An exhaustive evaluation of FIN7 has unmasked the cybercrime syndicate’s organizational hierarchy, alongside unraveling its position as an affiliate for mounting ransomware assaults.
It has additionally uncovered deeper associations between the group and the bigger menace ecosystem comprising the now-defunct ransomware DarkSide, REvil, and LockBit households.
The extremely energetic menace group, also called Carbanak, is recognized for using an in depth arsenal of instruments and techniques to increase its “cybercrime horizons,” together with including ransomware to its playbook and organising pretend safety firms to lure researchers into conducting ransomware assaults underneath the guise of penetration testing.
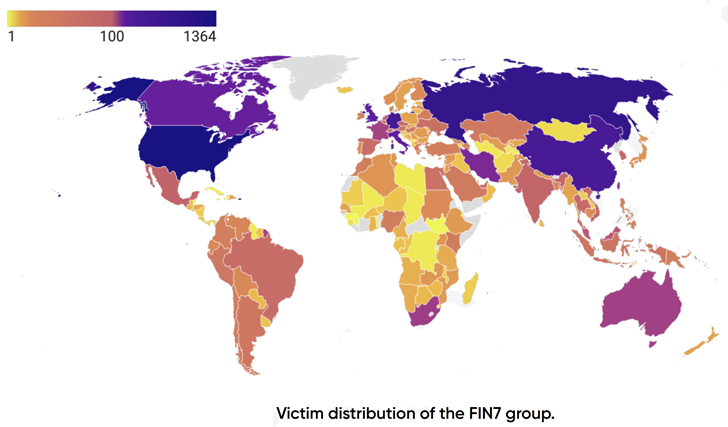
Greater than 8,147 victims have been compromised by the financially motivated adversary the world over, with a majority of the entities situated within the U.S. Different outstanding international locations embrace China, Germany, Canada, Italy, and the U.Ok.
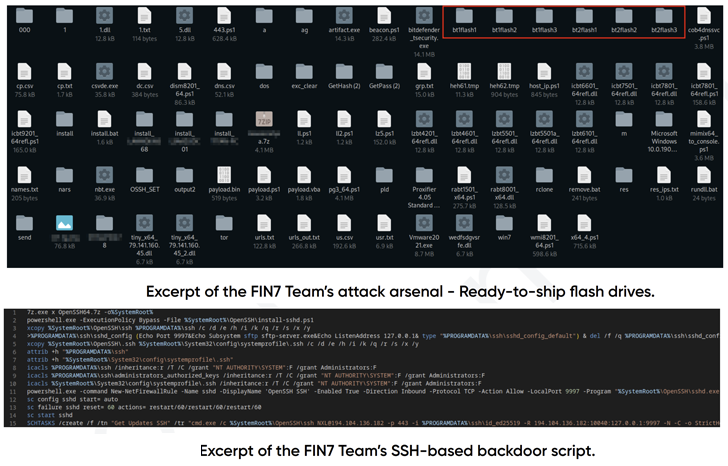
FIN7’s intrusion strategies, over time, have additional diversified past conventional social engineering to incorporate contaminated USB drives, software program provide chain compromise and the usage of stolen credentials bought from underground markets.
“These days, its preliminary method is to rigorously decide high-value firms from the pool of already compromised enterprise techniques and pressure them to pay massive ransoms to revive their knowledge or search distinctive methods to monetize the information and distant entry,” PRODAFT stated in a report shared with The Hacker Information.
In response to the Swiss cybersecurity firm, the menace actors have additionally been noticed to weaponize flaws in Microsoft Alternate comparable to CVE-2020-0688, CVE-2021-42321, ProxyLogon, and ProxyShell flaws in Microsoft Alternate Server to acquire a foothold into goal environments.
Using double extortion techniques however, assaults mounted by the group have deployed backdoors on the compromised techniques, even in eventualities the place the sufferer has already paid a ransom.
The thought is to resell entry to different ransomware outfits and re-target the victims as a part of its illicit money-making scheme, underscoring its makes an attempt to reduce efforts and maximize earnings, to not point out prioritize firms primarily based on their annual revenues, based dates, and the variety of staff.
This “demonstrates a specific kind of feasibility examine thought of a singular habits amongst cybercrime teams,” the researchers stated.
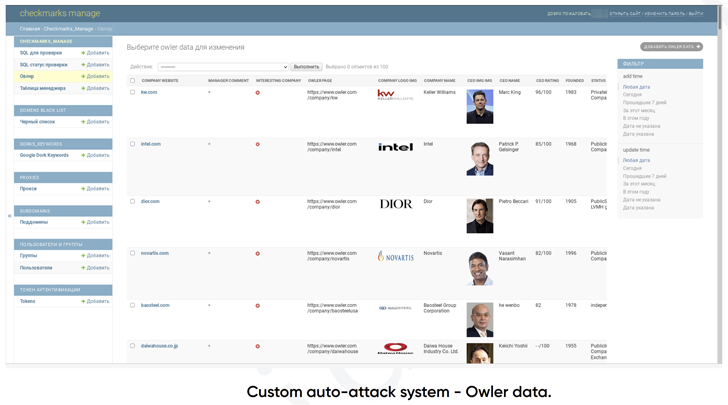
Put in a different way, the modus operandi of FIN7 boils all the way down to this: It makes use of companies like Dun & Bradstreet (DNB), Crunchbase, Owler, and Zoominfo to shortlist companies and organizations with the very best income. It additionally makes use of different web site analytics platforms like MuStat and Similarweb to observe site visitors to the victims’ websites.
Preliminary entry is then obtained via one of many many intrusion vectors, adopted by exfiltrating knowledge, encrypting recordsdata, and finally figuring out the ransom quantity primarily based on the corporate’s income.
These an infection sequences are additionally designed to load the distant entry trojans comparable to Carbanak, Lizar (aka Tirion), and IceBot, the latter of which was first documented by Recorded Future-owned Gemini Advisory in January 2022.
Different instruments developed by FIN7 embody modules to automate scans for weak Microsoft Alternate servers and different public-facing internet purposes in addition to Cobalt Strike for post-exploitation.
In one more indication that felony teams operate like conventional firms, FIN7 follows a workforce construction consisting of top-level administration, builders, pentesters, associates, and advertising groups, every of whom are tasked with particular person tasks.
Whereas two members named Alex and Rash are the chief gamers behind the operation, a 3rd managerial member named Sergey-Oleg is liable for delegating duties to the group’s different associates and overseeing their execution.
Nevertheless, it has additionally been noticed that operators in administrator positions interact in coercion and blackmail to intimidate workforce members into working extra and subject ultimatums to “harm their relations in case of resigning or escaping from tasks.”
The findings come greater than a month after cybersecurity firm SentinelOne recognized potential hyperlinks between FIN7 and the Black Basta ransomware operation.
“FIN7 has established itself as a very versatile and well-known APT group that targets enterprise firms,” PRODAFT concluded.
“Their signature transfer is to totally analysis the businesses primarily based on their income, worker rely, headquarters and web site data to pinpoint essentially the most worthwhile targets. Though they’ve inside points associated to the unequal distribution of obtained financial assets and considerably questionable practices in the direction of their members, they’ve managed to determine a robust presence within the cybercrime sphere.”