The risk actor behind the Fodcha distributed denial-of-service (DDoS) botnet has resurfaced with new capabilities, researchers reveal.
This consists of adjustments to its communication protocol and the power to extort cryptocurrency funds in change for stopping the DDoS assault towards a goal, Qihoo 360’s Community Safety Analysis Lab mentioned in a report printed final week.
Fodcha first got here to gentle earlier this April, with the malware propagating via identified vulnerabilities in Android and IoT units in addition to weak Telnet or SSH passwords.
The cybersecurity firm mentioned that Fodcha has advanced right into a large-scale botnet with over 60,000 lively nodes and 40 command-and-control (C2) domains that may “simply generate greater than 1 Tbps site visitors.”
Peak exercise is alleged to have occurred on October 11, 2022, when the malware focused 1,396 units in a single day.
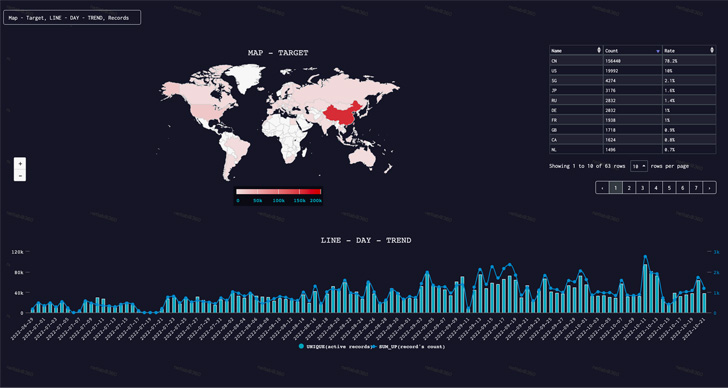
The highest nations singled out by the botnet since late June 2022 includes China, the U.S., Singapore, Japan, Russia, Germany, France, the U.Okay., Canada, and the Netherlands.
Among the outstanding targets vary from healthcare organizations and legislation enforcement businesses to a well known cloud service supplier that was assaulted with site visitors exceeding 1 Tbps.
Fodcha’s evolution has additionally been accompanied by new stealth options that encrypt communications with the C2 server and embed ransom calls for, making it a stronger risk.
“Fodcha reuses plenty of Mirai’s assault code, and helps a complete of 17 assault strategies,” the cybersecurity firm famous.
The findings come as new analysis from Lumen Black Lotus Labs identified the rising abuse of the Connectionless Light-weight Listing Entry Protocol (CLDAP) to amplify the dimensions of DDoS assaults.
To that finish, as many as 12,142 open CLDAP reflectors have been recognized, most of that are distributed within the U.S. and Brazil, and to a lesser extent in Germany, India, and Mexico.
In a single occasion, a CLDAP service related to an unnamed regional retail enterprise in North America has been noticed directing “problematic quantities of site visitors” in direction of a variety of targets for greater than 9 months, emitting as much as 7.8 Gbps of CLDAP site visitors.