An Android voice phishing (aka vishing) malware marketing campaign often known as FakeCalls has reared its head as soon as once more to focus on South Korean customers below the guise of over 20 in style monetary apps.
“FakeCalls malware possesses the performance of a Swiss military knife, ready not solely to conduct its major goal but additionally to extract personal knowledge from the sufferer’s machine,” cybersecurity agency Verify Level stated.
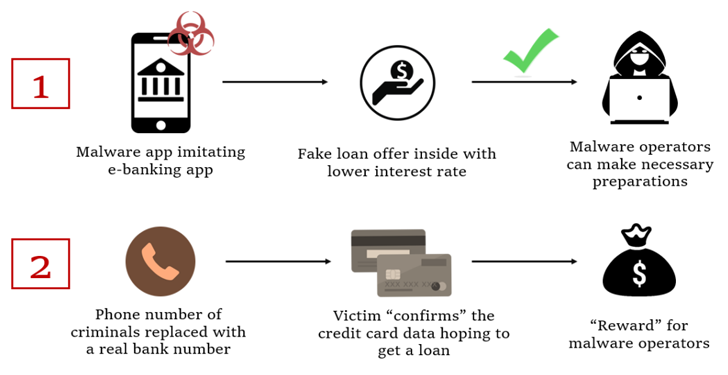
FakeCalls was beforehand documented by Kaspersky in April 2022, describing the malware’s capabilities to mimic telephone conversations with a financial institution buyer assist agent.
Within the noticed assaults, customers who set up the rogue banking app are enticed into calling the monetary establishment by providing a faux low-interest mortgage.
On the level the place the telephone name really occurs, a pre-recorded audio with directions from the true financial institution is performed. On the similar time, malware additionally conceals the telephone quantity with the financial institution’s actual quantity to present the impression {that a} dialog is occurring with an precise financial institution worker on the opposite finish.
The last word purpose of the marketing campaign to get the sufferer’s bank card info, which the risk actors declare is required to qualify for the non-existent mortgage.
The malicious app additionally requests for intrusive permissions in order to reap delicate knowledge, together with dwell audio and video streams, from the compromised machine, that are then exfiltrated to a distant server.
The newest FakeCalls samples additional implement varied strategies to remain below the radar. One of many strategies entails including a lot of recordsdata inside nested directories to the APK’s asset folder, inflicting the size of the file title and path to breach the 300-character restrict.
“The malware builders took particular care with the technical facets of their creation in addition to implementing a number of distinctive and efficient anti-analysis strategies,” Verify Level stated. “As well as, they devised mechanisms for disguised decision of the command-and-control servers behind the operations.”
Whereas the assault completely focuses on South Korea, the cybersecurity firm has warned that the identical ways might be repurposed to focus on different areas the world over.
The findings additionally come as Cyble make clear two Android banking trojans dubbed Nexus and GoatRAT that may harvest beneficial knowledge and perform monetary fraud.
Nexus, a rebranded model of SOVA, additionally incorporates a ransomware module that encrypts the saved recordsdata and might abuse Android’s accessibility providers to extract seed phrases from cryptocurrency wallets.
Uncover the Hidden Risks of Third-Social gathering SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to study in regards to the varieties of permissions being granted and how one can reduce danger.
In distinction, GoatRAT is designed to focus on Brazilian banks and joins the likes of BrasDex and PixPirate to commit fraudulent cash switch over the PIX funds platform whereas displaying a faux overlay window to cover the exercise.
The event is a part of a rising development the place risk actors have unleashed more and more subtle banking malware to automate the entire means of unauthorized cash transfers on contaminated units.
Cybersecurity firm Kaspersky stated it detected 196,476 new cell banking trojans and 10,543 new cell ransomware trojans in 2022, with China, Syria, Iran, Yemen, and Iraq rising as the highest nations attacked by cell malware, together with adware.
Spain, Saudi Arabia, Australia, Turkey, China, Switzerland, Japan, Colombia, Italy, and India lead the checklist of prime nations contaminated by cell monetary threats.
“Regardless of the decline in general malware installers, the continued progress of cell banking Trojans is a transparent indication that cybercriminals are specializing in monetary acquire,” Kaspersky researcher Tatyana Shishkova stated.