With the explosive progress of internet purposes because the early 2000s, web-based assaults have progressively change into extra rampant. One frequent answer is the Net Software Firewall (WAF). Nonetheless, tweaking guidelines of present WAFs to enhance the detection mechanisms might be complicated and troublesome. NGWAF seeks to handle these drawbacks with a novel machine studying and quarantine-to-honeypot based mostly structure.
Impressed by precise ache factors from working WAFs, NGWAF intends to simplify and reimagine WAF operations by means of the next processes:
| Ache level | NGWAF Characteristic |
|---|---|
| Upkeep of detection mechanisms and guidelines might be complicated | Leverage machine studying to automate the method of making and updating detection mechanisms |
| Instant blocking of malicious visitors reduces probabilities of studying from menace actor habits for future WAF enhancements | Risk elimination by means of redirected quarantine versus typical dropping and blocking of malicious visitors |
To make deployment easy and transportable, we’ve got containerised the completely different elements within the structure utilizing docker and configured them in a docker-compose file. This enables operating it on a recent set up to be fast and simple because the dependencies are dealt with by docker mechanically. The deployment might be expanded to be deployed into a neighborhood or cloud supplier based mostly kubernetes cluster, making scalabe as customers can enhance the variety of nodes/pods to deal with massive quantities of visitors.
The deployment have been examined on macOS (Docker desktop), linux (ubuntu).
Take a look at our demo video right here
NGWAF is created by @yupengfei, @zhangbosen, @matthewng and @elizabethlim
Particular shoutout to @ruinahkoh for her contributions to the preliminary levels of NGWAF.
How does NGWAF work?
NGWAF runs out-of-the-box with three key elements, these elements as talked about above are all containerised and are scalable in accordance with desired utilization. The protected useful resource might be customised by making a deployment change throughout the setup.
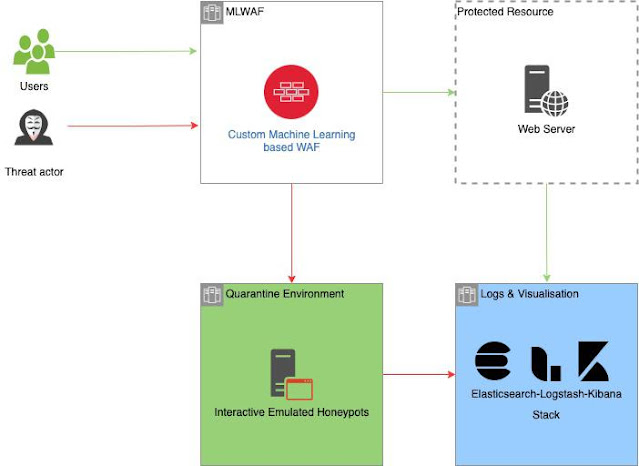
Excessive degree structure of NGWAF with anticipated visitors flows from completely different events
Key Advantages
NGWAF was engineered with the next key person advantages in thoughts:
1. Rule Complexity Discount
NGWAF replaces conventional rulesets with deep studying fashions to scale back the complexity of managing and updating guidelines. As an alternative of manually editting guidelines, NGWAF’s machine studying automates the sample studying course of from malicious knowledge. Knowledge collected from the quarantine setting are mechanically scrubbed and batched, permitting it to be retrained into our detection mannequin if desired.
2. Cyber Deception
NGWAF adopts a novel structure consisting an interactive and quarantine setting constructed to isolate potential hostile attackers. In contrast to typical WAFs which blocks upon detection, NGWAF diverts menace actors to emulated programs, trapping them to melt the impression of their malicious actions. The setting additionally act as a sinkhole to assemble present assault strategies, enabling the commentary and assortment of malicious knowledge. These knowledge can be utilized to additional enhance NGWAF’s detection functionality.
NGWAF in motion: Upon detection of SQL injection, NGWAF redirects to our quarantine setting, as a substitute of dropping or blocking the try.
3. Compliance to Internationally Recognised Requirements
The guiding principal behind the creation of NGWAF is to protect in opposition to the dangers highlighted from the Open Net Software Safety Challenge’s normal consciousness doc – The OWASP High 10 2021.
Coaching knowledge and compliance checks for NGWAF are collected and carried out based mostly on this requirement.
1. The Brains – Machine-Studying based mostly WAF | Who wants guide after we can go NEURAL
As an alternative of conventional rulesets which require analysts to manually establish and add guidelines as time goes by, NGWAF leverages end-to-end machine studying pipelines for the detection mechanism, tremendously lowering the complexity in WAF rule administration, particularly for detecting complicated payloads.
Base Mannequin
To take action, we wanted to first create a base mannequin and structure that customers can begin off with, earlier than they later use knowledge collected from their very own purposes for retraining and fine-tuning:
- We collected malicious and non-malicious payloads from numerous utility logs (whole of ~40k observations)
- As an alternative of manually figuring out guidelines, we leverage machine and deep studying to automate the method of studying patterns from earlier malicious knowledge.
- We then experimented with a number of mannequin architectures, and our closing mannequin utilized a sequential neural community to foretell whether or not an incoming payload was malicious or not.
Efficiency
Our mannequin was capable of obtain 99.6% accuracy on our coaching dataset.
Upkeep & Retraining
Though we’ve got included logs from numerous purposes with a view to enhance the generalizability of the bottom mannequin, additional upkeep and retraining of the mannequin will probably be vital to:
- Tune the mannequin for higher efficiency on visitors from the person’s particular utility
- Cut back mannequin degradation over time, as menace actors uncover new strategies and alternatives
To handle this, customers of NGWAF profit from our packaged end-to-end mannequin retaining pipeline, and might simply set off mannequin upkeep with a couple of easy steps with out having to dig underneath the hood. (See Part 3 beneath).
