Fixing oblique vulnerabilities is a kind of advanced, tedious and, fairly frankly, boring duties that nobody actually desires to the touch. Nobody aside from Debricked, it appears. Certain, there are many methods to do it manually, however can or not it’s achieved robotically with minimal danger of breaking modifications? The Debricked workforce determined to search out out.
A forest filled with fragile bushes
So, the place do you even begin?
Firstly, there must be a option to repair the vulnerability, which, for oblique dependencies, isn’t any stroll within the park. Secondly, it must be achieved in a secure approach, or, with out something breaking.
You see, oblique dependencies are launched deep down the dependency tree and it is very tough to get to the precise model you need. As Debricked’s Head of R&D as soon as put it, “You’re turning the knobs by enjoying round together with your direct dependencies and praying to Torvalds that the right oblique packages are resolved. When Torvalds is in your favour, it’s a must to sacrifice some cloud storage to uncle Bob to ensure the updates do not break your utility.”
In different phrases, there actually needs to be a neater, much less anxious, option to do it.
On this article, we’ll stroll you thru how fixing transitive vulnerabilities could be achieved manually and, in the direction of the top, present you the Debricked answer, which lets you do it robotically. Should you’re actually simply within the answer, I counsel you begin scrolling.
Precision surgical procedure in your dependency tree
Throughout the analysis section of the graph-database undertaking, or, how Debricked at present fixes your open supply vulnerabilities on the velocity of sunshine, the workforce stumbled upon some articles explaining the way to repair oblique vulnerabilities in NPM.
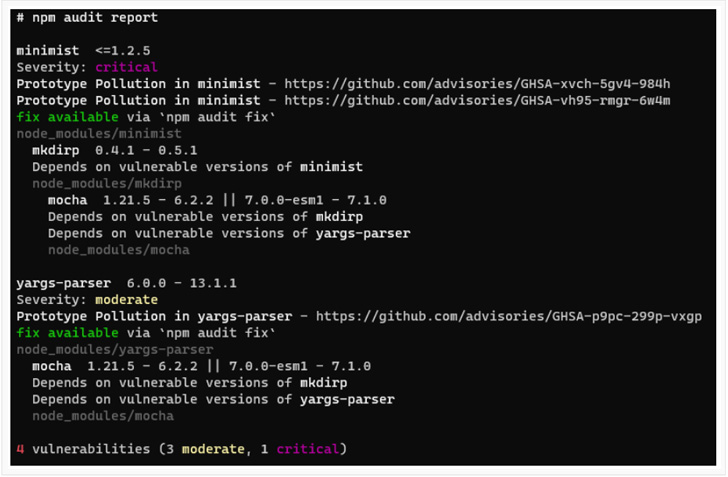
As acknowledged within the article, the `minimist` package deal is affected by vulnerabilities, specifically CVE-2021-44906 and CVE-2020-7598.
These are each “Prototype Air pollution” vulnerabilities, which means that arguments are usually not correctly sanitized. Fortunately, the maintainers of `minimist` mounted these vulnerabilities in model 1.2.6.
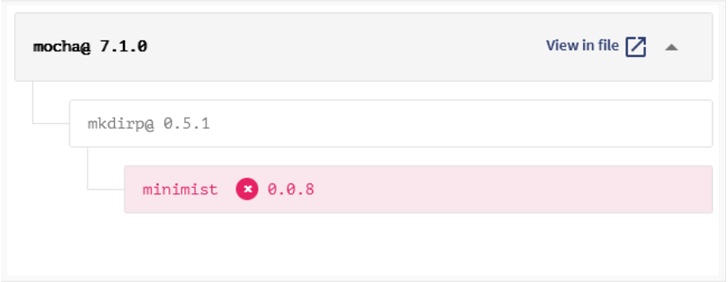
Sadly, `mocha` model 7.1.0 resolves `minimist` 0.0.8, which is throughout the weak vary of those vulnerabilities. As recommended by the writer of this text, these vulnerabilities could be mounted in a number of other ways.
However! What about breaking modifications?
The primary suggestion is to easily set off an replace of all “oblique dependencies”, which means that we cannot really change the model of `mocha`. To carry out this replace, merely run `npm replace`, delete your `npm.lock` file, and run `npm set up`. This regenerates the dependency tree with the newest potential model (in keeping with constraints) of your oblique dependencies. With this methodology, the chance of breaking modifications may be very low as you really do not replace any of your root dependencies, simply your oblique ones.
Breaking modifications happen when the package deal performance or interface is just not ahead appropriate, which means that an replace to the package deal may trigger your utility to interrupt. Frequent breaking modifications are class/function-removal, change of arguments to a perform, or licence-change (be careful for that one!).
However life is just not all the time this simple, and this easy replace of the tree won’t clear up the vulnerability. The issue is that `mkdirp` has really locked their model of `minimist` to 0.0.8. Because of this the contributors of `mkdirp` have come to the conclusion that they don’t seem to be appropriate with newer variations of `minimist`, and forcing the replace of `minimist` might introduce breaking modifications between `mkdirp` and `minimist`.
Assume… graphs!
So, the million-dollar query is: what model of `mocha` needs to be used, that in flip trickles right down to a secure model of `minimist` with out breaking the dependency tree? That is really a graph drawback, which has been described in this text.
What graph algorithm would clear up this drawback? How NPM resolves dependencies could be a bit difficult, as they’re allowed to “cut up” the dependency tree. Because of this they will have a number of variations of 1 dependency to make it possible for we all the time have a tree that’s appropriate. To unravel the vulnerability, we have to make it possible for all situations of `minimist` are secure by updating all roots that may trickle right down to `minimist`.
The algorithm used to resolve this drawback known as “All Max Paths Secure”. By strolling down the dependency graph and protecting the max variations, all whereas pruning all different variations of that package deal in every intersection, we will create an approximate illustration of our dependency tree. If the approximation is secure, that signifies that our actual tree shall be secure as properly!
By performing this algorithm for all potential variations of `mocha`, we discover the smallest improve to repair this vulnerability. To get the velocity we wished for this algorithm, the workforce needed to construct a customized Neo4j process, which may deal with looking over 100 root variations with a search depth of 30+ in ~150 milliseconds. Speedy, huh?
On this case, we do not have to look very far… as 7.1.1 of `mocha` is secure! That is solely a patch replace, which signifies that the chance of breaking modifications may be very low. For much less advanced instances (like this instance), ‘npm audit’ might help you with their improbable ‘npm audit repair’ command.
Do not be ad-hoc, enter the pub-sub-human approach of working!
Now, if you happen to acquired this far (congratulations, very spectacular) and thought, “this sounds actually advanced and like an terrible lot of labor,” don’t be concerned – you are not the one one. Fortunately, all this occurs utterly robotically within the Debricked instrument when clicking this little button:
As of proper now, that is obtainable for Javascript. Quickly, the help shall be prolonged to Java, Golang, C#, Python and PHP.
Should you’re not but a Debricked person, what are you ready for? It is free for single devs, smaller groups and open supply tasks (and if you happen to’re a bigger group, concern not. There is a beneficiant free trial). Join free right here.