipher
On this the order of the given phrase is being modified. The given phrases are positioned in a m*n matrix, after which the alphabets are changed with the next alphabet. The interval is chosen as per the important thing.
For instance:
Transposition cipher is hard and the key random key chosen is 6. Now create a matrix with 6 column and required rows.
And place the given string in it.

Now our secret is 6, so substitute T with subsequent 6 alphabet within the given matrix.
So, T = O
Now change the entire string with the identical process.
Plain Textual content Cipher Textual content
Transposition cipher is hard = OSITIONCIPHERISTOUGHTRANSP
Extra Ciphers
1. Polygraphic Cipher
It’s related as substitute cipher, however on this plain textual content blocks are changed with cipher textual content blocks as an alternative of particular person letters or characters.
The plain textual content is split in bigger teams. Every group is changed with similar dimension cipher textual content block.
Playfair and Hill cipher are the instance.
2. Permutation Ciphers
That is fairly reverse of substitute ciphers. On this the plaintext is rearranged in any doable order.
Permutation easy means rearrange the order of characters and alphabets in plain textual content.
Instance:
Hey is a plaintext. Now discover its permutations:
H E Y are three letters so variety of complete doable permutation is:
3 X 2 X 1 = 6
So, let’s discover these 6 permutations manually by rearrange the order.
Now we will use any permutation as an alternative of Hey. That is permutation cipher.
3. Non-public-key Cryptography
On this technique a Non-public secret is used for encryption and decryption.
This key needs to be similar for the encryption or decryption of the identical textual content or knowledge.
This secret is shared between the sender and receiver of the textual content.
4. Public-key Cryptography
On this technique two totally different keys are used for encryption and decryption.
First secret is used to encrypt the plain textual content into cipher textual content. This key is named the Public key.
Second secret is used to decrypt the cipher textual content into plain textual content. This key is named personal key.
Right here we tried to cowl all widespread varieties of ciphers in cryptography. In case you’ve gotten any queries or strategies please point out within the remark part beneath.