Linus Torvalds, the creator of Linux and Git, has his personal regulation in software program improvement, and it goes like this: “given sufficient eyeballs, all bugs are shallow.” This phrase places the finger on the very precept of open supply: the extra, the merrier – if the code is definitely out there for anybody and everybody to repair bugs, it is fairly secure. However is it? Or is the saying “all bugs are shallow” solely true for shallow bugs and never ones that lie deeper? It seems that safety flaws in open supply may be tougher to seek out than we thought. Emil Wåreus, Head of R&D at Debricked, took it upon himself to look deeper into the neighborhood’s efficiency. As the information scientist he’s, he, after all, requested the information: how good is the open supply neighborhood at discovering vulnerabilities in a well timed method?
The joys of the (vulnerability) hunt
Discovering open supply vulnerabilities is often completed by the maintainers of the open supply challenge, customers, auditors, or exterior safety researchers. However regardless of these nice code-archaeologists serving to safe our world, the neighborhood nonetheless struggles to seek out safety flaws.
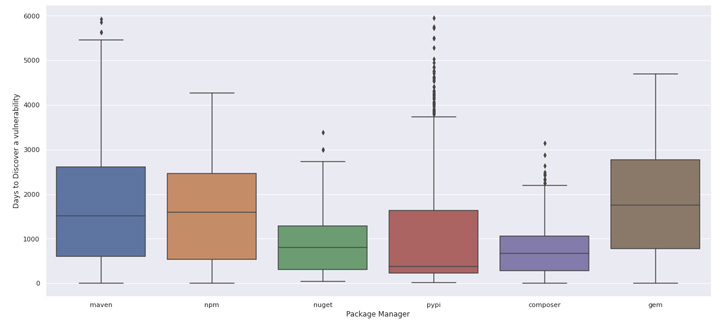
On common, it takes over 800 days to find a safety flaw in open supply initiatives. As an example, the notorious Log4shell (CVE-2021-44228) vulnerability was undiscovered for a whopping 2649 days.
The evaluation exhibits that 74% of safety flaws are literally undiscovered for a minimum of one 12 months! Java and Ruby appear to have essentially the most challenges right here, because it takes the neighborhood greater than 1000 days to seek out and disclose vulnerabilities. Our [white] hats go off to the PHP/Composer neighborhood, which barely outperforms the others.
The needle in a techstack
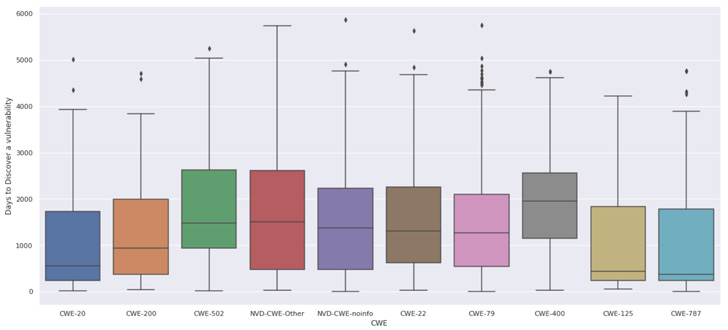
Different attention-grabbing elements are that a number of the completely different weak point varieties (CWE) appear to be tougher to seek out and disclose, which really contradicts Linus’s regulation. The weak point varieties CWE-400 (Uncontrolled Useful resource Consumption) and CWE-502 (Deserialization of Untrusted Knowledge) usually aren’t localized to a single perform or could seem as meant logic within the utility. In different phrases, it might probably’t be thought of “a shallow bug.”
It additionally appears that the developer neighborhood is a bit higher at discovering CWE-20 (Improper Enter Validation), the place the flaw more often than not is just some strains of code in a single perform.
Clear up vulnerabilities with highly effective remediation
Why does this matter? As shoppers of open supply, and that is about each firm in the entire world, the issue of vulnerabilities in open supply is a crucial one. The info tells us that we won’t absolutely belief Linus’ Regulation – not as a result of open supply is much less safe than different software program, however as a result of not all bugs are shallow.
Fortunately, there are highly effective instruments to carry out at-scale evaluation of a variety of open supply initiatives without delay. There have been [white knight hackers disclose 1000’s] of vulnerabilities without delay utilizing these strategies. It could be naive to not assume that ill-minded organizations and people do the identical. As an ecosystem that lays the inspiration for our software-centric world, the neighborhood should enhance its potential to seek out, disclose, and repair safety flaws in open supply considerably.
Final 12 months, Google dedicated $10 billion to an open supply fund to assist safe open supply with a particular curator function to work alongside the maintainers with particular safety efforts.
Moreover, Debricked helps firms make these vulnerabilities actionable by scanning all of your software program, each department, each push, and each commit, for brand spanking new (open supply) vulnerabilities. Debricked even constantly scans all of your previous commits for each new vulnerability, to verify they bring about up-to-date, correct, and actionable intelligence on the open supply you devour. Debricked even helps builders repair your safety flaws with automated pull requests that will not trigger dependency hell; fairly neat!
The reality lies within the knowledge
So, figuring out all this, what’s the easiest way to guard your challenge or firm towards open supply vulnerabilities? As we have seen within the case of Log4j and Spring4shell in addition to the numbers, we will by no means actually belief that the neighborhood will discover and repair all dangers. There is a good probability that there are tons and plenty of undiscovered and undisclosed vulnerabilities in your code in the present day, and there is not a lot you are able to do about it.
In accordance with Debricked, the easiest way to mitigate that is by implementing steady vulnerability scanning to your SDLC. By mechanically scanning at each push of code, together with the machine learning-powered vulnerability database. This makes certain you are up to date in real-time, you will learn about new vulnerabilities earlier than anybody else does. As quickly as there is a repair, you possibly can generate a Repair Pull Request mechanically or remedy it manually with Debricked’s assist. At the moment, Debricked presents remediation for JavaScript and Go, with extra language assist is to come back shortly.