2. The Wanting Glass – Scalable Interactive Quarantine Surroundings | Do not allow them to go, DETAIN THEM!
Opposite to conventional WAFs the place malicious visitors are blocked or dropped instantly. NGWAF goes with a extra versatile strategy. Whereby, it redirects and detains malicious actors inside a quarantine setting. This setting consists of varied interactive emulated honeypots to attempt to collect extra assault strategies/knowledge, these knowledge will probably be utilised to doubtlessly improve NGWAF’s detection price of extra fashionable and sophisticated assaults.
Capturing of Malicious knowledge and Auto-Scrubbing for retraining functions
At the moment, NGWAF’s quarantine setting forwards all knowledge submitted by the trapped attacker to our ELK stack for evaluation and visualisation. The information are auto-scrubbed into completely different elements of the HTTP request, then packaged internally on the setting’s backend in JSON format earlier than forwarding. This helps to decrease the manpower price required to scrub and index the information after we kickstart the retraining course of.
Creating your customised quarantine setting
NGWAF at present supplies customers to make modifications to the appear and feel of the front-end side of our honeypots throughout the quarantine setting (based mostly off a personalized model of drupot). Customers merely have to switch the property folder throughout the docker quantity with their front-end property of selection.
NGWAF can also be accommodating to customers who want to hyperlink their very own honeypots as a part of the quarantine setting. Customers simply must ahead the honeypot’s HTTP requests to the setting’s backend server (backend processes will mechanically scrub and ahead knowledge to the evaluation dashboard – ELK stack).
3. The Library – Retraining Sequence to Reinforce the Brains | Sensible is not actually good until you may continue to learn.
As new payloads and assault vectors emerge, it is very important improve detection capabilities with a view to guarantee safety. Therefore, a retraining operate is constructed into NGWAF to make sure defenders are capable of practice the machine studying mannequin to detect these newer payloads.
Retraining of datasets is among the foremost options in NGWAF. On our dashboard, customers can insert new dataset for retraining, to strengthen and enhance the standard of NGWAF detection of malicious payloads.
This may be achieved within the following steps:
-
Create a brand new dataset (.csv) for add within the following format (empty column, coaching knowledge, label). You possibly can seek advice from
patch_sqli.csvfor example. -
Navigate to
http://localhost:8088to view NGWAF admin panel. -
Choose the “Import Dataset” tab and add the coaching set you’ve got created
- Affirm that the coaching set have been uploaded efficiently underneath the “Handle Datasets” tab.
- Beneath “Handle Mannequin” tab, choose the dataset(s) you need to retrain the mannequin on and click on on the “UPDATE WAF MODEL” button.
- Congrats! The mannequin ought to end re-training after a while.
4. Further Options:
NGWAF makes use of ELK stack to seize logs of community knowledge that passes by means of NGWAF, permitting customers to watch the visitors that passes by means of the NGWAF for additional evaluation.
NGWAF additionally comes with reside Telegram notification, to tell homeowners about reside malicious threats that’s detected by NGWAF.
Pattern Utilization Eventualities
- Newly regular utility (Use the inbuilt internet cloner / create one other duplicate deployment to make use of as isolation setting)
- Combine into current honeypot/honeynet (Replace the configuration to level to honeypot/honeynet)
Organising NGWAF | Necessities, set up, and utilization
Necessities
Examined Working Programs
- macOS (Docker Desktop)
- linux
WAF Part
- Python
- request
- fastapi
- pandas
- scikit-learn
- tensorflow (tentative)
- nltk
WAF Admin Panel Part
- fastapi
- scikit-learn
- nltk
- pandas
- Create React App
- React Materials Admin Template by Flatlogic
Decode Layer
Caching Layer
- Redis
Quarantine Surroundings
- Drupot
- Elastic Search Stack Elements (Elasticsearch, Logstash, Kibana, Filebeats)
Net App
Set up and Utilization
With Docker operating, run the next file utilizing the command beneath:
./run.sh
To switch the targets, level the dest_server and honey_pot_server variable to the right targets within the /waf/WafApp/waf.py file
# Change me
dest_server = "dvwa"
honey_pot_server = "drupot:5000"As soon as the Docker container is up, you may go to your localhost, through which these ports are operating these companies:
| Port | Service | Remarks | Credentials (If relevant) |
|---|---|---|---|
| 8080 | DVWA | The place the WAF resides | admin:password |
| 5601 | Elasticsearch | To view logs | elastic:changeme |
| 8088 | Admin Dashboard | Dashboard to handle the WAF mannequin | |
| 5001 | Drupot | Honeypot |
To permit for Telegram reside notifications, do change the next variables in /waf/WafApp/waf.py with a legitimate TELEGRAM tokens.
token='<INSERT VALID TELEGRAM BOT TOKEN>'
CHAT_ID = '<INSERT VALID CHAT_ID>'
WAF_NAME = 'Tester_WAF'
WARN_MSG = "ALERT [Security Incident] Malicious exercise detected on " +WAF_NAME+ ". Please alert related groups and examine by means of incident artifacts."
URL= "https://api.telegram.org/bot{}/sendMessage?chat_id={}&textual content={}".format(token,CHAT_ID,WARN_MSG)Disclaimers & Different Issues
NGWAF is a W.I.P, Open supply venture, capabilities and options might change from patch to patch. If you’re to contribute, please be at liberty to create a difficulty or pull request!
Licensing
License










