A artistic mixture of phishing emails, stable social engineering, use of Fb Messenger, model and web site impersonation, and a way of urgency all add as much as a plausible assault.
A artistic mixture of phishing emails, stable social engineering, use of Fb Messenger, model and web site impersonation, and a way of urgency all add as much as a plausible assault.
Most phishing scams take customers via a sequence of hoops to leap via to keep away from detection – a lot so, that the hoops themselves ought to function a crimson flag. However within the case of a new Fb-themed phishing assault documented by safety vendor Trustwave, the steps taken are probably so unfamiliar to the sufferer, that they are going to be thrown off fully and can merely observe the steps… to surrender their Fb credentials.
The rip-off begins with a easy sufficient e mail from “Fb” stating “your web page has been scheduled for deletion for violating our Neighborhood Requirements.” The “Enchantment Now” name to motion takes customers to a Messenger dialog with a chatbot below the title of “Web page Help”.

Supply: Trustwave
The chatbot “requires” that the person be logged onto Fb, prompting the person to go online. Throughout the chat is a chance to enchantment the web page deletion which takes the person to a Fb-branded (however impersonated) “Help Inbox”.

Supply: Trustwave
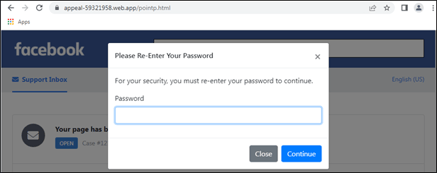
The preliminary “enchantment” type requested for login, title, and cellphone quantity. However the sneaky step is how they ask for the password. Have a look – I discover this to be plausible sufficient to idiot those who aren’t tech-savvy:
Supply: Trustwave
For the reason that person has already skilled logging onto Fb throughout this rip-off, this step feels prefer it’s professional. There’s even a pretend one-time password request despatched to the cell phone quantity provided to make this appear professional.
What makes this rip-off scary is that it could actually simply as simply be pretending to be your group’s occasion of Salesforce, Microsoft 365, or every other vital SaaS software. Customers want to pay attention to such assaults through Safety Consciousness Coaching so that they don’t fall for the preliminary e mail within the first place, nullifying all of the social engineering effort within the assault that may, little doubt, set up some credibility and acquire the attackers some victims.